Remove the Clhmotjdxp Ransomware & Recover Your Files (Guide)
Robert
Issue:I had my files encrypted to .clhmotjdxp and now they're asking me to pay money to restore them
Hello,
just the other day i saw that some of my files had the .Clhmotjdxp extension and can't be opened. I then saw a ransom note that if I don't send bitcoin to someone -- my files will be lost.
Can I fix this somehow cheaper?
One of the pesky ransomwares that has been plaguing a lot of Windows Operating System users is the Clhmotjdxp Ransomware. It affects infected systems by encrypting files and data and leaves a ransom note that demands a payment from the victims.
The Clhmotjdxp Ransomware infects the infected system by encrypting the files in the system prohibiting the users to open and use them. It affects not only files and data in the system itself but also files that are in external devices and cloud storage that are connected to the infected system. Aside from locking the files in the system, the Clhmotjdxp Ransomware also decreases the performance and security of the infected system, thus making it more vulnerable to other viruses.
Clhmotjdxp Ransomware Ransom Note
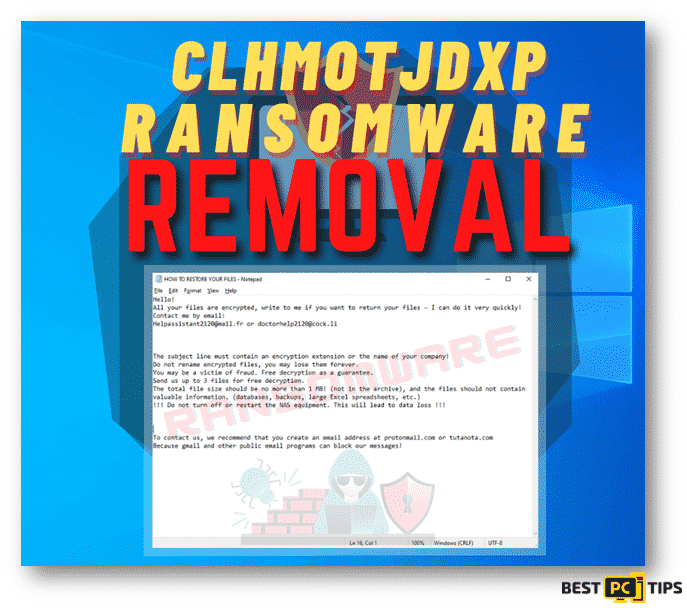
Just like any other ransomware, the cyber criminals who are behind the Clhmotjdxp Ransomware demands for a payment in order for you to recover your files. The victims can find the ransom note on a text file under the name of “HOW TO RESTORE YOUR FILES.TXT” which can be opened with Notepad.
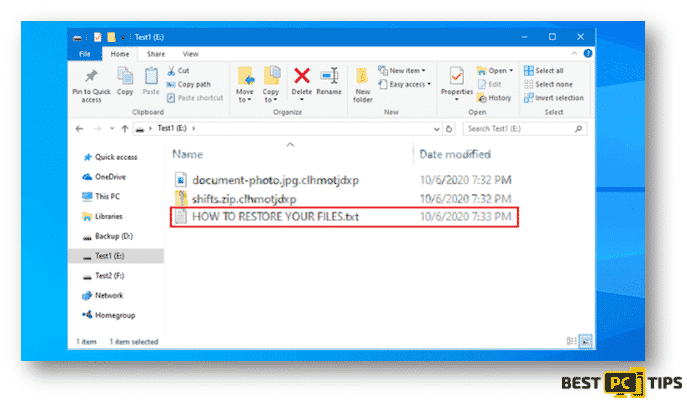
The contents of the message are typical to most ransomware. The developers behind the Clhmotjdxp Ransomware will ask the victim to contact them via email if you want your files to be returned back to you and it also contains instructions on how you can contact them. Here’s a screenshot of that message.
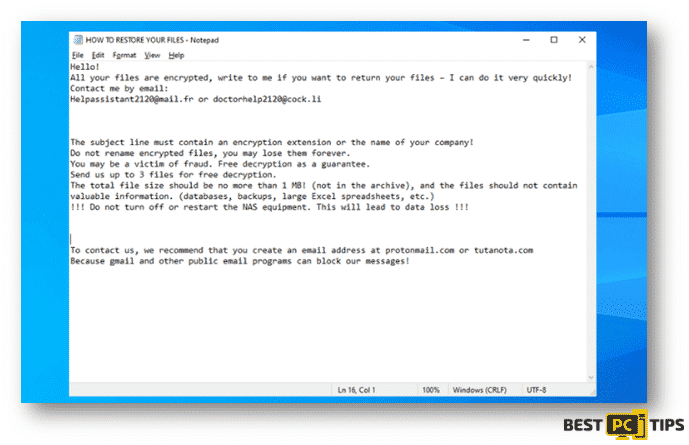
Ransom Message Contents:
“Hello!
