“Sekhmet” Ransomware Removal Guide (Effective Instructions)
Maria R.
Issue:Help! My computer was encrypted with ransomware called 'sekhmet'. Any advice how to fix it?
Hello,
my PC has been recently infected and files encrypted with Sekhmet ransomware. I have no idea what to do and how to remove it.
Please help me. Thank you!
The Sekhmet Ransomware is a crypto-malware that encrypts all the files in the infected machine and restricts the users from using them as normal. It mainly targets organizations and then threatens them that they will divulge confidential information to the public if the victim does not agree to their demands.

The Sekhmet ransomware was first detected by cybersecurity experts back in March of 2020. Just like any other malware, the Sekhmet ransomware uses a combination of both ChaCha and RSA encryption algorithm. Once the computer is infected, it will encrypt files such as documents, videos, music and other executable programs making it unusable unless the victim pays the ransom amount through Bitcoin. This ransomware is developed by Maze Ransomware and is already being emulated by other strains of the ransomware.
Threat Summary
| Threat Name | Sekhmet Ransomware |
| Type of Threat | Crypto-malware, file encryption |
| Encryption Type | A combination of ChaCha and RSA-2048 |
| Ransom Note File | RECOVER-FILES.txt |
| Contact Details | sekhmet.top (using a TOR client) |
| Symptoms | Encrypts and locks files in the infected machine making it unusable, as per the developers of the ransomware they also harvest and sell sensitive information from the infected machine |
| Removal | Perform a full system scan while the machine is in Safe Mode with Networking using a reliable anti-malware tool such as iolo System Mechanic. |
The attack vectors of Sekhmet ransomware do not perform random attacks of regular internet users as they mainly target organizations. To perform these attacks, the cyber criminals behind the malware spreads their infection through insecure Remote Desktop connections and spear-phishing emails. For insecure Remote Desktop connections, Sekhmet ransomware can easily make its way to the system if they are still using the default TCP/UDP port 3389.
Several anti-virus tools have already updated their virus definitions and depending on what you use, they may come up under several names. Here are their names according to several anti-virus tools:
- Trojan.GenericKD.42872192 (B)
- Trojan-Ransom.Win32.Cryptor.ddu
- Trojan.GenericKD.42872102
- Wind32:Malware-gen
- Win32.Trojan.Cryptor.Pgwr
- Ransom.Win32.SEKHMET.A
What Happens When You Get Infected with Sekhmet Ransomware?
Once a computer is infected with Sekhmet Ransomware, it will start to make unnoticeable changes on the machine. It will start with modifying some entries in the registry, establish remote server connections, invite and install additional malicious files, delete files and change some startup settings. Once all of these processes are complete, it will start encrypting files on the machine and appending their file extensions to make them unusable.
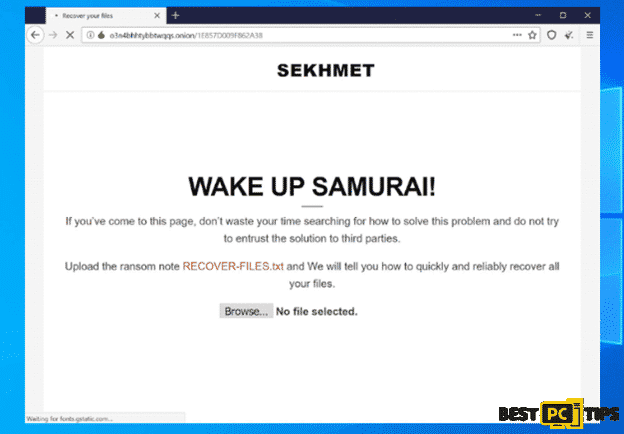
Once the encryption is complete, the developers of Sekhmet ransomware makes sure that they let the victim know that they do have the option to recover their files, and that option is to pay them through bitcoin. Here’s the message left in the ransom note:
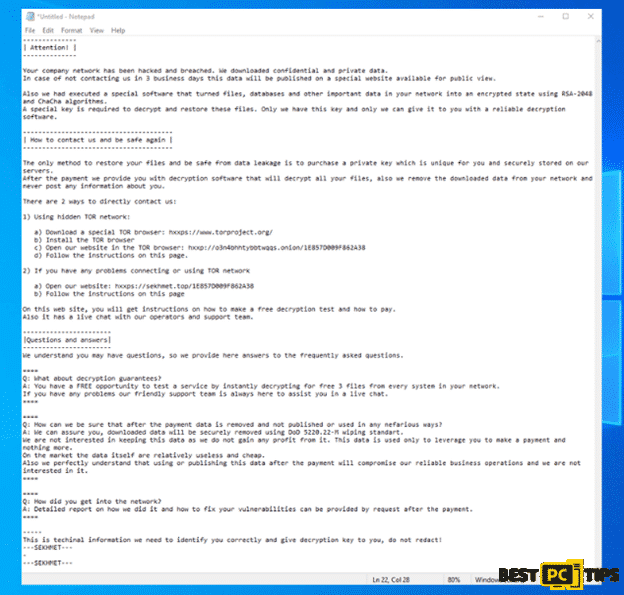
————–
| Attention! |
————–
Your company network has been hacked and breached. We downloaded confidential and private data.
