How to Remove Koom Ransomware From Your PC (Free Instructions)
Hilary Paden
Issue:I can't open any of my files, all of them are with .koom extension! Please help me!
I don't know what happened. When I turned my computer on this morning I can no longer open any of my files.
All of the names of my office documents were renamed with a ".koom" extension and I keep getting a pop-up telling me that I need to update my computer.
Please, I need your help in fixing my computer.
Koom ransomware is a crypto-virus from STOP/DJVU family. It infects a PC using misleading tactics such as social engineering attacks. Once the virus enters the computer, Koom ransomware locks the user’s data. Some of the common files locked are spreadsheets, images, documents, videos, and more. It attaches a “.koom” extension to the filenames and from there creates a ransom note. The hackers “sells” the decryption file so that victims will have access to their documents again.

Important Information About the Koom Ransomware
Along with your files being encrypted, you will receive a “_readme.txt” file. The file includes specific information such as how much the decryption software and keys are ($980 but with a 50% discount in the first 72 hours) and the things you need to do to retrieve your files.
Furthermore, it also includes instructions on where to email the hackers. You also have a way to get one file decrypted for free when you email them.
Details About Koom Ransomware
As the note shares, you will be unable to decrypt the malware without using a tool that the hackers can only provide. That means the only way you can get your files again is if you have a personal back on a separate computer or hardware or if you can find any other decryption tool online. Experts suggest that ransom should never be paid since there is no assurance that the hackers will send a decryption tool.
Koom works just like other ransomware variants in which the files are encrypted then users receive a note which includes details and payment information. Some similar ransomware is yUixN, Delta Plus, and JamesBond.
Here’s a screenshot of infected files by Koom Ransomware:
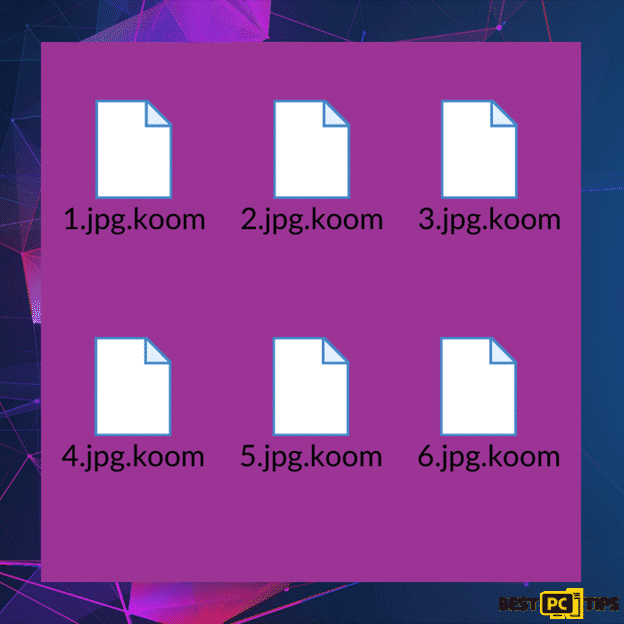
Koom Ransomware is likely distributed through emails, fake software updates, Trojans, programs, or software cracking tools, or downloading files from unreliable sources. It is crucial that the ransomware must be uninstalled from the PC right away.
