“MONETA” Ransomware Removal Guide (Effective Instructions)
Lina P.
Issue:All of my files were stolen and encrypted with .moneta extension. How can I recover from this virus?
Hello,
I think all of my PC files were stolen... All of them are encrypted with ".moneta" extension and hackers are demanding a ransom.
I don't know what should I do. Is there a way to fix this issue without paying the virus creators?
Thank you.
The MONETA Ransomware is a type of cryptovirus that encrypts all of the files and data that are in the infected computer. Once it has completely infiltrated the machine, the developers have made sure that the victim will contact them by leaving a ransom note that demands payment. After payment is made, the cybercriminals will exchange will provide the victim with the decryption key that is used to unlock the encrypted files and make it usable once again.
The MONETA Ransomware is a variant of the Phobos ransomware family which had previous versions namely .google, 1500dollars, HOTEL ransomware, and a lot more.
How Does MONETA Ransomware Infect Your System
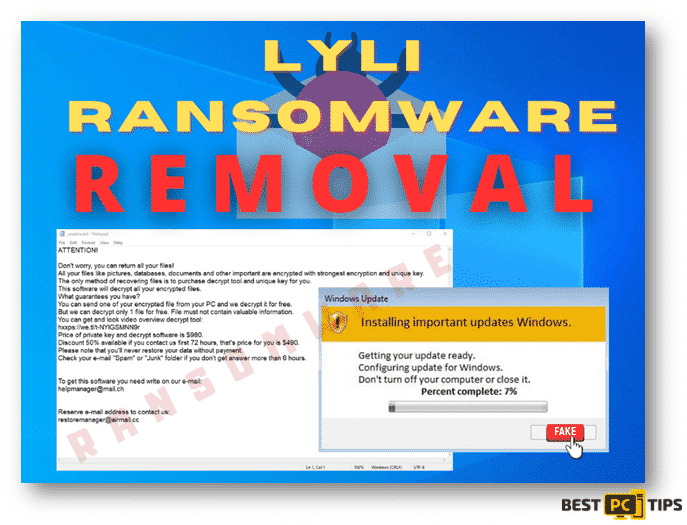
Just like most ransomware, the MONETA ransomware locks infected files and changes the extensions of the files. Once all the files on the infected machine are encrypted, the ransom note will be put on the desktop in a text file with a file name of “info.txt” and a pop-up will also appear.
Here’s a screenshot and a quote of the ransom note:
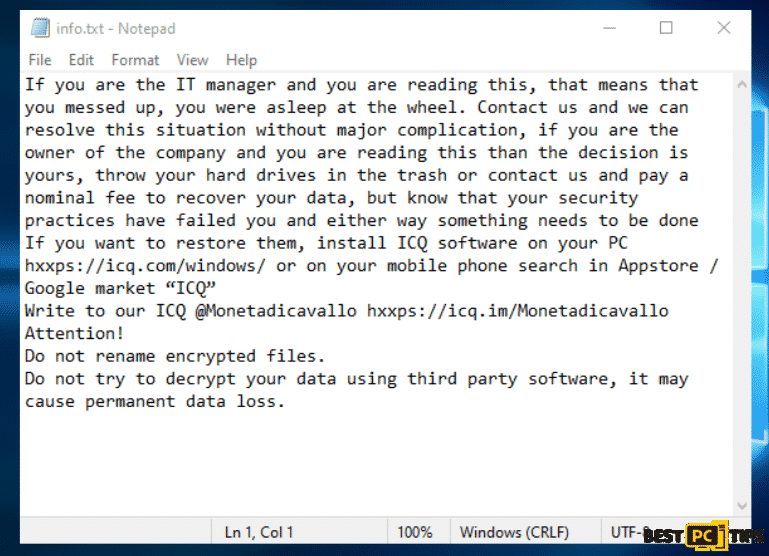
“If you are the IT manager and you are reading this, that means that you messed up, you were asleep at the wheel. Contact us and we can resolve this situation without major complication, if you are the owner of the company and you are reading this than the decision is yours, throw your hard drives in the trash or contact us and pay a nominal fee to recover your data, but know that your security practices have failed you and either way something needs to be done
If you want to restore them, install ICQ software on your PC https://icq.com/windows/ or on your mobile phone search in Appstore / Google market “ICQ”
Write to our ICQ @Monetadicavallo https://icq.im/Monetadicavallo
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.”
