Decaf Ransomware-Virus Removal [FULL GUIDE]
Liam Park
Issue:I can't open any of my files and I got a threatening message! Please help!
My files are broken, I can't open them all anymore. I have very important files on my computer for my studies. The names of the files including my dear photos have been changed to DECAF. Please help me! I'm desperate.
The Decaf Ransomware is a type of malware that encrypts data and demands a fee in exchange for its recovery. To put it another way, this program makes files unavailable and demands money to regain access.
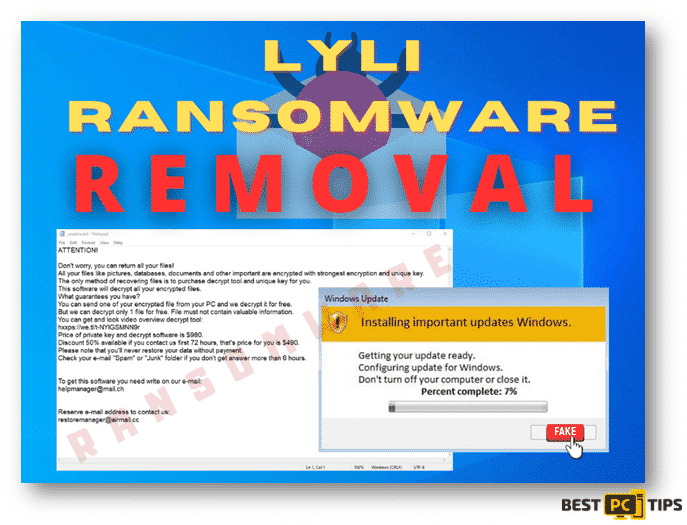
The ransom note notifies its victims that their data and files have been locked and backups have been erased. The only way to recover the data safely is to acquire decryption tools from cybercriminals. The message also gives free decryption of one encrypted to serve as proof that the encrypted data can be restored.

Unfortunately, without the involvement of cybercriminals, decryption is impossible in the majority of ransomware outbreaks. Despite paying, victims frequently do not obtain the decryption tools promised.
Decaf ransomware may be removed from the infected computer to prevent new encryptions, but it will not restore data that have already been encrypted. The only way to get them back is to use a backup that was made earlier and kept somewhere else.

To minimize irreversible data loss, it is extremely recommended that backups be kept on remote servers and/or disconnected storage devices (preferably, in many places).
Decaf Ransomware Distribution Methods
The majority of cyber threats, like Decaf Ransomware, are spread through dubious download sources including peer-to-peer file-sharing services, websites, and so on. Attackers can also get access to a user’s computer by displaying bogus upgrades and activation tools that are prohibited.
“Cracking” tools can also spread infections by activating licensed items through malicious channels instead of using legitimate ways. Infecting computers with illegal updaters involve exploiting software flaws and installing malicious software. Spam email campaigns may also be used to spread malware.
Infectious files might be attached to the malicious emails. These files can take on the form of Microsoft Office documents, PDFs, executable files, programs, and other formats. Whenever these files are opened or executed, whether intentionally or unintentionally, the infection chain begins.
Decaf Ransomware Threat Summary
| THREAT NAME | Decaf Ransomware |
| Type of Threat | Files Encryptor, Cryptocurrency Virus, Ransomware |
| Encrypted Files Extension | .decaf |
| Name of Ransom Note | README.txt |
| Amount of Ransom | Not stated, but the cybercriminals tell the victim to contact them by email and they will provide 1 free decryption to prove their legitimacy. |
| Contact Details of Cyber Criminal | ;@supersuso (ICQ) |
| Threat Symptoms and Potential Damage | Users will not be able to open the files on their system (locked files), file extensions will be replaced to .decaf. Users will be left with a ransom note by the ransomware developer and will be demanded to pay a certain amount to recover the victim’s files. |
| Method of Distribution | Malicious ads from untrustworthy websites, downloaded torrent files from unreliable websites, Macros or Infected email attachments |
| Suggested Removal Tool | If you think there is an infection in your system but have not yet seen the symptoms in your system, cyber security experts recommend using iolo System Mechanic to perform a holistic scan on your computer. |
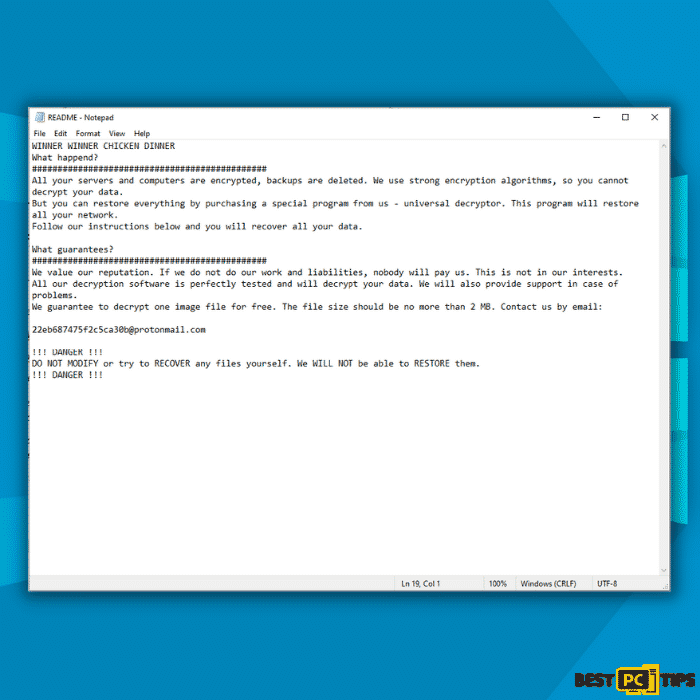
Here’s the content of Decaf Ransomware ransom message:
“WINNER WINNER CHICKEN DINNER
What happend?
