AMJIXIUS Ransomware Removal Guide (Quick Instructions)
Porter B.
Issue:My files have been ecnrypted with .amjixius extension. What should I do now?
Hi,
my pc files were encrypted with .amjixius extension and now I'm required to pay a ransom...
Is there a cheaper and easier way out of it?
Thanks.
The more time we use going online to all of our accounts and visiting websites, encountering a malicious site is possible. Now, if your anti-malware program detects a malware, it must be dealt with quickly.

What is AMJIXIUS Ransomware?
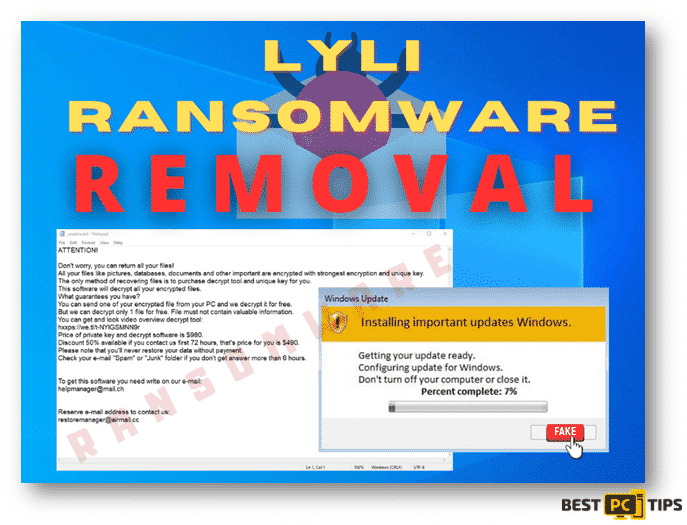
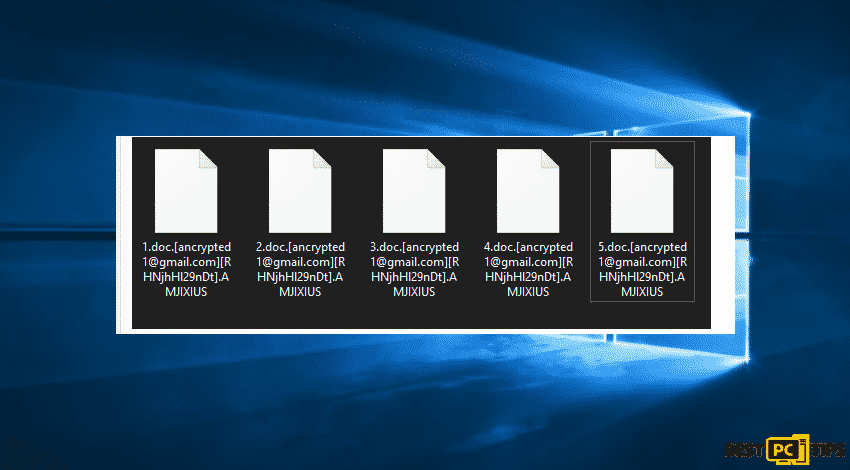
The AMJIXIUS is another type of ransomware which can infiltrate your computer and then keep away your access to your important files. The user can not notice anything suspicious and to regain data access, cybercriminals demand money from victims in BTC cryptocurrency. The user files change into .AMJIXIUS extension. The filename will be 2.jpg.[[email protected]][RHNjhHl29nDt].AMJIXIUS.
As part of the ransom note, the only way to decrypt files victims to use a decryption key which can only be purchased from developers of the AMJIXIUS ransomware which will give you instructions on how to pay for that key. Moreover, victims are offered a free decryption of files as a proof that the ransomware developers have the right decryption key.
Needless to say, the cyber criminals behind AMJIXIUS are the only ones who have the right decryption key. In addition, there will be no third-party tool which can decrypt files that are encrypted by the ransomware. Paying the ransom does not ensure that the developers of the ransomware will send users a decryption key or a tool. Most of the time, paying the ransom is just a scam. The only way to prevent from both data and financial loss, opt a free restoration of files or having a backup of the files. Also, there are files that are encrypted but installed by the ransomware. Then, they can be prevented from being encrypted by uninstalling that ransomware from the operating system. If you are experiencing ransomware, the message below is a sample message:
There are examples of ransomware and the list are BackMamba, cuteRansomware and Gac. As a rule, the victims of ransomware attacks could not access their files unless they decrypt them with the appropriate tool. Most of the time, the ransomware is geared toward generating ransom note that contains instructions on how to contact ransomware developers and/or purchase that decryption tool (or tools).
Following to encrypting the files, it generates a ransom note and dropped on the desktop screen. This ransom note contains a short message. In the message an email address is provided. This malware encrypts the files by using some sophisticated algorithm and make them unusable. Execution of the attached link result into the activation of the payload and hence it runs and download/install malware in the computer. The only main differences among ransomware are the symmetric or asymmetric algorithm. Victims can decrypt files that are encrypted by ransomware when that malware has some bugs, flaws/when it is not finished. However, it is not a common case.
