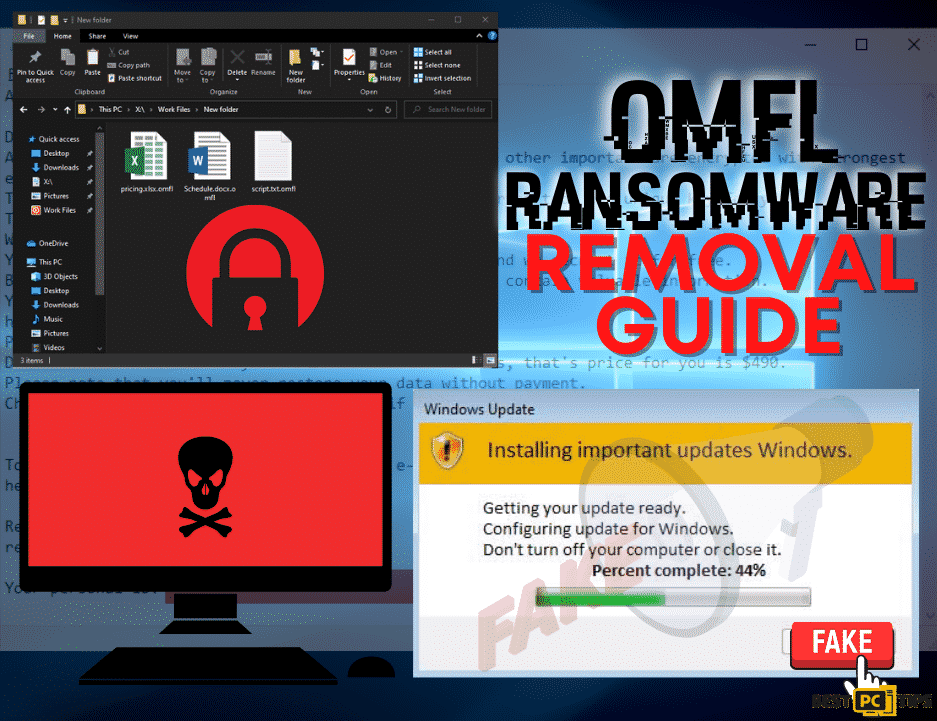
What is Lyli Ransomware and How to Remove It (FREE Instructions)
Gerald T.
Issue:My files turned into .lyli and I can't open them, how can I fix this?
Hi,
all of my files became unreadable and unusable, with .lyli extension. I got a note that they were encrypted and that I should pay the encryption team to recover my files...
Is there any way around this?
Thank you.
The Lyli Ransomware is a type of Ransomware that encrypts the infected user’s data, renames them and creates a ransom note in all of the folders that has the contained encrypted files. Files that gets encrypted are appended by “.lyli” extension. As an example, if the original file is named “sample.jpg” it will be renamed to “sample.lyli”, the same goes for the rest of the files that are infected whether be it photos, videos, text files, folder, etc.
Discovered by Mr. Michael Gillespie, the Lyli Ransomware has been determined to belong to the family of ransomwares under the name of Djvu.
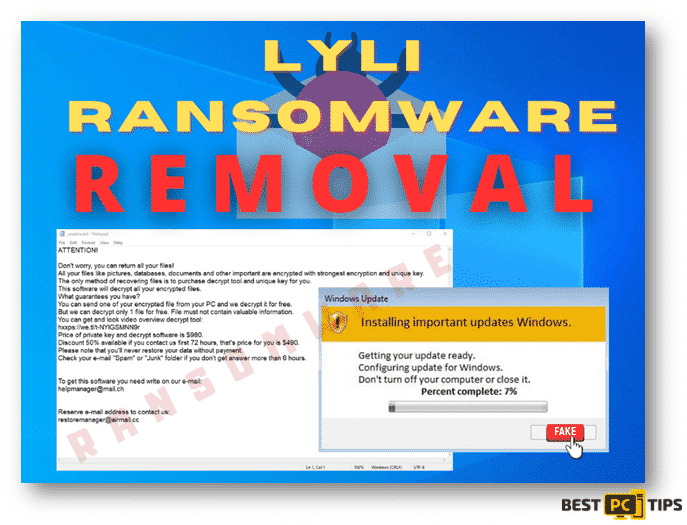
In a machine infected by the Lyli Ransomware, users will get a ransom note from the developers of the ransomware. The ransom note file is named “_readme.txt” text file which can be opened with Windows Notepad. In the ransom note, victims are told that they can recover their files by buying a decryption software from the developer of the ransomware. The price of the decryption software ranges from $490 up to $980, depending on how fast the victim will contact the developer.