In case of not contacting us in 3 business days this data will be published on a special website available for public view.
Also we had executed a special software that turned files, databases and other important data in your network into an encrypted state using RSA-2048 and ChaCha algorithms.
A special key is required to decrypt and restore these files. Only we have this key and only we can give it to you with a reliable decryption software.
—————————————
| How to contact us and be safe again |
—————————————
The only method to restore your files and be safe from data leakage is to purchase a private key which is unique for you and securely stored on our servers.
After the payment we provide you with decryption software that will decrypt all your files, also we remove the downloaded data from your network and never post any information about you.
There are 2 ways to directly contact us:
1) Using hidden TOR network:
a) Download a special TOR browser: hxxps://www.torproject.org/
b) Install the TOR browser
c) Open our website in the TOR browser: hxxp://o3n4bhhtybbtwqqs.onion/1E857D009F862A38
d) Follow the instructions on this page.
2) If you have any problems connecting or using TOR network
a) Open our website: hxxps://sekhmet.top/1E857D009F862A38
b) Follow the instructions on this page
On this web site, you will get instructions on how to make a free decryption test and how to pay.
Also it has a live chat with our operators and support team.
———————–
|Questions and answers|
———————–
We understand you may have questions, so we provide here answers to the frequently asked questions.
====
Q: What about decryption guarantees?
A: You have a FREE opportunity to test a service by instantly decrypting for free 3 files from every system in your network.
If you have any problems our friendly support team is always here to assist you in a live chat.
====
====
Q: How can we be sure that after the payment data is removed and not published or used in any nefarious ways?
A: We can assure you, downloaded data will be securely removed using DoD 5220.22-M wiping standart.
We are not interested in keeping this data as we do not gain any profit from it. This data is used only to leverage you to make a payment and nothing more.
On the market the data itself are relatively useless and cheap.
Also we perfectly understand that using or publishing this data after the payment will compromise our reliable business operations and we are not interested in it.
====
====
Q: How did you get into the network?
A: Detailed report on how we did it and how to fix your vulnerabilities can be provided by request after the payment.
====
—–
This is techinal information we need to identify you correctly and give decryption key to you, do not redact!
—SEKHMET—
The cyber criminals behind the Sekhmet Ransomware is not yet determined but with the efforts used in spreading the ransomware and the technical aspect of it, they are sure to be determined and serious. Basing on their ransom note, it is clear that they are not new when it comes to making and distributing ransomwares.
Knowing that these kinds of ransomware are floating around the internet, cyber security experts strongly encourage all individuals especially business to employ a legitimate anti-ransomware software such as iolo System Mechanic. It is common knowledge between businesses that it could be devastating for businesses if confidential information is leaked.
How to Prevent Sekhmet or Any Other Ransomware Virus Infections?
Do Not Download from Suspicious Websites – Just like any other viruses and ransomware, we strongly suggest internet users downloading and installing files that are downloaded from unknown and suspicious sources. Before downloading anything, make sure to do quick research as to where you can download your preferred application legitimately.