A Possible Way How Your Computer Got Infected
Among the popular ways to distribute malware is to send spam emails or malicious files attached in the email along with download links for malicious files. Once the user started to open the files, the malware will be installed. Such examples of files that can be used to trick recipients into infecting computers are through emails with attachments such as Microsoft Office, PDF documents, archive files like RAR, ZIP, executable files (like .exe), or JavaScript files. Another way that your computer will be infected is by tricking users into installing a Trojan in their device. A type of Trojan can cause chain infections once installed on computers and can also install additional malware.
If you have encountered unreliable software download channels which are like unofficial websites, freeware download websites, free file hosting pages, peer-to-peer networks. When you encounter third-party downloaders, it can also be a way of hackers to install malware as well. Users install malware when they download some malicious file and then open it. There can be infection when they use a fake software as updating tools which can cause damage by installing malware instead of updates, fixes for installed programs, or by exploiting bugs, flaws of installed outdated software.
| Name | AMJIXIUS virus |
| Threat Type | Ransomware, Crypto Virus, Files locker |
| Encrypted Files Extension | .AMJIXIUS |
| Ransom Demanding Message | Pop-up window |
| Cyber Criminal Contact | [email protected] |
| Detection Names | Avast (Win32:MalwareX-gen [Trj]), BitDefender (Trojan.GenericKD.35784096), ESET-NOD32 (A Variant Of MSIL/Filecoder.AEQ), Kaspersky (HEUR:Trojan.Win32.Generic), Microsoft (Trojan:Win32/Ymacco.AAD6), Full List Of Detections (virustotal) |
| Symptoms | Cannot open files stored on your computer, previously functional files now have a different extension (for example, my.docx.locked). A ransom demand message is displayed on your desktop. Cyber criminals demand payment of a ransom (usually in bitcoins) to unlock your files. |
| Distribution methods | Infected email attachments (macros), torrent websites, malicious ads. |
| Damage | All files are encrypted and cannot be opened without paying a ransom. Additional password-stealing trojans and malware infections can be installed together with a ransomware infection. |
| Malware Removal (Windows) | To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using iolo System Mechanic. |
Protect Your Device From Infections (AMJIXIUS & Others)
The irrelevant emails contain attachments or web links that are received from unknown, suspicious addresses should be ignored. In most cases, emails sent with the purpose to trick recipients into infecting computers. The software should not be downloaded or installed via third party downloaders or installers. Keep in mind that software should be downloaded from official websites and direct links. The already installed software must be activated and updated only using tools or implemented functions provided by official developers.
If your computer is already infected with AMJIXIUS, we recommend running a scan with iolo System Mechanic for Windows to automatically eliminate this ransomware.
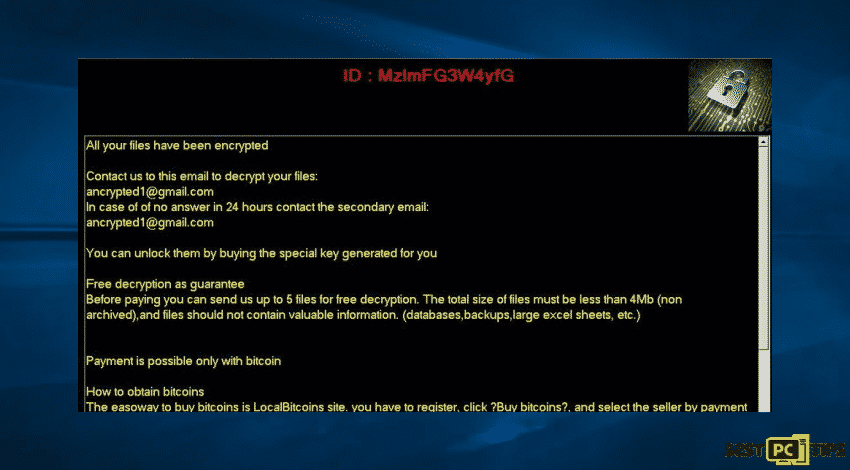
Text presented in the pop-up window that require ransom:
“All your files have been encrypted
Contact us to this email to decrypt your files:
[email protected]
In case of of no answer in 24 hours contact the secondary email:
[email protected]
You can unlock them by buying the special key generated for you
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 4Mb (non archived),and files should not contain valuable information. (databases,backups,large excel sheets, etc.)
Payment is possible only with bitcoin
How to obtain bitcoins
The easoway to buy bitcoins is LocalBitcoins site. you have to register, click ?Buy bitcoins?, and select the seller by payment method and price.
Https://localbitcoins.com/buy_bitcoins
Also you can fund other places to buy Bitcoins and beginners guide here:
Http://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention !!!Do not rename encrypted files. Do not try to decrypt your data using third party softwares, it may cause permanent data loss.Decryption or your files with the help of third parties may cause increased price(they add their fee to ours) or you can become a victim of a scam“
Screenshot of files encrypted by AMJIXIUS:
Instead of an automatic removal of the ransomware, you may follow our step-by-step guidelines in order to remove AMJIXIUS ransomware and decrypt .AMJIXIUS files.