As per the instructions of the developer of the ransomware, the victims should contact them via email at [email protected]. or [email protected] so that they can provide them with the steps on where to send the payment and how they can receive the decryption software. In addition, as per the ransom note, they will decrypt one file for free to show the victim that they do indeed have a decryption tool available.
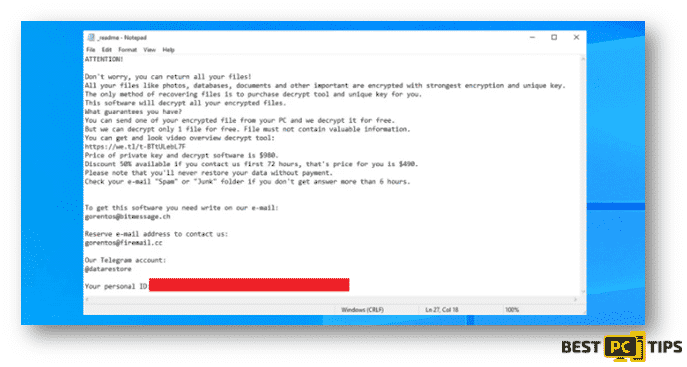
Here’s the content of the Ransom Note:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-h159DSA7cz
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
[email protected]
Reserve e-mail address to contact us:
[email protected]
Our Telegram account:
@Datarestore
Although they are giving an option to their victims to recover their files, it is strongly discouraged that victims of Lyli Ransomware pay for the file decryption tool. As per reports, users who paid for the decryption tool did not get any response from the cyber criminals after they have sent the payment for the tool.
How to Avoid Getting Infected with Lyli Ransomware
Just as most of other ransomwares, Lyli Ransomware can come bundled in Trojan applications, fake software updating tools, spam emails, untrustworthy software/file sources, unofficial cracking/activation tools other unofficial means of downloading or activating a software or program.
Trojan viruses can come bundled in a legitimate software however, in the process of installation of the file there will be a bundled malware with it that will be installed together with the legitimate software. Another way to get infected with the Lyli Ransomware is through spam emails that contains suspicious attachments or untrustworthy site links that are designed to download and install malicious files.
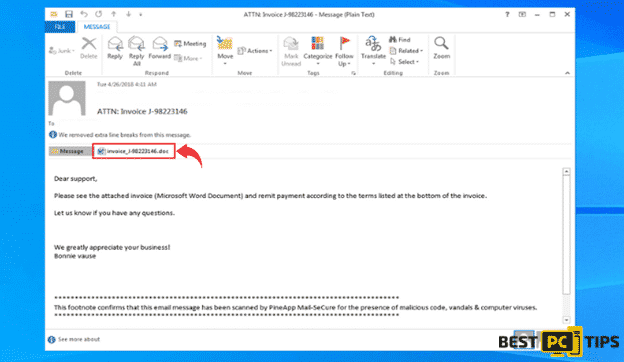
In most cases, spam emails contain files that looks like an MS office document, PDF Document or a ZIP file but in reality, those are the programs that will cause the infection on your system as soon as you download and open them.