##############################################
All your servers and computers are encrypted, backups are deleted. We use strong encryption algorithms, so you cannot decrypt your data.
But you can restore everything by purchasing a special program from us – universal decryptor. This program will restore all your network.
Follow our instructions below and you will recover all your data.
What guarantees?
##############################################
We value our reputation. If we do not do our work and liabilities, nobody will pay us. This is not in our interests.
All our decryption software is perfectly tested and will decrypt your data. We will also provide support in case of problems.
We guarantee to decrypt one image file for free. The file size should be no more than 2 MB. Contact us by email:
!!! DANGER !!!
DO NOT MODIFY or try to RECOVER any files yourself. We WILL NOT be able to RESTORE them.
!!! DANGER !!!“
Here’s a screenshot of the ransom note from Decaf Ransomware:
How You Can Stay Safe from the Decaf Ransomware?
It is suggested that you only download from official/verified sources. All apps must be enabled and updated with the use of reputable developers’ tools. Emails that appear to be suspicious or unconnected should not be opened, especially if they include links or attachments.
It is vital to install and keep up to date a reliable anti-virus/anti-spyware application. This program must be run on a regular basis to scan the device and remove threats. If your computer has already been infected by Decaf Malware, we recommend doing a comprehensive system scan with iolo System Mechanic to immediately remove the ransomware.
Report Cyber Crimes to the Authorities
It is strongly advised that victims of ransomware attacks notify authorities as soon as possible. Giving information to law enforcers will aid in the prevention of cybercrime and will aid in the punishment of hackers. Here is a list of contact information to call to report these incidents:
- USA – Internet Crime Complaint Centre IC3
- United Kingdom – Action Fraud
- Spain – Policía Nacional
- France – Ministère de l’Intérieur
- Germany – Polizei
- Italy – Polizia di Stato
- The Netherlands – Politie
- Poland – Policja
- Portugal – Polícia Judiciária
Fast and Automatic Decaf Ransomware Removal with iolo System Mechanic
If you don’t want to deal with the stress and hassle of manually cleaning infections, iolo System Mechanic is a fantastic solution. It’s a malware and virus detection and removal program as well as a system optimization tool that not only protects your computer from online threats but also keeps it up to date.
Decaf Ransomware Manual Removal Instructions
If you happen to notice that your computer is infected with the Decaf Ransomware, you have to make sure that it does not spread to other devices in your network. To do this, you have to isolate the infected device away from the other devices that are connected to your computer and the network.