Disconnecting the Infected Device
There are ransomware types of infections that are designed to encrypt files within external storage devices in order to infect and to cause infection too in the entire local network. For this reason, it is very important to isolate the infected device (computer) as soon as possible.
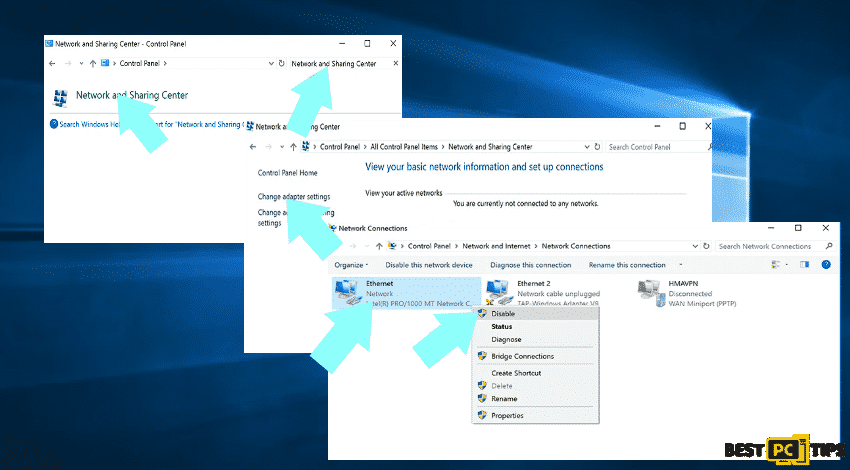
Step 1: Remove Internet Connection
You can easily unplug the Ethernet cable from the motherboard, however, some devices are connected via a wireless network and for some users (especially those who are not particularly tech-savvy), disconnecting cables may seem troublesome. To fix the issue, go to Control Panel instead.
- Go to Control Panel
- Select Network and Sharing Center
- Click Change adapter settings
- Right click on the connection point then select disable (You can go back to settings by clicking Enable then done with the repair)
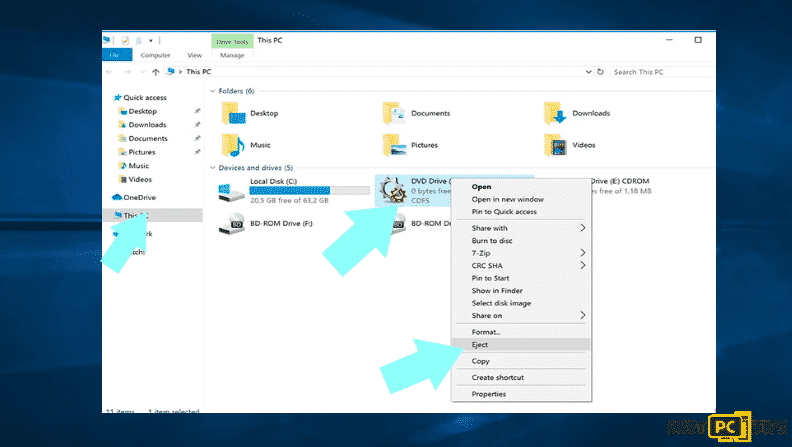
Step 2: Unplug All Storage Devices
The ransomware might encrypt the data and infiltrate all storage devices that are connected to the computer. With that said, all external storage devices are included such as flash drives, portable hard drives and others. These tools must be unplugged immediately. However, we strongly advise to eject each device before disconnecting to prevent corrupted data.
- Go to My Computer
- Choose the device then select Eject
Step 3: Log-out of cloud storage accounts
There are hijack software that are in charge of data stored in the online storage and because of that, the data could be corrupted or encrypted. If this is the case, you should completely disconnect and logout all cloud storage accounts across all browsers and other associated software. You should also consider temporarily uninstalling the cloud-management software until the infection is completely removed.
Determine the Infection of the Ransomware (Is It Really AMJIXIUS?)
To manage the infection, it is best to handle it by identifying it. There are some ransomware infections use ransom-demand messages as an introduction (see the WALDO ransomware text file below).