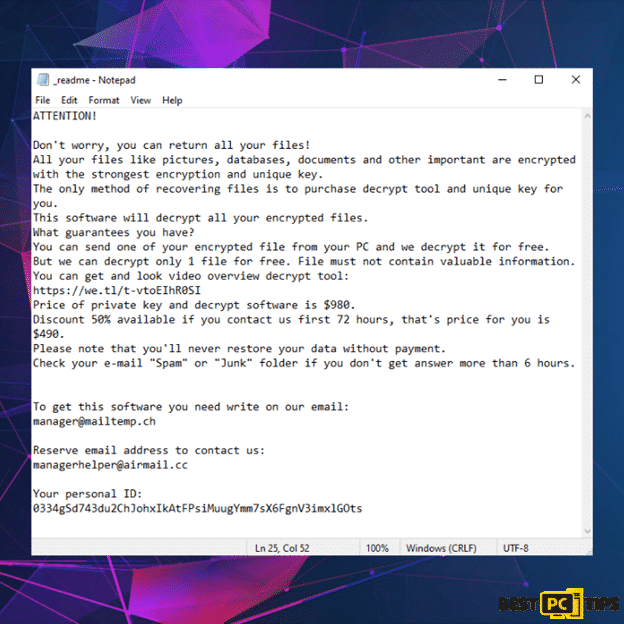
Here is the original ransom note from Koom creators:
“ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-vtoEIhR0SI
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
[email protected]
Reserve e-mail address to contact us:
[email protected]
Your personal ID:“.
Screenshot of a fake update by Koom Ransomware:
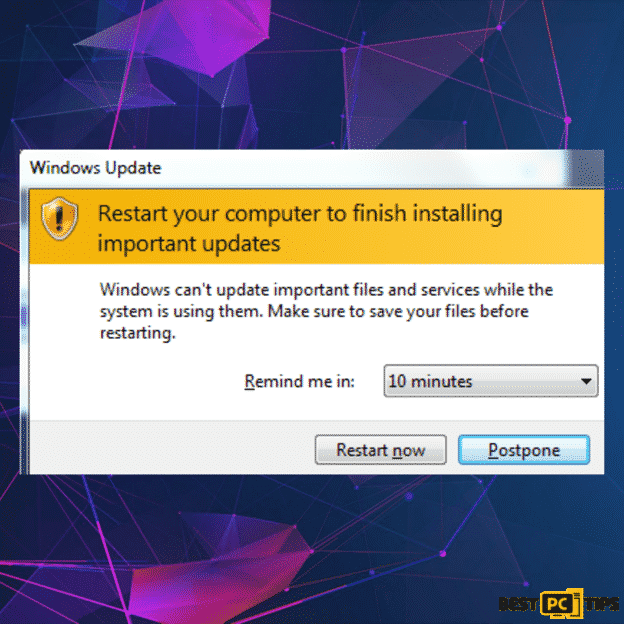
Here’s a brief summary of what the Koom Ransomware is all about:
| Name | Koom virus |
| Threat Type | Ransomware, Crypto Virus, Files locker |
| Encrypted Files Extension | .koom |
| Ransom Demanding Message | _readme.txt |
| Free Decryptor Available? | Partial (more information below). |
| Ransom Amount | $980/$490 |
| Cyber Criminal Contact | [email protected], [email protected] |
| Detection Names | Avast (FileRepMalware), AVG (FileRepMalware), Ikarus (Trojan.Win32.Glupteba), Kaspersky (UDS:Exploit.Win32.Shellcode.gen), Microsoft (Trojan:Win32/CryptInject.FB!MTB), Full List Of Detections (VirusTotal) |
| Symptoms | Cannot open files stored on your computer, previously functional files now have a different extension (for example, my.docx.locked). A ransom demand message is displayed on your desktop. Cyber criminals demand payment of a ransom (usually in bitcoins) to unlock your files. |
| Additional Information | This malware is designed to show a fake Windows Update window and modify the Windows “hosts” file to prevent users from accessing cyber security websites (more information below). |
| Distribution methods | Infected email attachments (macros), torrent websites, malicious ads. |
| Damage | All files are encrypted and cannot be opened without paying a ransom. Additional password-stealing trojans and malware infections can be installed together with a ransomware infection. |
Ways To Protect Your PC from Ransomware (Including Koom)
Since you now have an idea where you get this ransomware, it is crucial to take the necessary precaution to protect yourself.
- Never download any email attachments when you received them from unknown or suspicious senders.
- Avoid clicking any links from unknown emails.
- Files and updates should only be download from official website pages.
- Programs downloaded should only be installed using tools from their official developers.