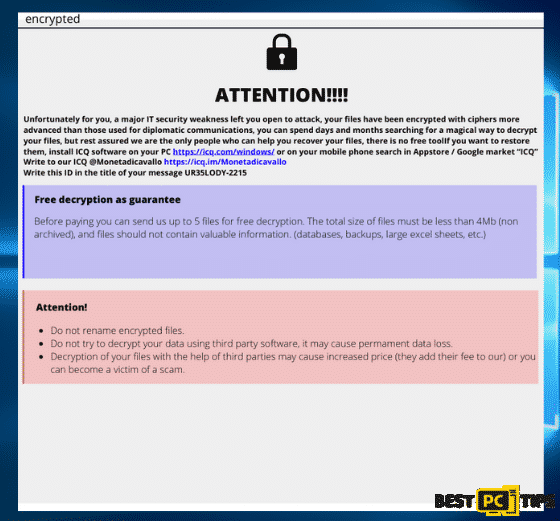
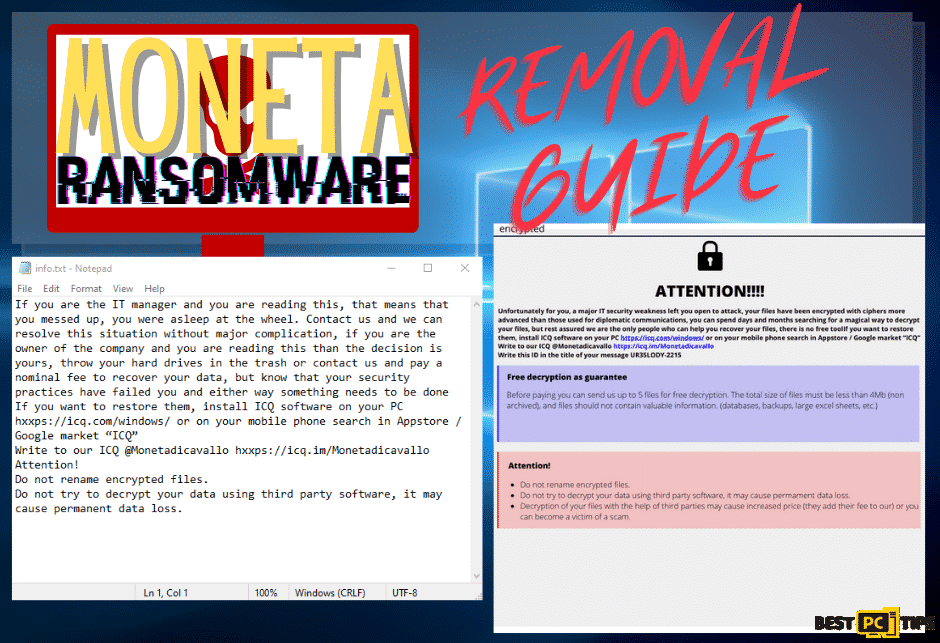
“ATTENTION!!!!
Unfortunately for you, a major IT security weakness left you open to attack, your files have been encrypted with ciphers more advanced than those used for diplomatic communications, you can spend days and months searching for a magical way to decrypt your files, but rest assured we are the only people who can help you recover your files, there is no free tool
If you want to restore them, install ICQ software on your PC hxxps://icq.com/windows/ or on your mobile phone search in Appstore / Google market “ICQ”
Write to our ICQ @Monetadicavallo https://icq.im/Monetadicavallo
Write this ID in the title of your message –
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 4Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.“
Threat Summary
| Threat Name | MONETA Ransomware |
| Threat Type | Cryptovirus/Ransomware |
| Known Associates | Phobos ransomware family |
| Ransom Note | info.txt and the user will see a pop-up window in their desktop |
| Extension File | .id[user ID].[ICQ_Monetadicavallo].MONETA extension |
| Contact Details | The victim should install ICQ on their computer by going to https://icq.com/windows/ or download the ICQ app in the appstore or Google playstore and contact them at ICQ @Monetadicavallo https://icq.im/Monetadicavallo |
| Removal | Running a full system scan using a legitimate and reliable anti-virus tool such as iolo System Mechanic |
Just like the predecessors of MONETA ransomware, uses an AES military grade algorithm to encrypt the infected files. With this type of encryption method, the encrypted files and data cannot be unlocked without the appropriate decryption tool.