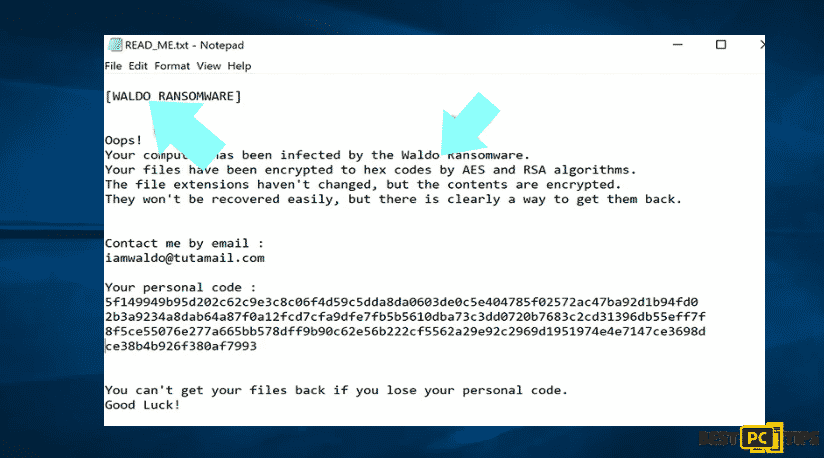
The occurrence of this one is rare because most cases the ransomware deliver more direct messages simply stating that data is encrypted and those victims must pay some sort of ransom. Ransomware-type infections typically generate messages with different file names (for example, “_readme.txt”, “READ-ME.txt”, “DECRYPTION_INSTRUCTIONS.txt”, “DECRYPT_FILES.html”, etc.). One problem you may want to check is the generic names in infections. Though the delivered messages are different and the infections themselves are unrelated. Therefore, using the message filename alone can be ineffective and even lead to permanent data loss.
There is an alternative to easily determine where the ransomware infection is. By doing a file extension check which is appended to each encrypted file. Ransomware infections are often named by the extensions they append.
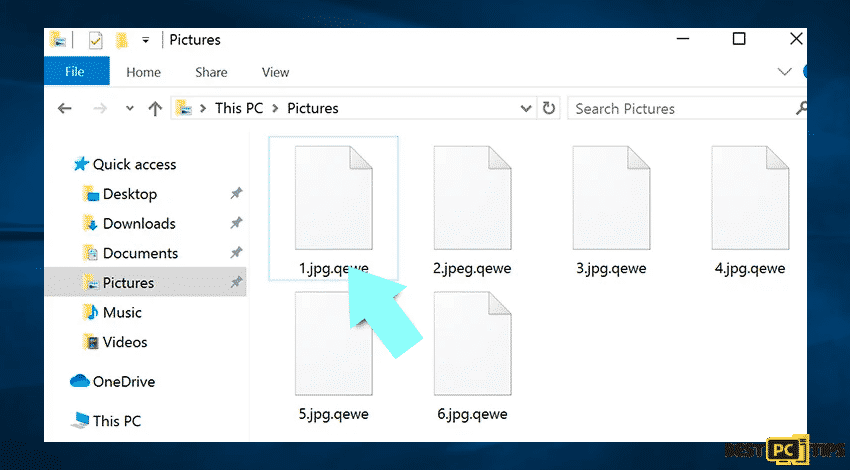
The method is effective but the encrypted files are unique that many ransomware infections append a generic one. You can automatically to identify a ransomware infection through the ID Ransomware website. Moreover, the ransomware will be determined in just a few seconds and the user will be provided with various details such as the name of the malware family to which the infection belongs.
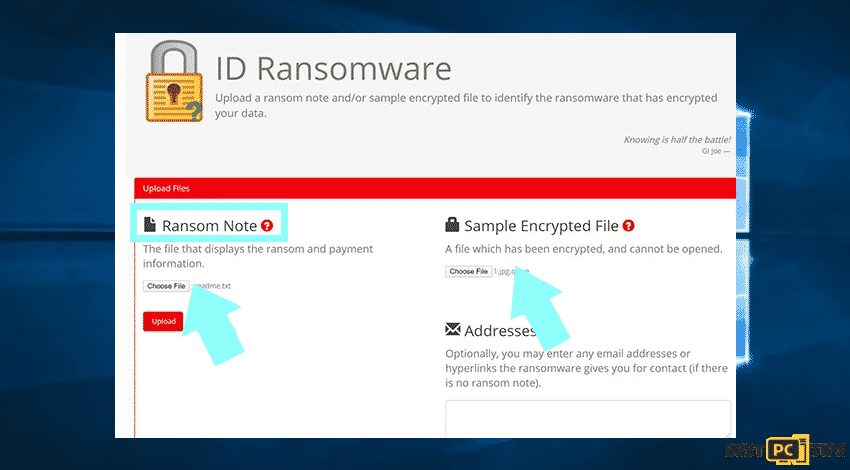
Sample 1: (Qewe [Stop/Djvu] ransomware):
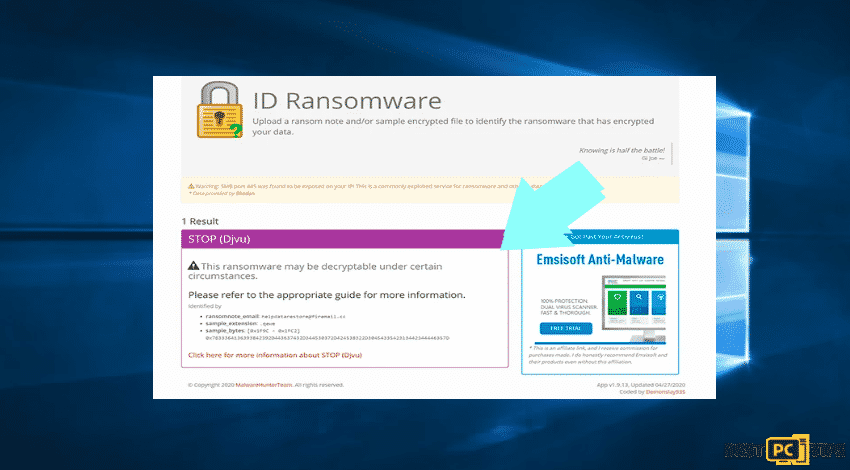
Sample 2: (.iso [Phobos] ransomware):
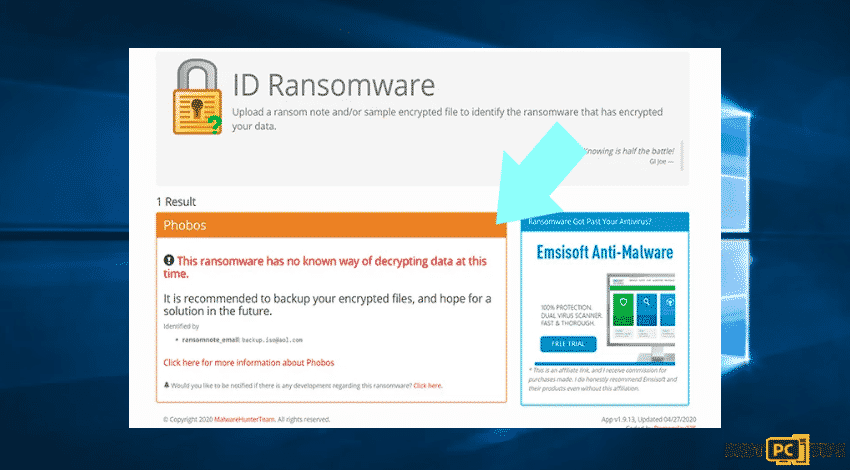
In case that your data happens to be encrypted by a ransomware which is not supported by ID ransomware then there can always be a way to try searching through the internet though certain keywords including ransom message title, file extension, provided contact emails, and cryptowallet addresses.