Here’s how a spam email with a malicious attachment looks like:
Summary of the Security Threat
| Name | Lyli Ransomware |
| Type of Threat | Files Encryptor, Crypocurrency Virus, Ransomware |
| Names under Detection | Full List Of Detections (VirusTotal), Kaspersky (HEUR:Trojan-Ransom.Win32.Stop.gen), ESET-NOD32 (A Variant Of Win32/Kryptik.HGLF), Emsisoft (Trojan.GenericKDZ.70420 (B) and BitDefender (Trojan.GenericKDZ.70420) |
| File Extension | .lyli |
| Name of Ransom Note | _readme.txt |
| Amount of Ransom | $490 (if you contact the threat developer within 72 hours upon infection) up to $980 (after 72 hours of infection) |
| Contact Details of Cyber Criminal | [email protected] and [email protected] |
| Threat Symptoms and Potential Damage | Users will not be able to open the files on their system (locked files), file extensions will be replaced to .lyli. Users will be left with a ransom note by the ransomware developer and will be demanded to pay a certain amount to recover the victim’s files. |
| Method of Distribution | Malicious ads from untrustworthy websites, downloaded torrent files from unreliable websites, Macros or Infected email attachments |
| Suggested Removal Tool | If you think there is an infection in your system but have not yet seen the symptoms in your system, cyber security experts recommends using Malwarbytes to do a holistic scan on your computer. |
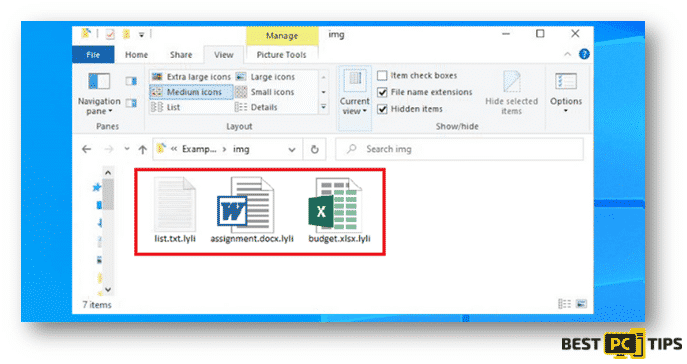
Below is a screenshot of infected files with “.lyli” extension:
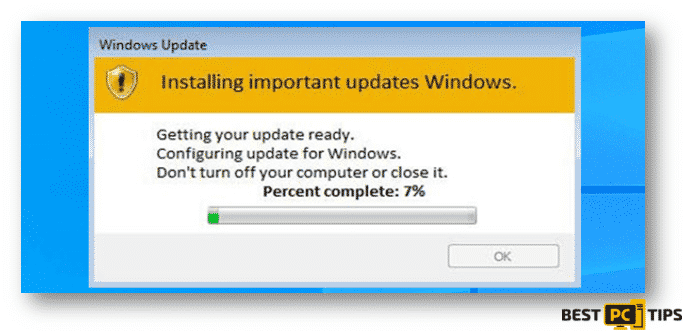
This is the fake “Windows Update” pop-up during the encryption of the infected files:
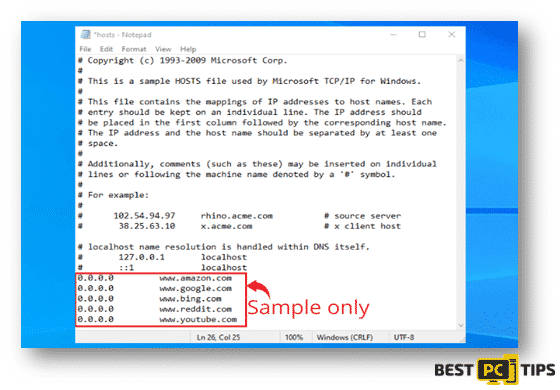
Another important information to note is that aside from the regular symptoms that ransomwares can cause is that, once it infects the system it will also add multiple new entries to the systems’ Windows “hosts” file. The new entries will have the links or URLs of several websites that mostly relate to the removal of viruses and malwares. The developers behind these malwares have made sure that users will not be able to access any websites which contains information regarding the removal of viruses and malwares.
Here’s a sample of Windows Hosts:
Additional Information About Djvu Family Ransomware Infections
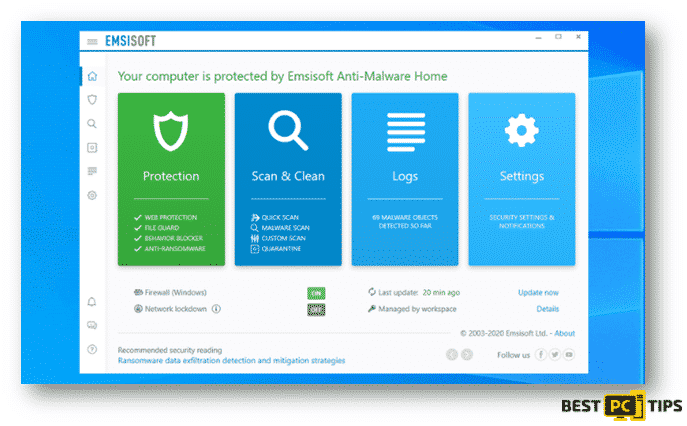
There are 2 different versions of Djvu Ransomwares that are currently active which are the old and new versions. The old versions of Djvu Ransomwares were created to encrypt the files and data of their victims using a hard-coded offline key. This means if the infected system is not connected to the internet, the ransomware will commence the infection and encryption of the files and data in the system. With this process, some victims are able to successfully decrypt some infected files with the help of the Decryption Tool which was developed by Emsisoft and Michael Gillespie. However, if you were unfortunate enough to get infected with the newer version of a Djvu Ransomware, then the Djvu Decryption Tool from Emsisoft and Michael Gillespie will not be able to recover the encrypted files.