Avoid Clicking Attachments from Unknown Senders – In today’s time, clicking an attachment is strongly discouraged especially if its from an unknown source as it may contain malicious links or applications that will trigger a series of problems for your machine.
Install a Reliable Anti-Malware Software – Installing a reliable anti-malware tool in your computer is the most important step that should be done by everyone who is using the internet. With a reliable anti-malware tool such as iolo System Mechanic, your computer will be safe from any online threats as it will automatically detect and remove threats from your computer and it will also keep your system files updated.
How to Remove Sekhmet Ransomware?
Although paying the cyber criminals that are behind the Sekhmet Ransomware may sound like an easy fix, we strongly discourage anyone in contacting them. Just like regular criminals, nobody should trust their likes as it is still not a guarantee that they will provide the victim with the decrypting tool after the payment has been made.
Instead, you can manually remove the virus from your computer by using a reliable anti-malware tool such as iolo System Mechanic. Just make sure you put your computer in Safe Mode with Networking so that unnecessary drivers are disabled while you are performing a full system scan.
Below are the steps on how you can manually remove Sekhmet Ransomware or any other ransomware from your machine:
Rebooting to Safe Mode with Networking:
For Windows XP/Windows 7/Windows Vista
- Click on the “Windows” or “Start” button located on the lower left corner of the Window’s Desktop and click on the little arrow right next to “Shutdown” and click on “Restart”
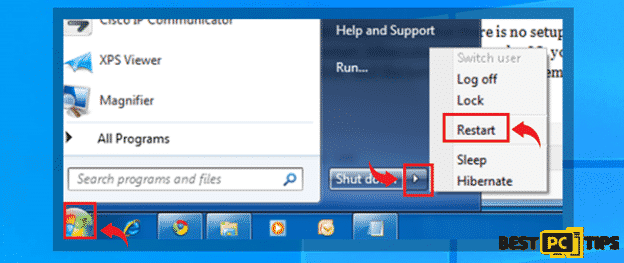
- Tap on the “F8” button on the keyboard once every second while the computer is booting back up until you see the “Advanced Boot Options”. Using the arrow keys on the keyboard, select “Safe Mode with Networking” and press “Enter” on your keyboard