Look for Ransomware Decryption Tools
The encryption algorithms that most ransomware use are sophisticated and once the encryption is done properly, then, the developer is the only one who can restore the data. The reason behind this is that the decryption requires a specific key. No need to worry for the key is generated during the encryption. To restore the data without having the key is not possible. Most cases it is stored in a remote server instead of using the infected machine as a host. Dharma (CrySis), Phobos, and other families of high-end ransomware infections are virtually flawless, and thus restoring data encrypted without the developers’ involvement is simply impossible. With that said, it is best to always check for available decryption tools for any ransomware that infiltrates your computer.
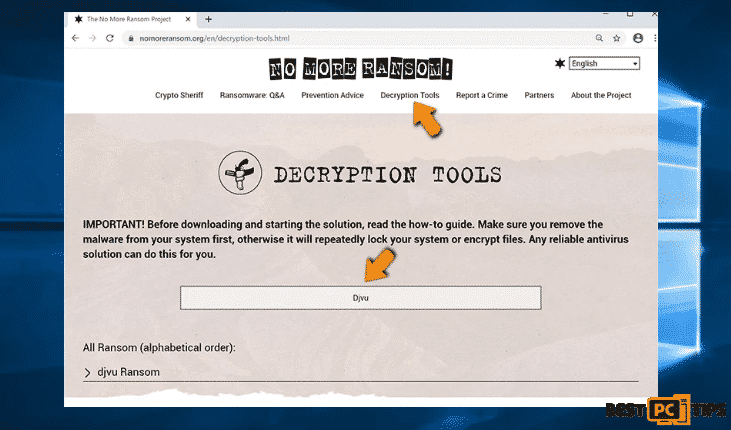
Knowing the appropriate decryption tool can be a daunting task and since we know the struggle, we recommend users to opt for No More Ransom Project and this is where identifying the ransomware infection is useful. The No More Ransom Project website contains a “Decryption Tools” section with a search bar. It is easy to navigate and to enter the name of the identified ransomware along with the available decryptors.
Restoration of Data with the Right Data Recovery Tools
Gauge the situation before taking action. Consider the quality of ransomware infection, type of encryption algorithm used, etc. Just restore data with legitimate third-party tools. We advise you to use EaseUS Data Recovery Wizard Pro. The tool supports more than thousand data types including graphics, video, audio, and documents.