Here’s a screen shot of the Emsisoft Decryptor:
As of this moment, Emsisoft is providing decryption services for victims who have been infected with the “old version” of the virus. This means, machines that were infected with any Djvu ransomwares that were released before August of 2019.
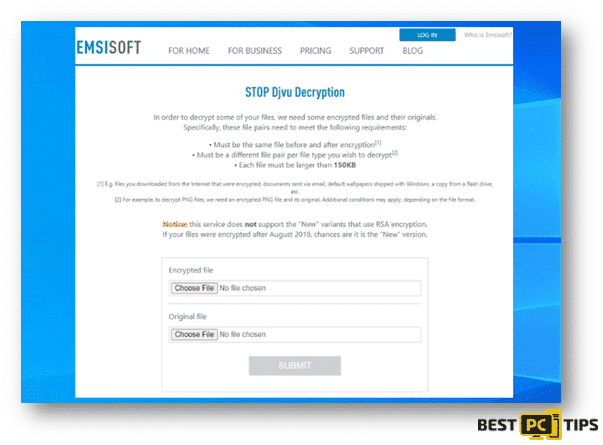
In order to use the service, the victims must upload a pair of the original and the encrypted file to their website at decrypter.emsisoft.com/submit/stopdjvu/. Once you have submitted the required files, they will provide you with the link to where you can download the decryption tool.
A lot of patience is needed for the processing of the files decryption as it may take a while to complete. Lastly, the machine should also have a stable internet connection during the decryption process or else the decryption process will not work.
Here’s a look at the file submission page at decrypter.emsisoft.com/submit/stopdjvu/:
How to Remove Lyli Ransomware Manually
Removing the Lyli Ransomware manually requires a lot of time, patience and advanced computer knowledge. Malwarebytes is one of the many tools that cyber security experts recommend in getting rid of malware.
Summarized steps on the Lyli Ransomware manual removal:
1st Step: Isolate the infected machine
2nd Step: Identify the type of infecting ransomware
3rd Step: Looking for an effective ransomware decryption tool
4th Step: Restoring the infected files using a data recovery tool
Isolate the Infected Machine
It is very important to isolate the infected machine from the network, any external storage device and even cloud storages as ransomware infections are engineered to encrypt files that are connected to the infected machine.
Follow these steps to disconnect from the internet:
There are several ways that you can disconnect from the internet, you can unplug the ethernet cable from your machine, power off your internet router, disconnect from your WiFi and a lot more. However, we will show you some steps that you can follow to disconnect it without having to stand up to disconnect some cables.
- Click on the “Windows” or “Start” button located on the bottom left corner of your desktop screen and type in “run” and press the “Enter” key on your keyboard. Once you see the Run line command, type in “ncpa.cpl” and click “OK”.
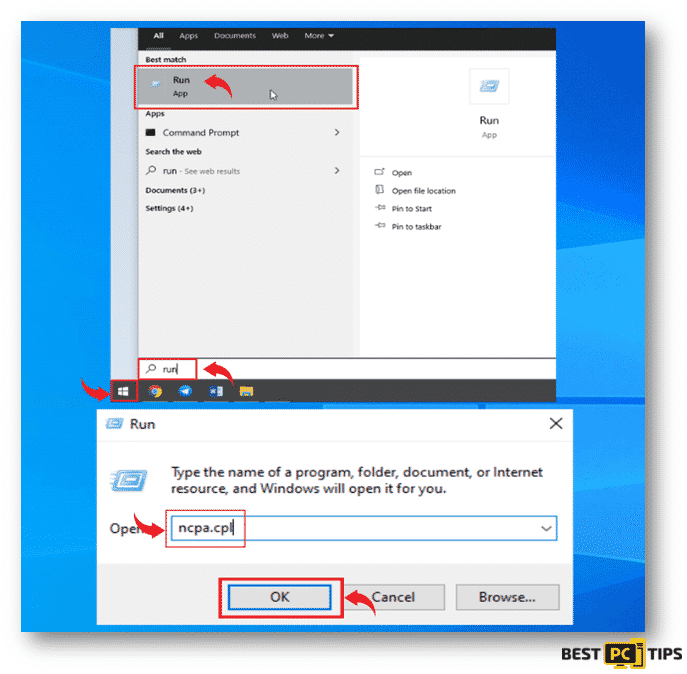
- Next, click on each active connection and click on the “Disable this network device”.