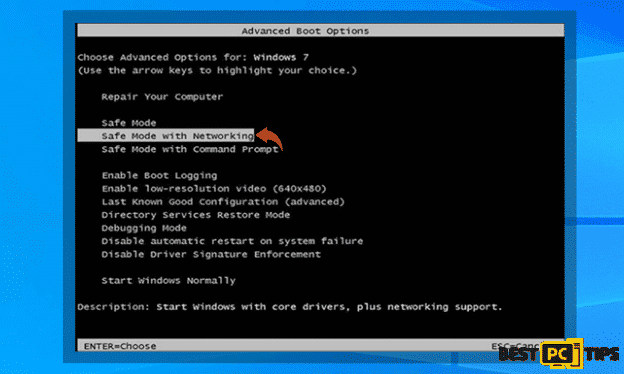
For Windows 10/Windows 8
- Click on the “Windows” button located on the lower left corner of the Window’s Desktop and hold down the “Shift” key on and click “Power” then “Restart”
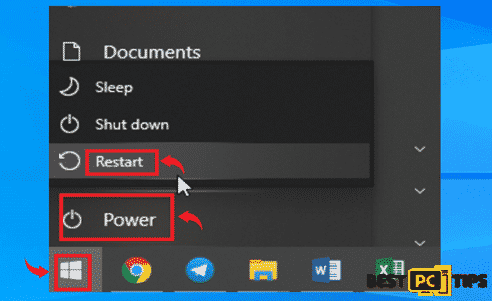
- In the Troubleshoot Screen, click the “Advanced Options”
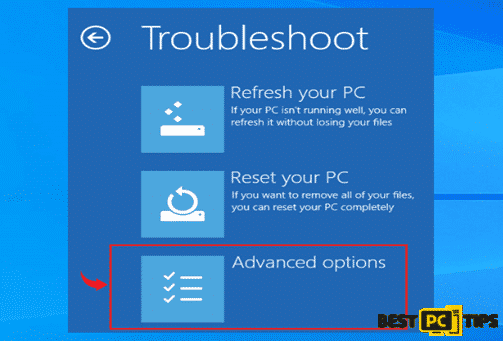
- In the Startup Settings, select the 5th option “Enable Safe Mode with Networking”
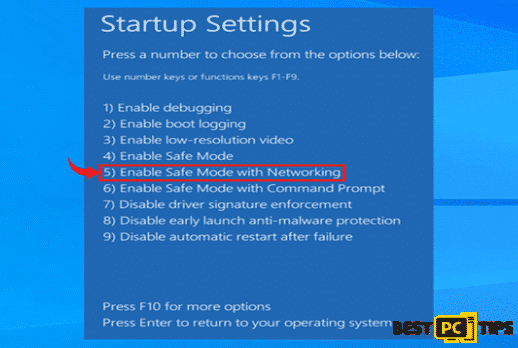
After entering the Safe Mode with Networking state on your machine, download and install your preferred anti-malware application. We suggest using an all-in-one tool that will not only keep your computer safe from viruses, but also one that will keep your machine updated to make it run at its optimal speed. You may use iolo System Mechanic as it uses a holistic approach in making sure your computer is virus free and updated all the time.
If for some reason you are not able to access Safe Mode with Networking, you may also use:
Windows full system restore through Safe Mode with Command Prompt. Simply follow the below steps:
For Windows XP/Windows 7/Windows Visa
- Click on the “Start” or “Windows” button found on the desktop and click the arrow next to the “Shutdown” and click “Restart”
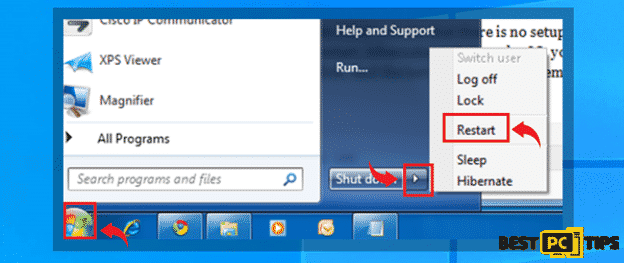
- Tap the “F8” key on the keyboard once per second while the computer is turning back on until you see the “Advanced Boot Options” on the screen and select “Safe Mode with Command Prompt” using the arrow keys and press enter
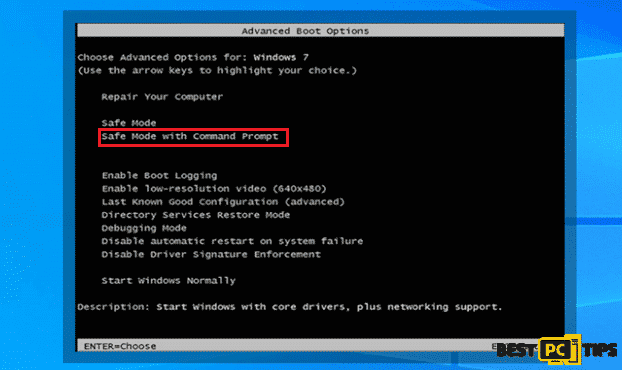
For Windows 10/Windows 8
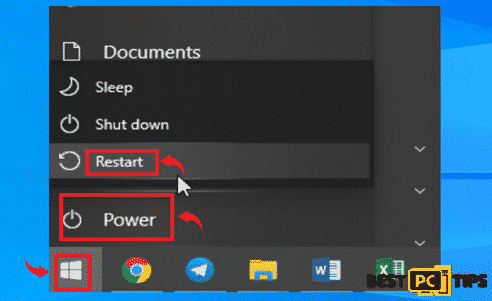
- Click on the “Windows” logo on the lower left corner of the desktop and hold down the “Shift” key on and click on the “Power” then click “Restart”
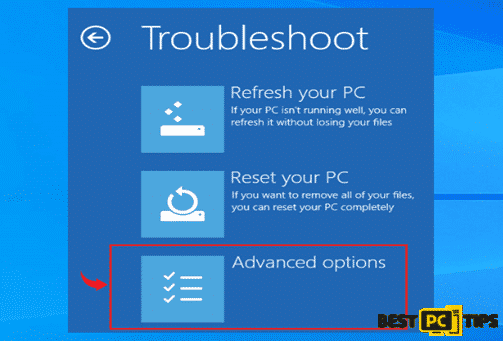
- Select the “Advanced Options” in the Troubleshoot screen
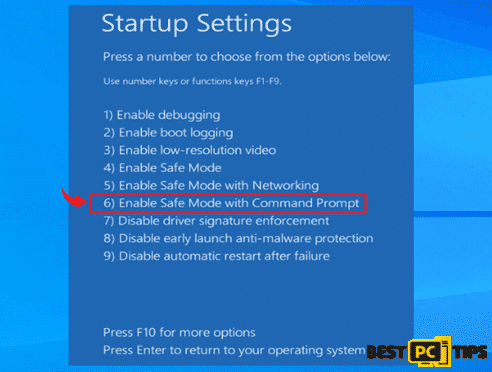
- Click on option 6 “Enable Safe Mode with Command Prompt”