- Use good and reliable antivirus software.
Important Reminder and File Recovery
Other than encrypting data, Djvu malware family infections also add several entries to the Windows “hosts” file. These entries will contain URLs of different websites that offer malware removal. The hackers do this to stop users from getting help from malware security websites. Thankfully, there are easy ways to remove these entries.
Djvu ransomware infections have old and new versions. The older version is made to encrypt data by using a hard-coded “offline key” which happens when the infected PC had no internet connection. As a result, some users can decrypt their data using a tool made by Michael Gillespie, a cyber security expert. Unfortunately, the “newer” version released in August 2019 rendered the decrypted useless.
If ever your PC is infected with the older version, you might be able to get back your files using tools made by Michael Gillespie and Emsisoft. You can download it along with the instructions from the Emsisoft official website.
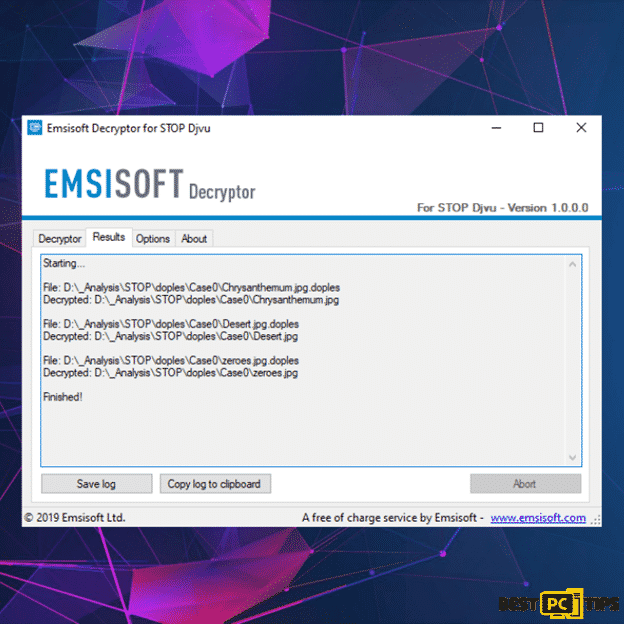
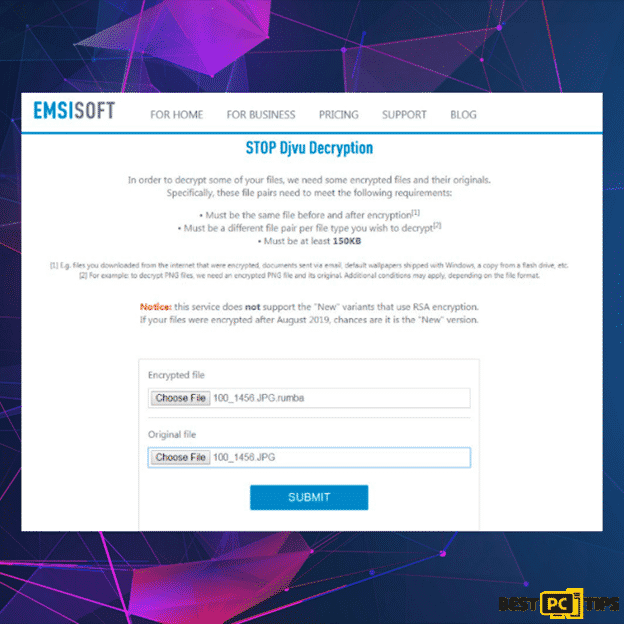
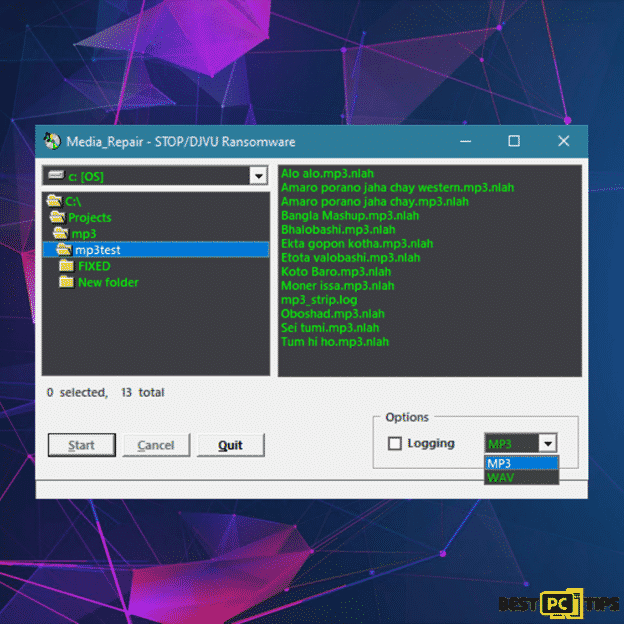
Koom/Djvu ransomware only encrypts portion (start) of the file which makes it unusable. Therefore, it is possible to restore other parts of the file that is not encrypted. This is useful especially if users need to access video or audio files. To do this, you can use DiskTuna’s Media Repair Tool. This tool is completely free and easy to use.
Reporting Koom Ransomware Infection To Authorities
It is highly encouraged that victims of a ransomware attack should immediately report it to authorities. Providing information to law enforcement will help curb cybercrime and can be very useful in the prosecution of hackers. Here is a shortlist of contact numbers where you can report these incidents:
- USA – Internet Crime Complaint Centre IC3
- United Kingdom – Action Fraud
- Spain – Policía Nacional
- France – Ministère de l’Intérieur
- Germany – Polizei
- Italy – Polizia di Stato
- The Netherlands – Politie
- Poland – Policja
- Portugal – Polícia Judiciária