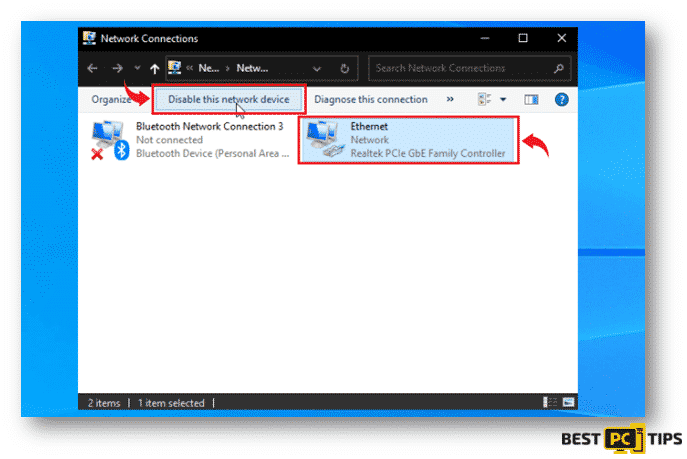
The next few steps will show you how to properly disconnect all of your storage devices such as portable hard drives, flash drives and even a connected mobile phone.
- Click on the “Arrow” that is pointing up beside the clock on the bottom left corner on your desktop screen taskbar, and click on the connected media icons and click on the “Eject” on the external storage device.
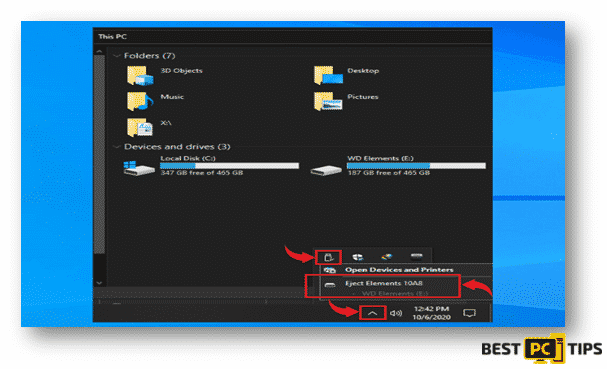
- Logging out from your cloud storage vary for each provider. It is best to contact your cloud storage provider if you need assistance on how to properly logout.
Identifying the Type of Ransomware Infection
In order for the victim to effectively get rid of the infection on your machine, they must identify what type of ransomware is infecting their system. In some cases, some ransomware infections will leave a ransom note on the infected system and will give you an introduction.
Below is a sample of a Ransom Note from a ransomware called “GANDCRAB V3”
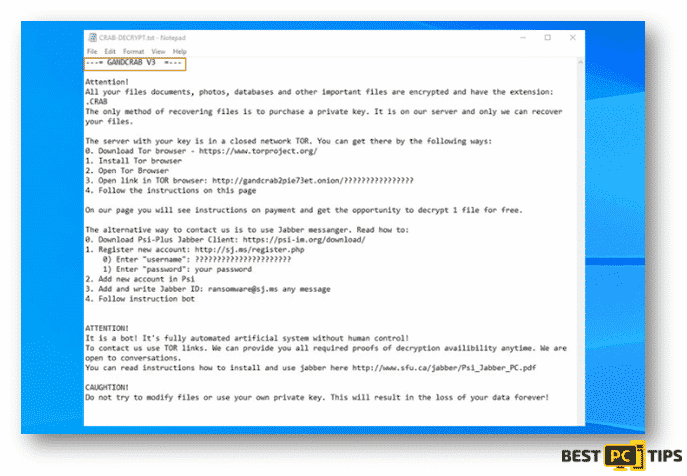
Unlike GANDCRAB V3, the Lyli Ransomware leaves a more direct message to the victim and asks the victim to pay them in order for the victim to recover their files. Ransom notes are given different names, some of which are “DECRYPT_FILES.html“, “_readme.txt“, “DECRYPTION_INSTRUCTIONS.txt“, “READ-ME.txt” and a lot more.
Aside from looking for the ransom note, you may also determine what type of ransomware has infected your system by looking at the file name extensions of the encrypted files as shown in the screenshot below.