Step 1: Do a complete scan
- Move your mouse over the partition that you wish to scan before clicking the scan option
- There is a selection to click a specific folder or shortcut icons
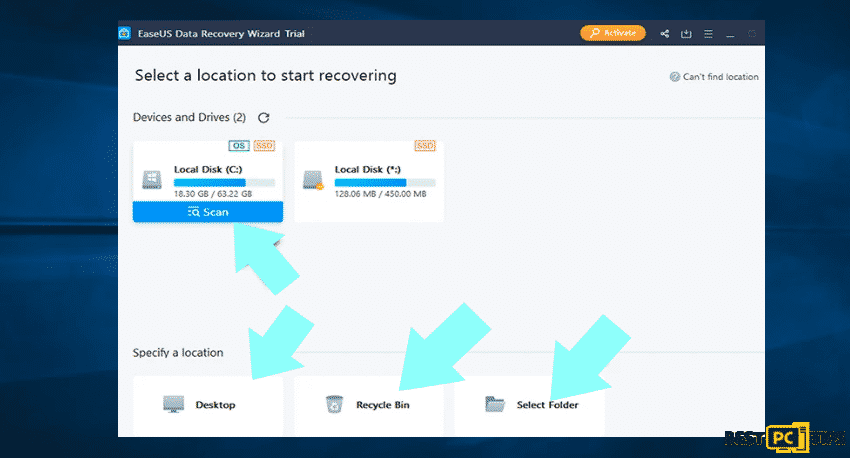
After selecting the scan using the EaseUS Data Recovery Wizard Pro, be patient in waiting for the results as it may take an hour depending on the volume of files in terms of quantity and size that you are scanning such as hundreds gigabytes could take over an hour. It is also advisable not to modify or delete existing files since this might interfere with the scanning process. For example, if you have added an additional data, the process will take few minutes longer.
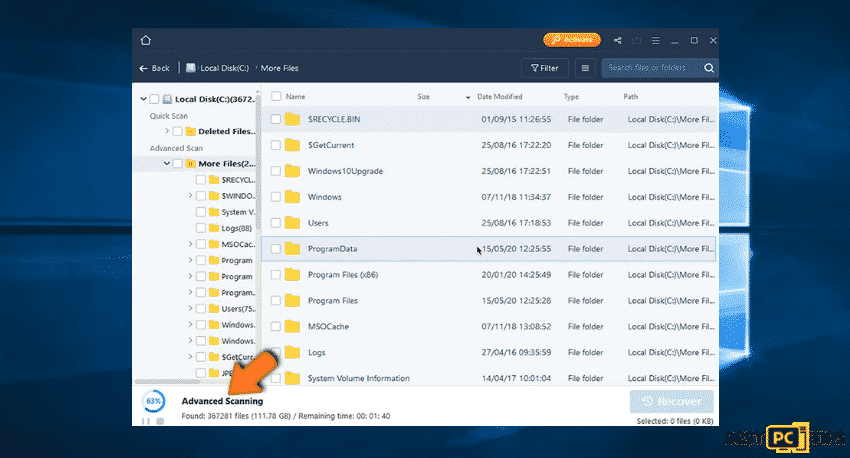
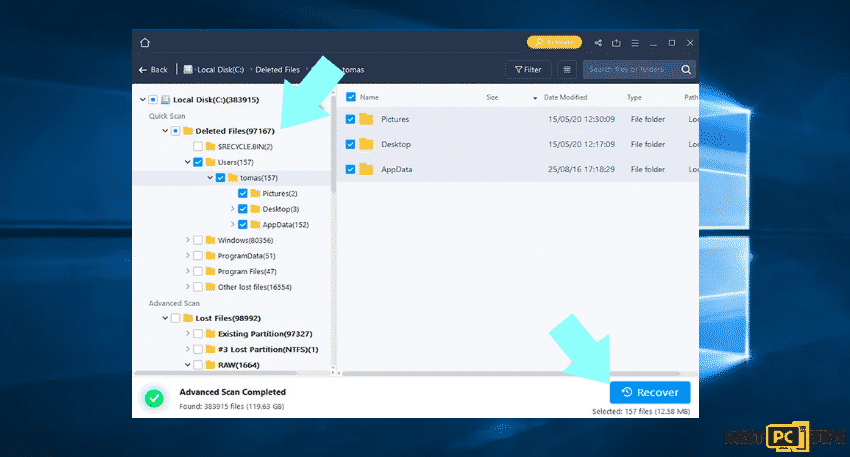
Step 2: Recover data
After the scanning, select the folders and files that you wish to restore and click recover. Take note that some free space on the storage device is needed to restore the data. Also, the trial version of the EaseUS Data Recovery Wizard Pro is only capable of scanning drives and listing recoverable files. For advanced features, you must be in a license subscription.