#1: Disconnect From Your Network
Step 1: Hold down the “Windows” + “R” keys and type in “ncpa.cpl” in the run command line and click “OK”
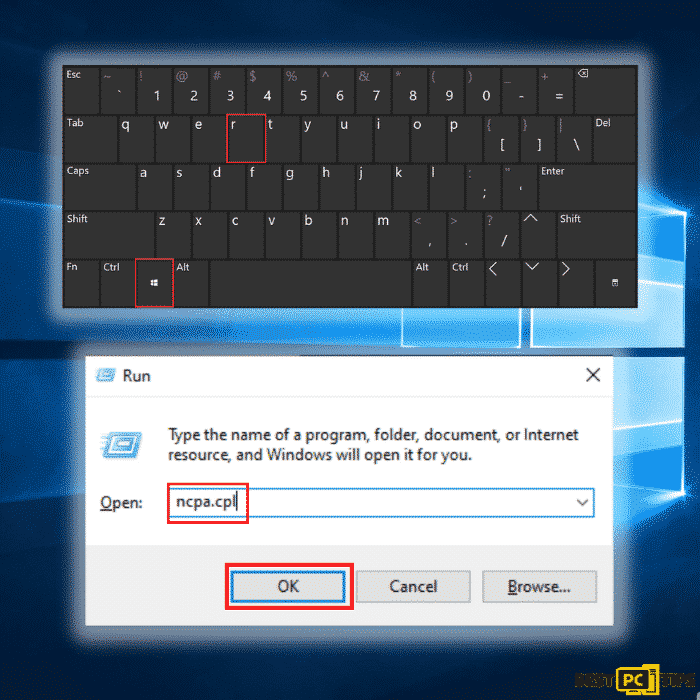
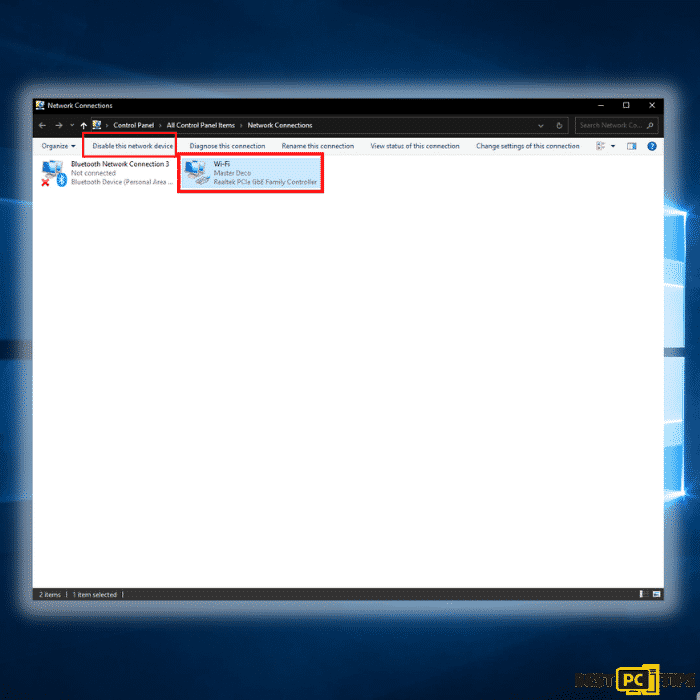
Step 2: Click on the network that you are connected to and click on “Disable this network”
#2: Unplug All Connected Storage Devices from the Computer
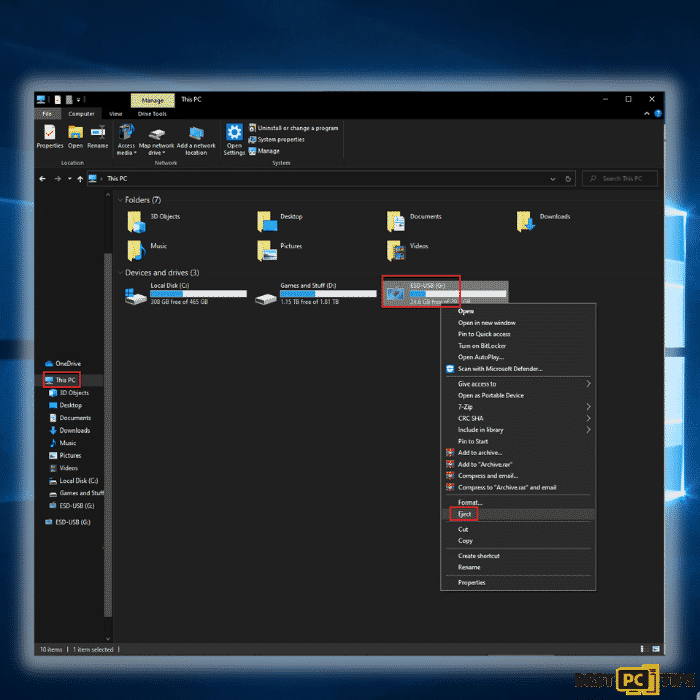
The Decaf Ransomware, as previously stated, encrypts data and infiltrates all storage devices attached to the computer. As a result, all external storage such as external hard drives, flash drives, and other similar devices should be detached as soon as possible. To avoid data corruption, we strongly encourage you to remove each device before disconnecting.
Step 1: Open “This PC” and locate all the connected storage devices. Right-click on it and click “Eject”
#3: Disconnect from Your Cloud Storage Devices
Some ransomware variants may be able to take control of software that manages data saved in your cloud storage. As a result, internet attacks like Decaf Ransomware could infect the information. As a result, you should log out of any cloud storage accounts you have in your browsers and other software. You should also uninstall the cloud-management application installed on your computer until the threat has been eliminated.