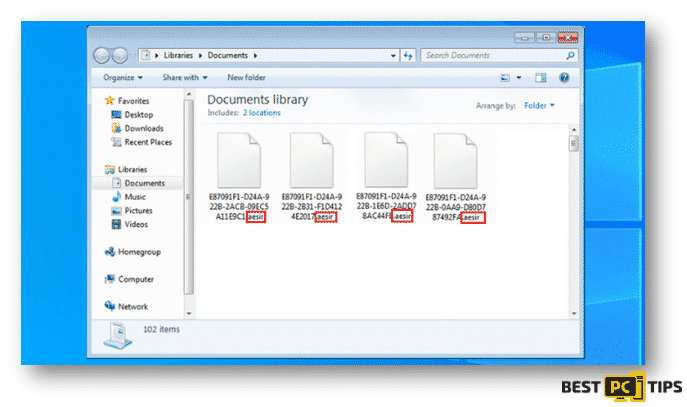
In this case, the ransomware that infected this system is named “Aesir”.
The next process of determining what ransomware is infecting a system is using the ID Ransomware website. This service can determine most of the currently existing ransomware. The victim only needs to upload an encrypted file or the ransom note. You may go to their website at https://id-ransomware.malwarehunterteam.com/
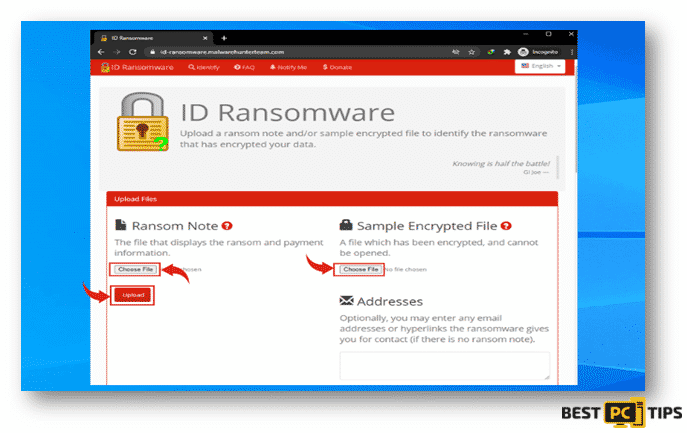
If ID Ransomware is able to determine what type of ransomware is infecting the machine, it will show this message containing the name of the ransomware.
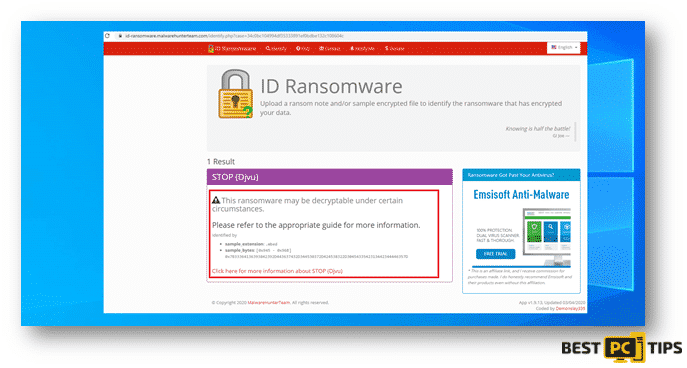
Here’s a screenshot of ID Ransomware not being able to determine what ransomware is infecting the machine.