Restoration Process
- Once the computer has been booted into Safe Mode with Command Prompt, type in “cd restore” in the command prompt and press enter. And type “rstrui.exe” and press enter again
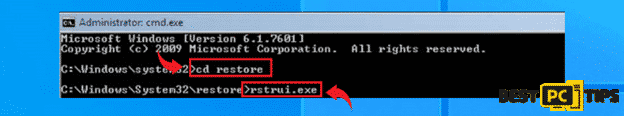
- On the next screen, select a restore point when the machine was working perfectly and click “Next”
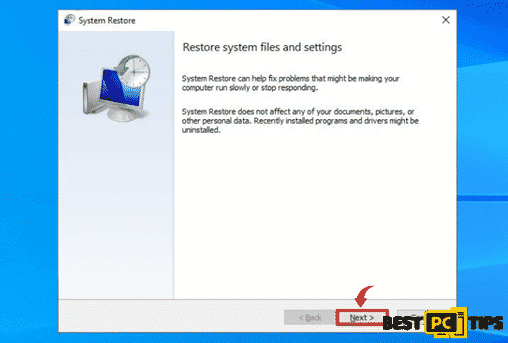
- Click “Yes” on the confirmation screen and let the restoration process complete without interruption
Additional Ransomware Removal/Restoration Methods
Use the Windows Previous Versions
Windows has a feature where you can restore infected files to a previously working files given that there is are available. Here are the steps:
- Select an encrypted file and right click on it
- Click on the “Properties” and then click on “Previous Versions”
- Under “File Versions” click the available copies and then click “Restore”
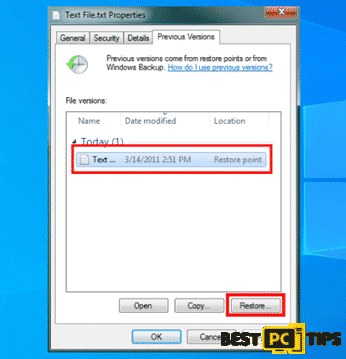
- After the restoration is complete, check the file to confirm if it has been restored.
Our Final Tips
To avoid disastrous data and files loss, we suggest for everyone to do a regular backup of their important files. You may back up your files to an external drive or to a cloud storage, it may be additional work but at least you are ready for any massive disaster such as a virus infection on a machine.
Offer
iolo System Mechanic® — is a patented PC & MAC repair tool & the only program of its kind. Not only it’s a registry fix, PC optimizer, or an anti-virus/malware remover – The iolo System Mechanic® technology reverses the damage done to Windows or Mac, eliminating the need for time-consuming reinstallations & costly technician bills.
It is available for FREE. Although, for some more advanced features & 100% effective fixes you may need to purchase a full license.
If your “Sekhmet” ransomware is still not removed — don’t hesitate and contact us via email, or a Facebook messenger (the blue ‘bubble’ on the bottom-right of your screen).