#4: Look for a Decryption Tool for the Files Infected by Decaf Ransomware
Most ransomware-type attacks use incredibly advanced encryption methods, and only the developer can restore the encrypted data. This is due to the fact that decryption needs the usage of a unique key that is only generated during the encryption process. It’s difficult to recover data without the key. Instead of using the infected system as a host, fraudsters would usually store the restoration keys on a remote server.
Phobos, Dharma and other varieties of ransomware attacks are almost perfect, making data recovery impossible without the cooperation of the developers. Nevertheless, there are many ransomware viruses that are poorly created and full of loopholes. As a result, if ransomware infects your machine, you should look for available decryption programs that can effectively remove it from your computer.
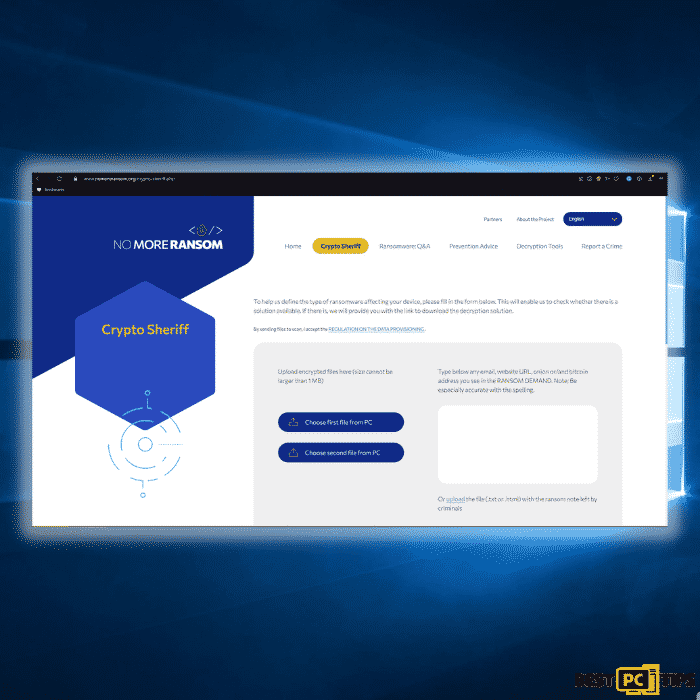
It can be difficult to find the right decryption tool. As a result, we highly suggest that you use the No More Ransom Project. There is a “Decryption Tools” section on the website with a search bar. You can enter the name of the ransomware to see a list of all available decrypting tools for Decaf Ransomware.
#5: Keep Your Files and Data Safely Stored
If you were able to successfully remove the Decaf Ransomware from your computer, now is the time to back up your files to cloud storage or a removable storage device. In this way, in case your computer gets infected again then you will have all your files stored in a safe place. However, you have to remember that you should not plug your storage device or log in to your cloud storage while your computer has not yet been fully rid of any threats.
#6: Data Backup Options
External Storage Devices – Using an external storage device and keeping it unplugged is one of the most reliable backup techniques. Please copy all your important files and data to an external storage device such as an external SSD/HDD or flash drive, then unplug it and keep it in a dry, cool location away from the sun. This strategy, however, is inefficient because data backups and upgrades must be performed frequently.
Cloud Storage Services – We recommend keeping a backup of your files with Microsoft OneDrive. OneDrive allows you to store important files and data in the cloud and sync files between your computer and mobile devices. You can also access and edit files from any Windows device and other devices with OneDrive. OneDrive allows you to save, share, and preview files, as well as see your download history, rename, move and delete files, and create new folders.
On your PC, you can make a backup of your most important folders and files. The File versioning feature will also let you keep older versions of files for up to 30 days. OneDrive has a recycle bin where you can store the deleted files for a limited period.
OneDrive offers 5 GB of free storage with subscription-based storage choices of 100 GB, 1 TB, and 6 TB available. These storage plans are available either as a standalone purchase or as part of an Office 365 subscription.

Final Words
Installing a trustworthy anti-virus solution on your computer is the best method to avoid becoming infested with any online dangers like Decaf Ransomware. iolo System Mechanic is a good choice since it not only defends your computer but also repairs any files that have been harmed by the virus.
Offer
iolo System Mechanic® — is a patented PC & MAC repair tool & the only program of its kind. Not only it’s a registry fix, PC optimizer, or an anti-virus/malware remover – The iolo System Mechanic® technology reverses the damage done to Windows or Mac, eliminating the need for time-consuming reinstallations & costly technician bills.
It is available for FREE. Although, for some more advanced features & 100% effective fixes you may need to purchase a full license.
If the Decaf Ransomware is still not removed — don’t hesitate and contact us via email, or a Facebook messenger (the blue ‘bubble’ on the bottom-right of your screen).