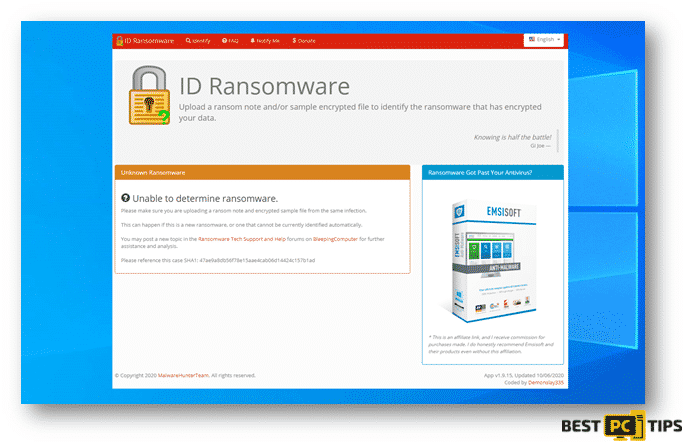
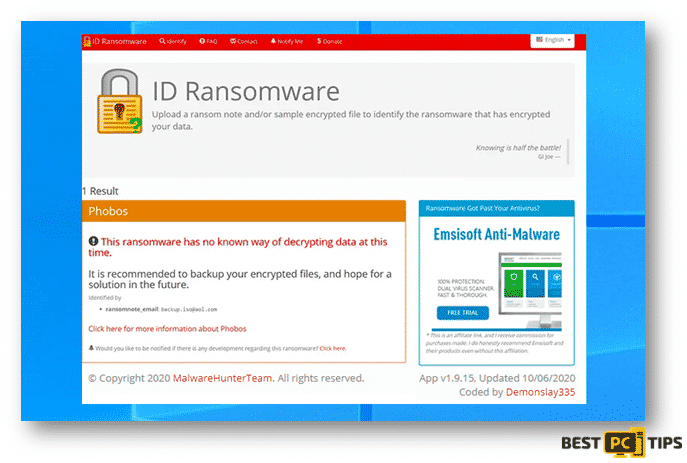
Lastly, here’s a screenshot of ID Ransomware determining the name of the ransomware however, but they do not have the capacity to decrypt the infected files.
Looking for Reliable Decryption Tools
Although there are ransomware infections such as Phobos and Dharha CrySis that are very difficult to remove and the only way to get rid of it is to contact the developer of the ransomware, there are also other ransomwares that can easily be removed by decryption tools that you can find online.
The No More Ransom Project is a free website that works as a search engine for possible decryption tools for ransomware infections. You will only need to upload 1 or 2 encrypted files or the ransom note left by the cyber criminals.

Restoring Files with Recovery Tools
Depending on the severity of the ransomware infection in the system, there are data recovery tools that can recover the infected files. One of the most used tool is the EaseUS Data Recovery Wizard Pro, it supports multiple types of files such as photos, documents, videos, audios, etc.
You can download EaseUS Data Recovery Wizard Pro by going to their website https://www.easeus.com/datarecoverywizardpro/index.htm
Below are steps on how you can use the EaseUS Data Recovery Wizard Pro:
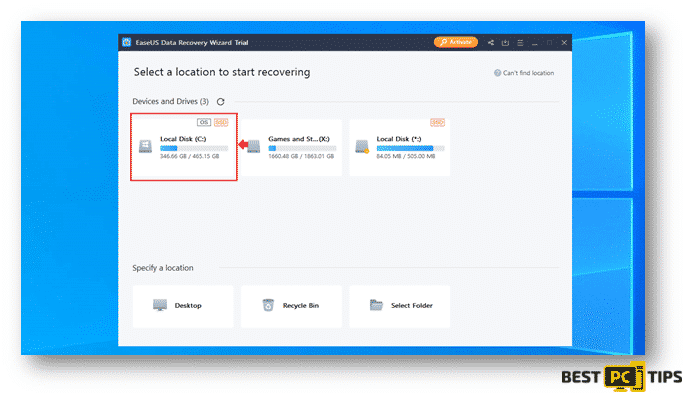
Step 1: How to Perform a Scan
- Click on the partition that had wish to have a scan on and it will automatically run the scan. The scan may take a while as it will go through the whole partition.
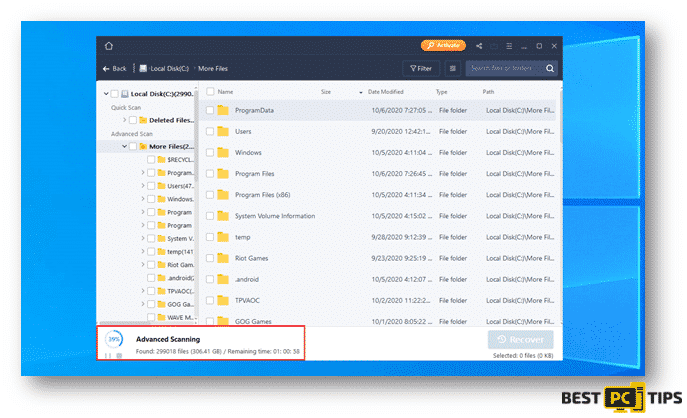
Step 2: Recovering the Discovered Data
- Selected your desired folder and click on recover.