The best way to deal with the MONETA ransomware is to remove it from the infected machine. Although the cyber criminals behind this ransomware promises to provide a fix for a certain amount, cyber security experts strongly discourage contacting them. Instead, invest in getting a reliable anti-virus tool such as iolo System Mechanic.
How to Avoid Getting Infected with MONETA Ransomware?
- Email Attachments from Spam Emails – One of the most common ways to get infected with any viruses is through clicking or opening attachments from spam emails. If you happen to receive any suspicious emails from unknown senders, it is wise to delete the email right away to avoid accidentally opening it.
- Avoid Downloading and Installing Pirated Software – Viruses are bundled together with pirated applications and software. This means that when a pirated program is installed to a computer, chances are there is also a virus installed together with the program.That is why we strongly encourage downloading and installing legitimate applications.
- Do Not Visit Suspicious Websites – If you go to a website and see offers that are too good to be true, then you should steer completely away from it. There are websites that will offer items and services that are ridiculously cheap. Most of the time, these websites are just trying to scam their visitors.
- Install a Reliable Anti-Virus Tool – To avoid going through the hassle of removing viruses from an infected computer, we strongly suggest using a decent and respectable anti-virus tool such as iolo System Mechanic. iolo System Mechanic offers a comprehensive anti-virus approach towards virus detection and removal.
MONETA Ransomware Removal Guide
The most effective way to use any tools to remove viruses or malwares is through booting your system in “Safe Mode”. It boots your Windows Operating system into a special mode that loads only minimal and important drivers, Windows services and it also does not load unnecessary applications automatically.
OPTION 1. Here Are The Steps On How You Can Remove MONETA Ransomware or Any Other Ransomware via “Safe Mode with Networking”
for Windows 7/Vista/XP
- Click on the “Start” button on the lower left corner of your screen, then click on the arrow next to “Shutdown”, click on “Restart” and finally click “OK” to confirm.
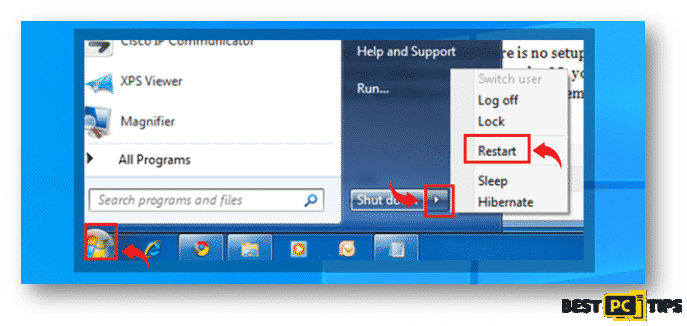
2. While your computer is trying to boot back up, start on tapping the “F8” button on your keyboard once every second until the “Advanced Boot Options” comes on your screen.