All your files are encrypted, write to me if you want to return your files – I can do it very quickly!
Contact me by email:
[email protected] or [email protected]
The subject line must contain an encryption extension or the name of your company!
Do not rename encrypted files, you may lose them forever.
You may be a victim of fraud. Free decryption as a guarantee.
Send us up to 3 files for free decryption.
The total file size should be no more than 1 MB! (not in the archive), and the files should not contain valuable information. (databases, backups, large Excel spreadsheets, etc.)
!!! Do not turn off or restart the NAS equipment. This will lead to data loss !!!
To contact us, we recommend that you create an email address at protonmail.com or tutanota.com
Because gmail and other public email programs can block our messages!”
Although this message from the cybercriminals may sound reassuring that the victim can’t recover their files, security experts strongly discourage contacting them. Just like what is stated in the message, they can decrypt up to 3 files for free, however, in order for you to decrypt and use the rest of your files, they will demand for payment. Just like any other cyber criminals, the developers of Clhmotjdxp Ransomware are not to be trusted. There’s no guarantee that they will send the steps and tools on how to decrypt the infected files once the victim has sent the payment.
Here’s a summary of Clhmotjdxp ransomware:
Summary of the Security Threat
| Security Threat Name | Clhmotjdxp Ransomware |
| Affiliation | Snatch ransomware Family |
| File Extension | Infected files will be renamed with an extension name of .clhmotjdxp |
| Ransom Note File | HOW TO RESTORE YOUR FILES.txt |
| Contact Details | [email protected] and [email protected] |
| Distribution Methods | Spam email attachments, malicious website pop-ups, bundled with malicious application installations |
| Removal | Using a reliable anti-malware software has proven to detect and remove the threat |
| Repair | Once the system is infected with this threat, it corrupts some files and the only way to repair them is to Reimage them |
Proper Approach to Eliminating Clhmotjdxp Ransomware
Using the right tools to detect and remove the Clhmotjdxp Ransomware threat on any machine is very important to lessen the damage that it can inflict. An infection such as this can spread and activate malicious scripts that will make the machine more vulnerable to other attacks and viruses. With the help of a reliable anti-malware tool, early detection can block the spread of the Clhmotjdxp Ransomware in the machine and potentially saving the user from the hassle of removing and recovering affected files.
Some of the tools that cyber security experts recommend are iolo System Mechanic. This tool can run a full system scan and notify the user about any infection that is already infesting the machine and other potential threats. Also, it will effectively remove it and restore any corrupted files.
However, if you feel tech-savvy enough you can try removing the ransomware manually.
Steps and Guide on Removing Clhmotjdxp Ransomware Manually:
Using Anti-Malware Tools Through Safemode with Networking
Booting the system into “Safe Mode with Networking” is the most effective way to use any anti-malware tools. It boots the system into a special mode and will only load important drivers that Windows need in order for it to work.
Here’s our guide on how to boot into “Safe Mode with Networking”:
Windows 7/Vista/XP:
- Press the “Start” button located on the lower-left corner of your desktop screen and click the arrow that is next located next to the “Shutdown” button, press “Restart” and click “OK”.
- Tap on the “F8” on your keyboard once per second while the computer is booting up and the “Advanced Boot Options” will come up on the screen.
- To highlight the “Safe Mode with Networking” in the “Advanced Boot Options”, use the arrow keys on the keyboard and press enter to select it.
Windows 10/Windows 8:
Note: For Windows 10 and Windows 8 operating system, you may follow the same steps indicated above.
- Press on the “Start” or “Windows” logo located on the bottom left corner of the desktop screen. Hold down the “Shift” key on your keyboard, click the “Power” button and then click “Restart”
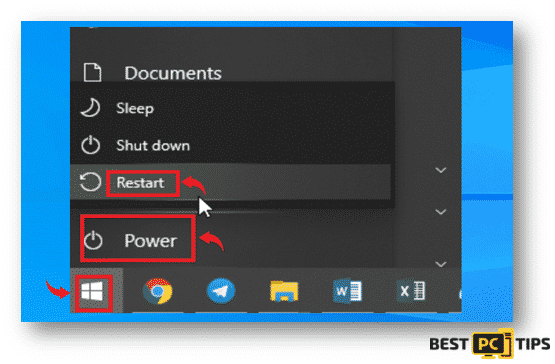
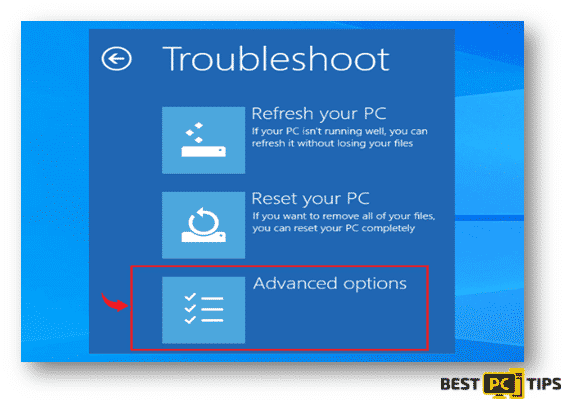
- The system will reboot and will show the Troubleshoot Screen. Select the “Advanced Options” menu.