Steps for Removing the Koom Ransomware
Isolate the Infected Device
Many issues involving ransomware will encrypt not just your device but also external storage devices and other computers connected to your network. As a result, it is crucial that you immediately isolate the infected device.
- Disconnect from the network and the Internet
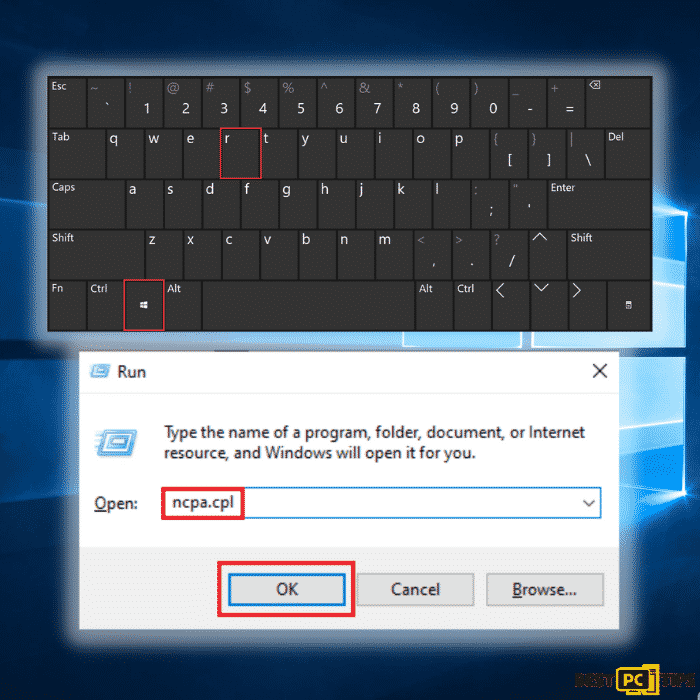
Immediately unplug the ethernet connection if your PC is connected by wire to your internet. For devices that are wirelessly connected, disconnect following these steps:
• Press the Windows Icon + R and type “ncpa.cpl” in the run command line and press “enter“
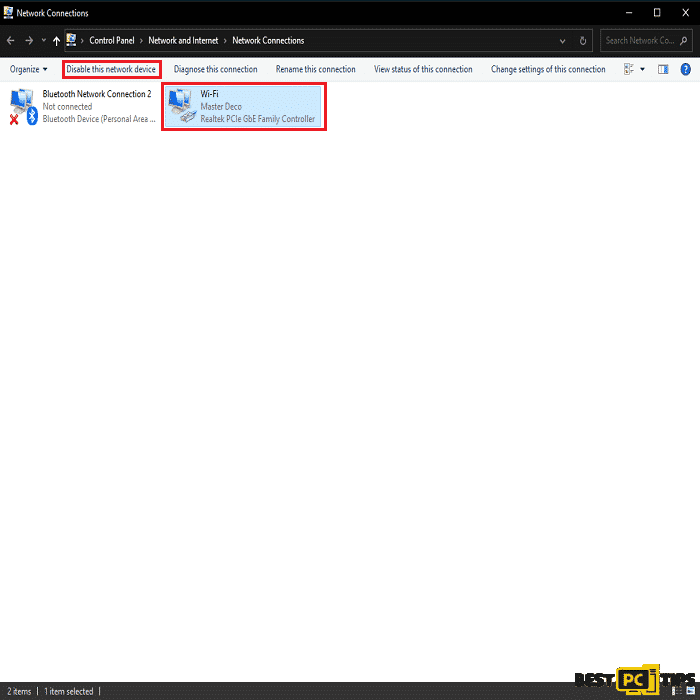
• Click on your network connection and click “Disable this network device“
- Unplug Any Storage Devices
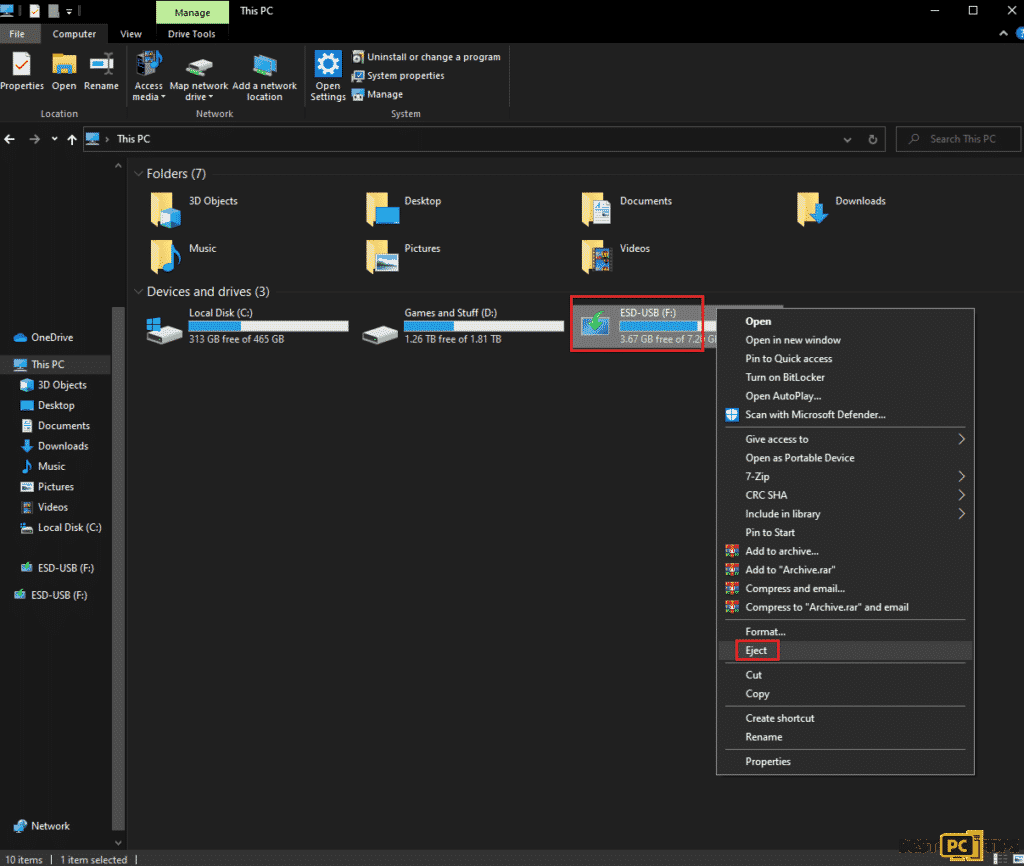
Ransomware is also notorious for encrypting storage devices connected to your PC. If your PC is infected with ransomware, unplug any storage device connected immediately. Be sure to properly eject each device to avoid data corruption.