3. In the “Advanced Boot Options” screen, use the arrow keys to select “Safe Mode with Networking” and then press enter to choose
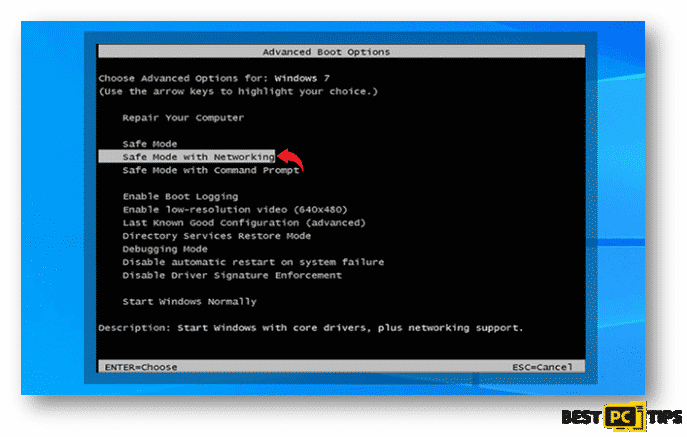
for Windows 10/Windows 8
Note: You may also follow the same steps that have been provided above
- Click on the “Windows” icon on the bottom left had side of your screen. While holding the “Shift” key, click on the “Power” button and click on “Restart”
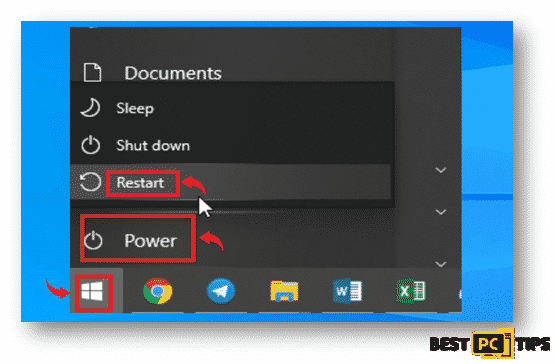
- In the Troubleshoot Screen, click on “Advanced Options”
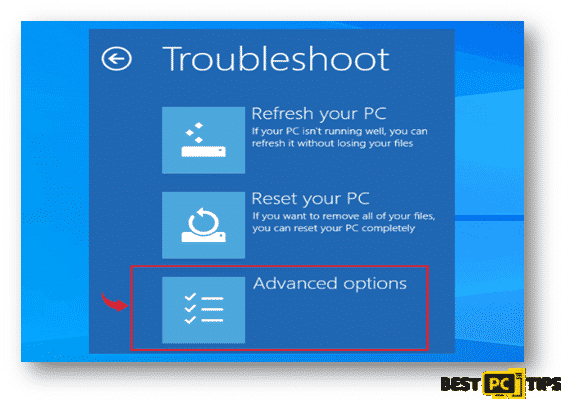
- After selecting “Advanced Options”, you will be brought to the “Startup Settings” screen. In the list of options, select “Enable Safe Mode with Networking”
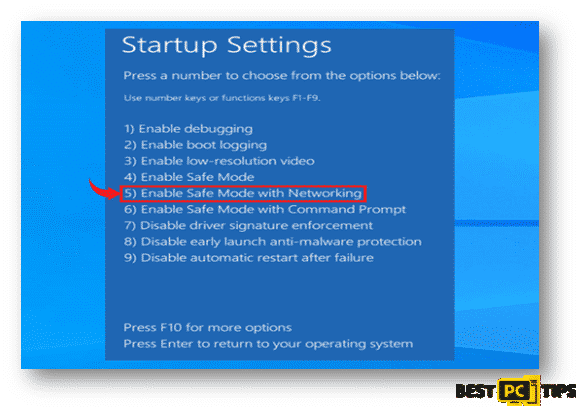
Once your system has booted into Safe Mode with Networking, login to your account and download your preferred Anti-Malware software. Make sure to update the Anti-Malware software of your choice in order for it to update its virus definition database. Once the Anti-Malware software is updated, go ahead and let it scan your machine and follow any other steps required to complete the virus removal in your computer.
OPTION 2. Removing MONETA Ransomware or Any Other Ransomware With “Windows System Restore“
System restore is a built-in feature in Windows Operating System that allows its users to revert back to a state when their computer were working properly. This will help users to recover from disastrous data loss due to viruses.
for Windows 7/Vista/XP
- Click on the “Start” button on the lower left corner of your screen, then click on the arrow next to “Shutdown”, click on “Restart” and finally click “OK” to confirm.
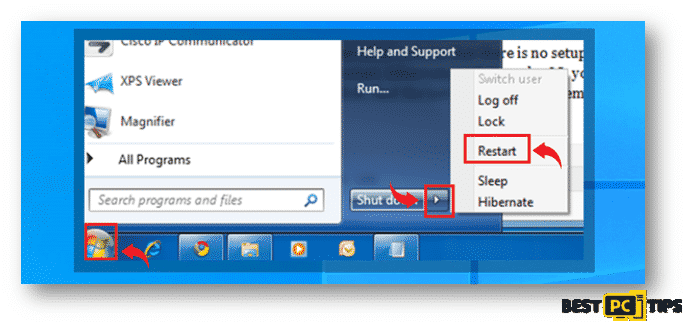
- While your computer is trying to boot back up, start on tapping the “F8” button on your keyboard once every second until the “Advanced Boot Options” comes on your screen.