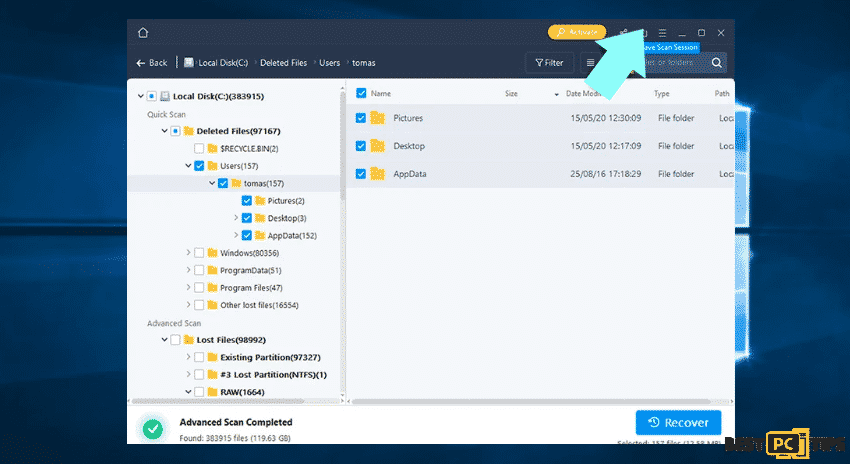
Step 3: Save the scan but this step is optional
Even though it is optional, we recommend that you save the scanning session once you have completed recovery, in case you decide to recover additional files later. Remember that by doing this, you can save time that you will need in order to not rescan the storage drive next time. To do so:
- Click the Save Scan Session
Make time for Data Backups
To manage your files properly is to create backups which are essential to secure your data in case of loss. Therefore, always be careful and think ahead. The way to do it is through partition management. We recommend that you store the data in multiple partitions and prevent storing important files in the partition which includes the entire operating system. In case that you are in a situation where you cannot boot the system and you are forced to format the disk where the OS is installed, the probability of losing all data stored in the drive is high.
This is the advantage of getting multiple partitions in case that you have the entire storage device assigned to a single partition, then, you will be forced to remove everything. But creating multiple partitions and allocating the data properly allows you to prevent such problems.
The most reliable method is through external storage device and keep it unplugged for data backups. Copy your data to an external hard drive, flash (thumb) drive, SSD, HDD, or any other storage device, unplug it and store it in a dry place away from sun and extreme temperatures.
Use EaseUS Todo Backup Application
We recommend the use of The “Home” edition of EaseUS Todo Backup because it is usually more than adequate for regular users. The EaseUS Todo Backup application provides extensive data protection features. With this, creating backups as well as encrypt and compress data process is easy for enhanced protection and storage saving purposes. Moreover, it enables you to set backup schedules, make bootable devices and restore system in case of crash. In addition, you can easily select where to store the backup folder you have created. In summary, EaseUS Todo Backup is an all-in-one tool, which provides all features required to properly backup your data.
To Make a Data Backup, follow the steps:
Step 1: Choose what folder you will backup
- Click the Menu
- Select File Backup
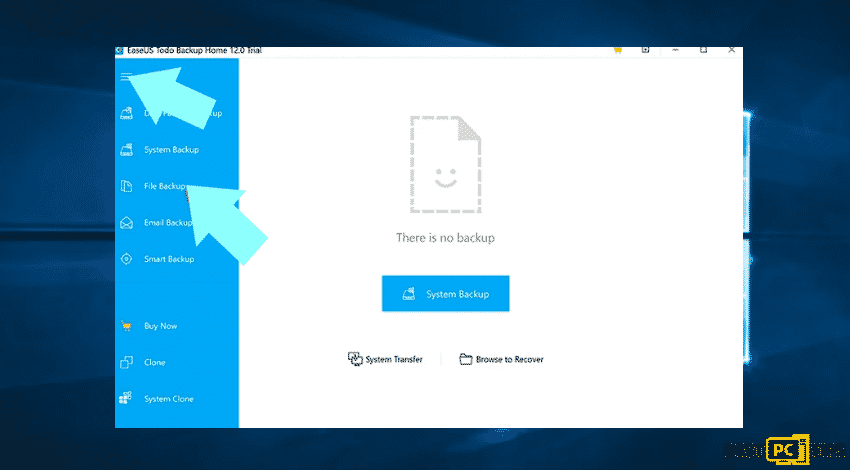
- Choose the files that you want to backup
- There is an option to enter name and description
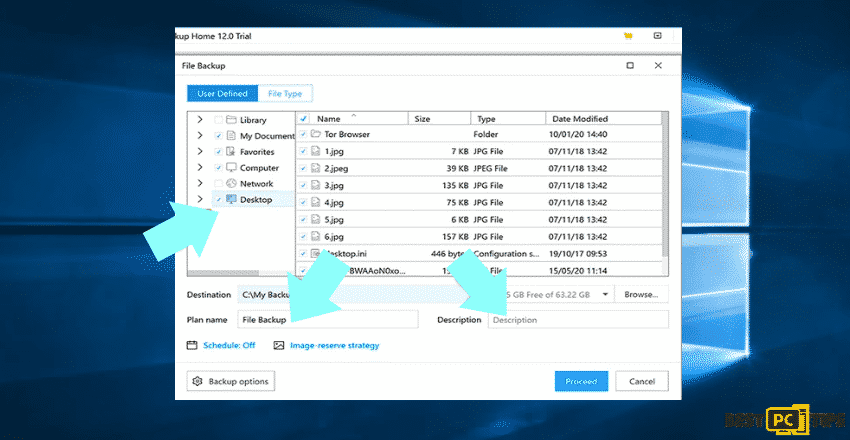
Step 2: Change the default settings
With the help of the EaseUS Todo Backup application which provides various additional options which can be added or modified while creating the backup. For example, there is a way to encrypt the data and add a password. Select the compression rate meaning the volume of backup that should be compressed.