Navigate to My Computer, right-click on the storage device and choose “Eject”.
- Log-out of Any Cloud Storage
There are cases when ransomware infections might also hijack any cloud storage. To avoid this problem, be sure to log out of the cloud storage account. If you are using cloud-management software, you can temporarily uninstall the program until the infection is removed for sure.
Identify the Ransomware Infection (Is It Really Koom?)
It is crucial to identify the ransomware infection correctly so that you can apply the right solution. Some ransomware infections will come with a note. Nonetheless, there are ransomware infections that will only show that your files are encrypted. In some cases, you can identify the name of the ransomware according to the notes you receive.
Another way is to check the file extension. Most ransomware is called after the extensions they append. This works great if it comes with a unique appended extension. There are cases when the ransomware infection comes with generic extensions such as .encrypted or .crypted.
You can also use the ID Ransomware website to identify the ransomware infection. You simply need to upload the ransom message or one of the encrypted files and the website will identify it for you.

Back-Up Your Data
Backing up your data is always a good practice for data security. When you are able to restore all your files, always back up your data.
Partition Management – It is highly recommended to store your data in multiple partitions. Never store your most important files in the partition that contains your entire operating system. That way you can avoid losing all your data in case you need to reformat the entire disk where your OS is saved. Having multiple partitions allows you to allocate your data properly and prevent you from losing all your files in the event of an infection. To learn partition, visit Microsoft’s website for complete instruction.
Back-Up Your Data Correctly – You can use external storage to back up all your data. This way, in case of an infection, you automatically have a way of restoring all your files. You can use an external hard drive, HDD, SSD, or a flash drive to back up your file.
You can also utilize Microsoft OneDrive for this purpose. OneDrive allows users to store personal files in the cloud. You can also easily sync the files to your PC so that your most recent files are always updated. OneDrive allows users to save, share, move and preview files making it very easy to manage all important data.
Back-Up Files In One Drive
- Select the folders or files that you want to backup.
- Click the OneDrive cloud icon to open the OneDrive menu. You can also customize your file backup settings in this folder.
- Next, select Help & Settings and then click Settings from the drop-down menu.
- Move to the Backup tab and click Manage backup.