- In the “Advanced Boot Options” screen, use the arrow keys to select “Safe Mode with Command Prompt” and then press enter to choose
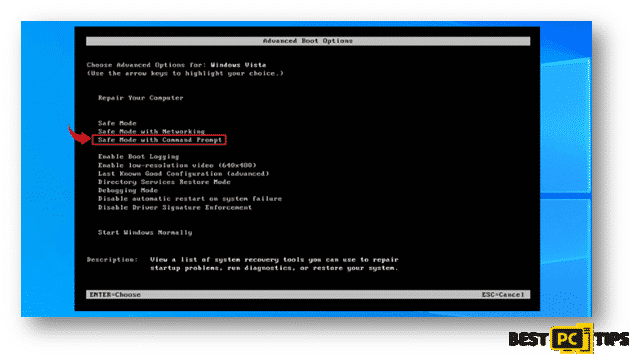
for Windows 10/Windows 8
Note: You may also follow the same steps that have been provided above
- Click on the “Windows” icon on the bottom left had side of your screen. While holding the “Shift” key, click on the “Power” button and click on “Restart”
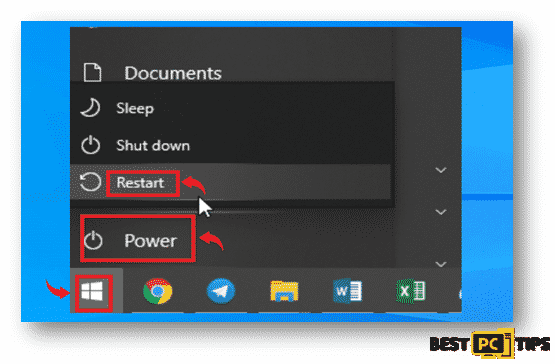
- In the Troubleshoot Screen, click on “Advanced Options”
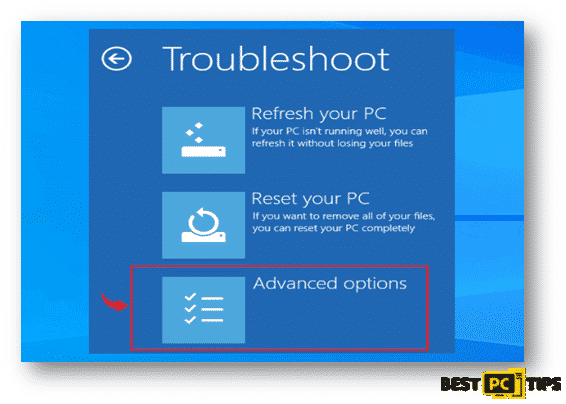
- After selecting “Advanced Options”, you will be brought to the “Startup Settings” screen. In the list of options, select “Enable Safe Mode with Command Prompt”
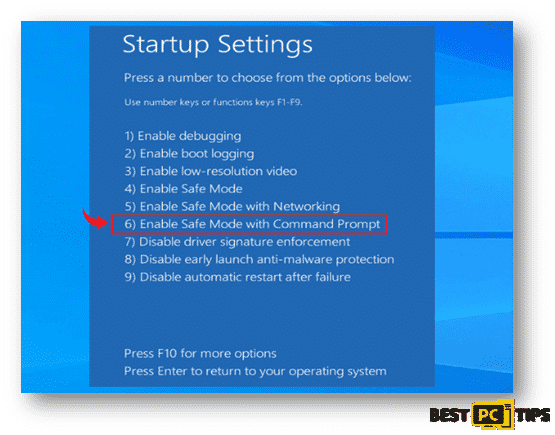
Restoring your Files and other Settings
- In the “Command Prompt” window, type in “cd restore” and press enter, and in the next line type in “rstrui.exe” and press enter once again
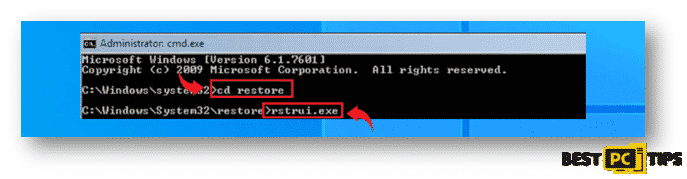
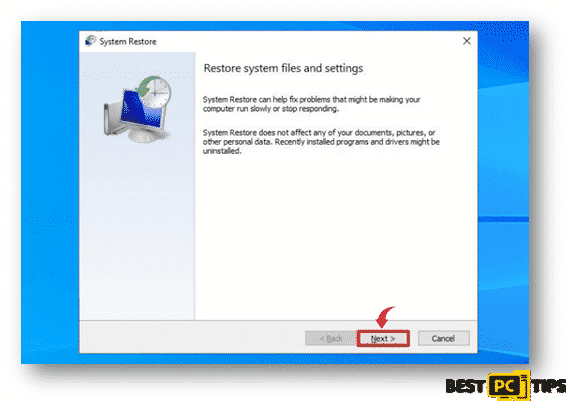
- You will see the “System Restore” screen on the next window, simply click on “Next” and select your preferred restore point. Its ideal to select a restore point when the Virus has not yet infiltrated your system.