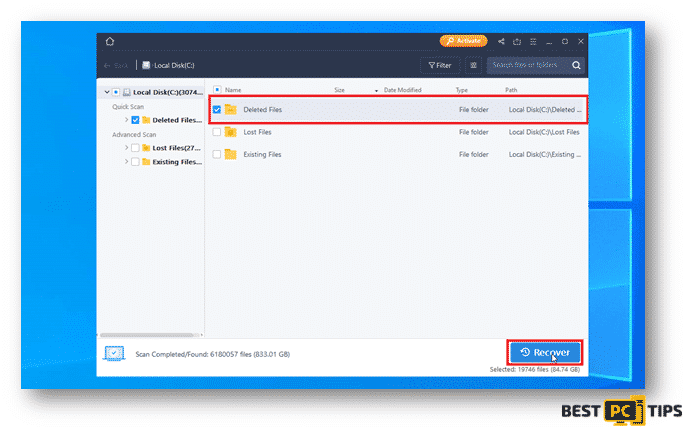
Step 3: Backing Up Your Data
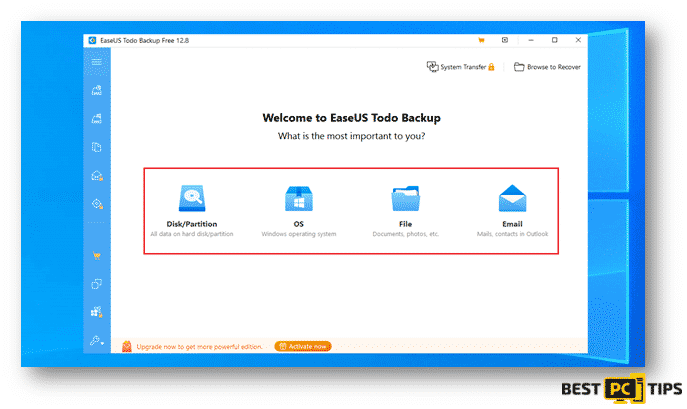
You may also use software that would automatically back up your files for you such as EaseUS Todo Backup. With EaseUS Todo Backup, you can easily schedule and automatically run your backups. In cases of disastrous files and data loss, EaseUS Todo Backup can also restore your data easily to get your computer working again. You can download EaseUS Todo Backup at https://www.easeus.com/backup-software/.
- Select your preferred types of files or data that you wish to do a backup of:
- Next step is to select the file path and files that you wish to back up and click on Proceed.
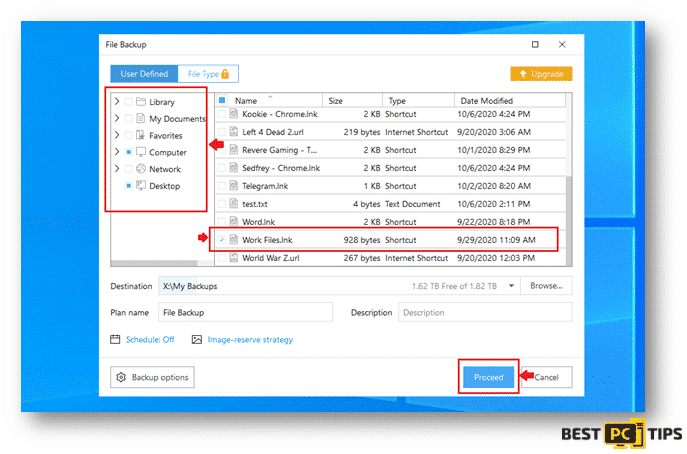
You backed up files will be located on the location that you selected once the backup process is complete.
Avoid & Remove Ransomware Automatically
In order for you to avoid disastrous files and data loss, make sure to make a backup of your important files. You can make a backup of your files by using an external device such as an external Hard Drive, an External SSD (Solid State Drive) or through a Cloud Service provider. Make sure to make a regular back up of your files to make sure all your files are up to date.
We also recommend to always use a high-grade anti-malware software like Malwarebytes which will scan your PC 24/7 and prevent any ransomware or any other viruses from infecting your system.
Offer
Malwarebytes — is a patented PC & MAC repair tool & the only program of its kind. It’s not only a registry fix, PC optimizer, or an anti-virus scanner – The Malwarebytes technology reverses the damage done to Windows or Mac, eliminating the need for time-consuming reinstallations & costly technician bills.
It is available for FREE. Although, for some more advanced features & 100% effective fixes you may need to purchase a full license.
If your LYLI Ransomware issue is still not fixed — don’t hesitate and contact us via email, or a Facebook messenger (the blue ‘bubble’ on the bottom-right of your screen).