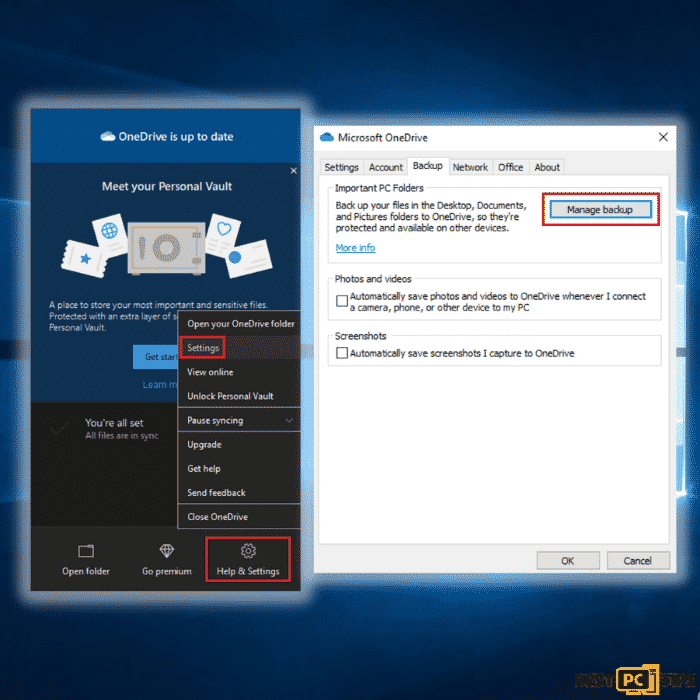
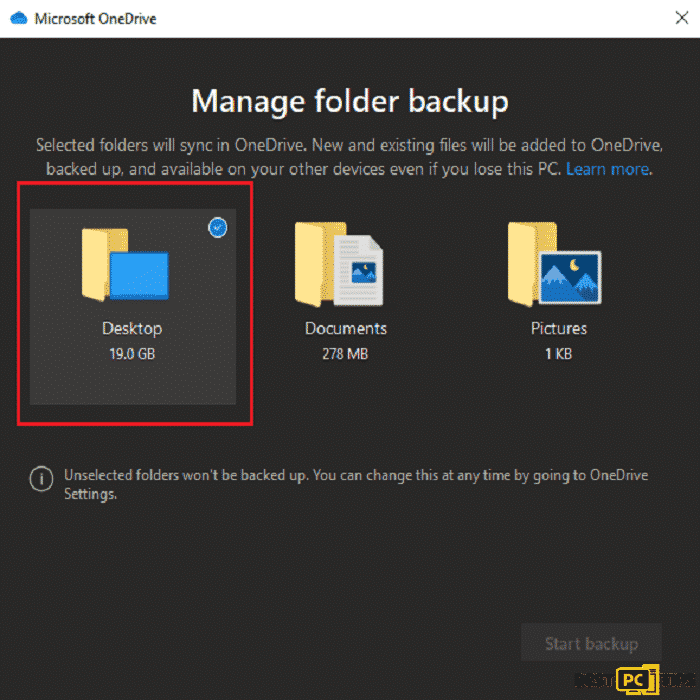
- Here, you can select to backup your Desktop and all files included.
- Click Start backup. Anytime you add a file to the Desktop, it will automatically be saved in OneDrive.
- If you wish to add folders or files, not on the Desktop, you can do so manually.
Restore Corrupted Files
OneDrives allows you to easily sync your PC to the cloud. In case of ransomware infection, you can download the last saved version from the cloud and you get at least the last time you sync. As another feature, Microsoft 365 also comes with a ransomware detection feature so your cloud is safe in case of attacks. This is a paid subscription but extremely helpful if you have a lot of important files.
Restore Your Entire OneDrive
If your OneDrive files get corrupted or deleted, you can restore them using these steps:
- Sign in with your account and click the cogwheel to access Settings.
- Click Options and choose to Restore Your OneDrive.
- Carefully select the correct dates from the drop-down list (Be sure to choose a date before the ransomware infection).
- Click Restore to retrieve all your last files.
Final Words
To keep your computer protected from online threats such as the Koom Ransomware, you should install a reliable anti-virus tool on your computer like iolo System Mechanic.
iolo System Mechanic uses a holistic approach to keep your computer running at its best as it blocks and removes threats from your computer and also automatically update your system drivers.
Offer
iolo System Mechanic® — is a patented PC & MAC repair tool & the only program of its kind. Not only it’s a registry fix, PC optimizer, or an anti-virus/malware remover – The iolo System Mechanic® technology reverses the damage done to Windows or Mac, eliminating the need for time-consuming reinstallations & costly technician bills.
It is available for FREE. Although, for some more advanced features & 100% effective fixes you may need to purchase a full license.
If the Koom Ransomware is still not removed — don’t hesitate and contact us via email, or a Facebook messenger (the blue ‘bubble’ on the bottom-right of your screen).