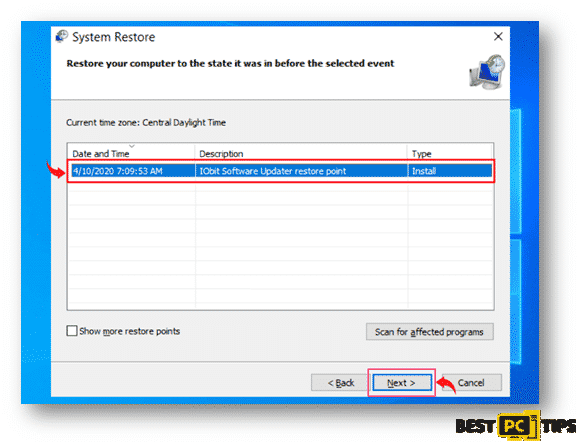
- In the confirmation screen, click “Yes” to confirm.
OPTION 3. Windows Previous Versions Method
After completing the System Restore process, you use the Windows Previous Versions feature in order to restore files individually.
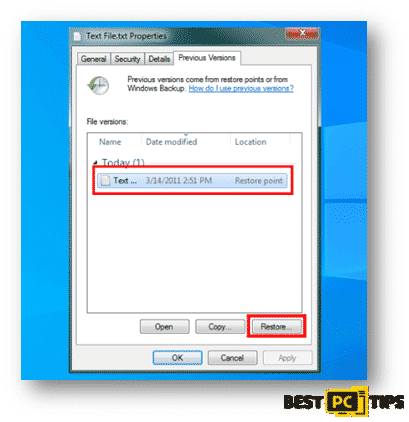
• Select an encrypted file in your system and right click on it
• Click on “Properties” and click on the “Previous Versions” tab
• In “Folder Versions”, select each of the available copes and click restore.
Recover Shadow Volume Copies through Shadow Explorer
There’s a chance to recover encrypted files if shadow volume copies were not compromised by the infection. Follow these steps to use Shadow Explorer.
- Click here to download Shadow Explorer
- Continue with the installation of Shadow Explorer once the download is complete
- Once Shadow Explorer is installed, launch the application and select the driver that you want to scan and right click the folder that you wish to recover and click “Export” and select the location where you want to save it.
Our Final Recommendations
To avoid going through the hassle of removing threats from your computer and recovering working copies of your files, we strongly encourage every internet user to install reliable anti-virus software.
There are hundreds of anti-virus tools that are available however, there are only a few that works as they should be. iolo System Mechanic is one of the few anti-malware tool that we trust as it offers an all-in-one approach when it comes to keeping your computer safe from viruses.
Offer
iolo System Mechanic® — is a patented PC & MAC repair tool & the only program of its kind. Not only it’s a registry fix, PC optimizer, or an anti-virus/malware remover – The iolo System Mechanic® technology reverses the damage done to Windows or Mac, eliminating the need for time-consuming reinstallations & costly technician bills.
It is available for FREE. Although, for some more advanced features & 100% effective fixes you may need to purchase a full license.
If your MONETA ransomware virus is still not removed — don’t hesitate and contact us via email, or a Facebook messenger (the blue ‘bubble’ on the bottom-right of your screen).