- To open the options window, click the Backup options.
- Select the settings
- Then Save
- Reset your changes, click Reset to initial settings
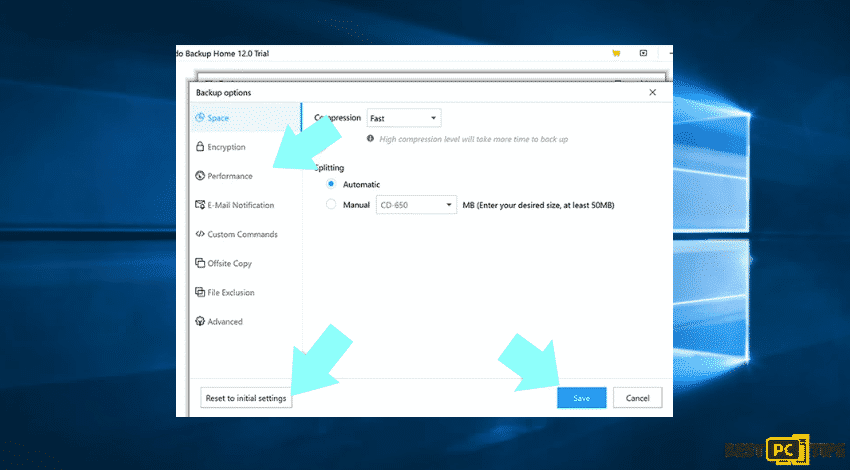
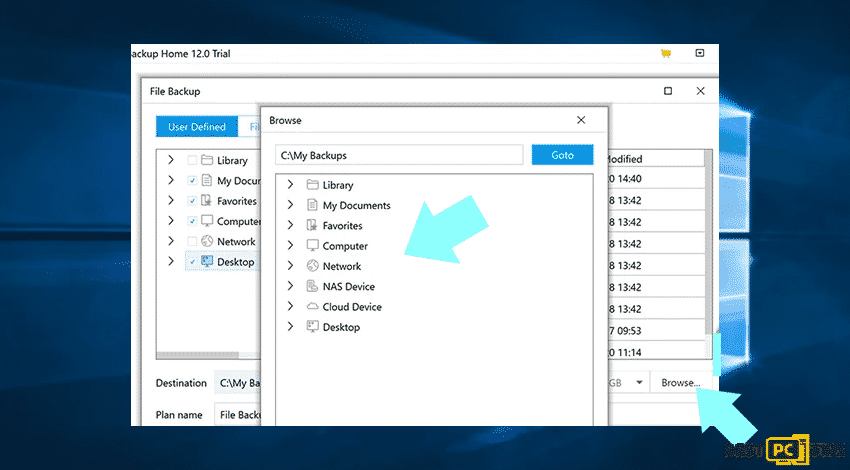
Step 3: Choose a backup destination
With the help of the EaseUS Todo Backup, you can choose where to save the backups either locally or externally.
- Click Browse
- Select the location to save backup
Step 4: Complete the process
It depends on the location that you have chosen, there have been a number of measures to take before the completion. In case that you are uploading an internet-connected location. Make sure to have a stable internet connection or else you have to start again. This is also the case for external storage devices, you should not interrupt and unplug until the process is complete. The progress bar always displays an estimated time remaining until the completion. Moreover, large backups with hundreds of gigabytes can take long hours to create. This is depending on the storage device speed, internet connection and other factors.
Keep in mind that the best way to prevent yourself from ransomware infections is to keep your data secure through backups.
Malicious Sites and Files That Cause Malware Penetration
The links to websites directly distribute malware payload which lead to other issues. Most of the time, infection is triggered by the payload executable or different type of file that users allow without their knowledge. The malicious files mostly come through torrent services or copies of legitimate sites to capture users. Once you recover the files on the infected machine, there is risk of getting them permanently damaged.
How to Protect Your Files Against Future Cyber-attacks Like AMJIXIUS and Others?
Presuming that your computer has malware removal software installed, you can easily remove the malware in your device’s system. Remember to be extra careful when opening sites especially when downloading files. Do not open spam e-mails and protect your mailbox. Malicious attachments in the spam folder or phishing e-mails are the most popular method of ransomware distribution. It is best to use spam filters and create anti-spam rules is good practice.
Offer
iolo System Mechanic® — is a patented PC & MAC repair tool & the only program of its kind. Not only it’s a registry fix, PC optimizer, or an anti-virus/malware remover – The iolo System Mechanic® technology reverses the damage done to Windows or Mac, eliminating the need for time-consuming reinstallations & costly technician bills.
It is available for FREE. Although, for some more advanced features & 100% effective fixes you may need to purchase a full license.
If your Amjixius ransomware virus is still not removed — don’t hesitate and contact us via email, or a Facebook messenger (the blue ‘bubble’ on the bottom-right of your screen).