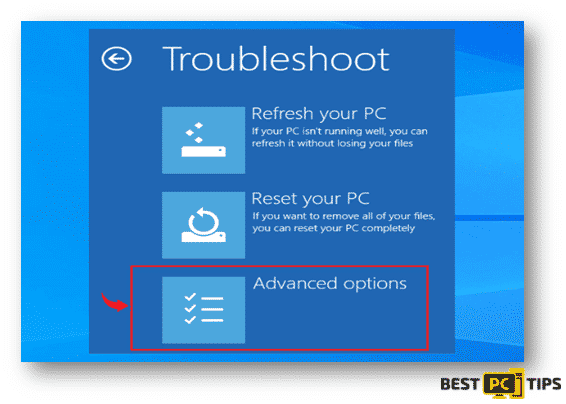
- On the next screen, you will see the “Startup Settings” window. Select the “Enable Safe Mode with Networking”
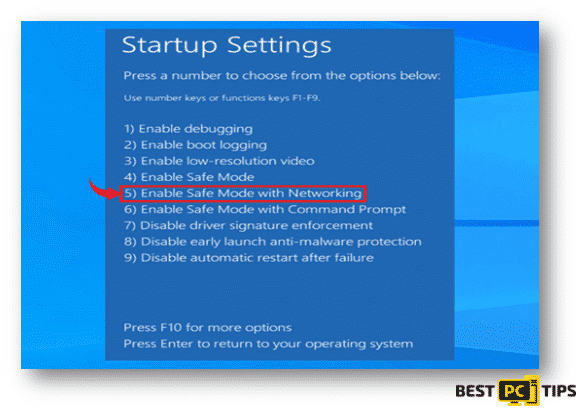
Once logged into “Safe Mode with Networking”, open your preferred Anti-Malware tool (we recommend iolo System Mechanic) and make sure to update it before doing a full system scan. If for some reason, this does not work you can try the next method in our guide.
Eliminating Clhmotjdxp Ransomware with System Restore
An effective tool that victims can use is the Windows System Restore. It is feature that comes with Windows which lets their users revert back their computer to a time when it was working properly. It is much useful during catastrophic data losses or system corruption.
Follow these steps to do a “System Restore”:
Windows 7/Vista/XP:
- Press the “Start” button located on the lower left corner of your desktop screen and click the arrow that is next located next to the “Shutdown” button, press “Restart” and click “OK”.
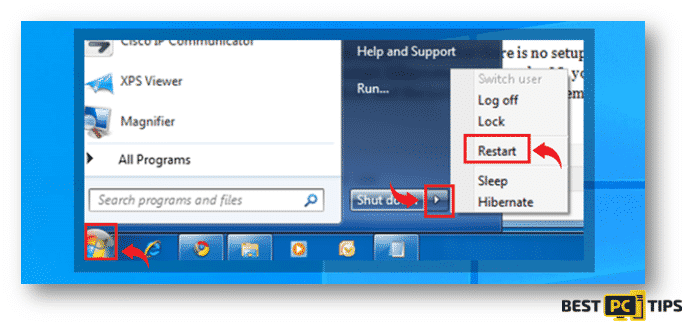
- Tap on the “F8” on your keyboard once per second while the computer is booting up and the “Advanced Boot Options” will come up on the screen.
- Highlight the “Safe Mode with Command Prompt” in the “Advanced Boot Options”, use the arrow keys on the keyboard and press enter to select it.
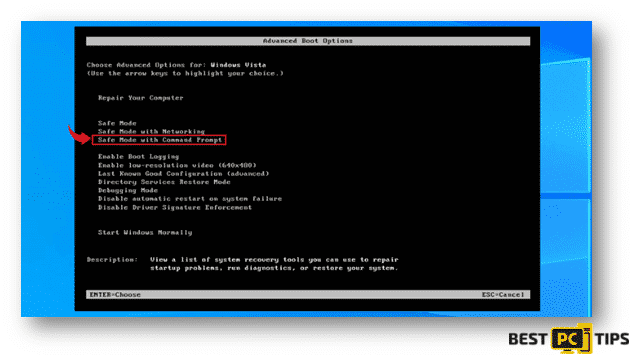
Windows 10/Windows 8:
Note: For Windows 10 and Windows 8 operating system, you may follow the same steps indicated above as well.
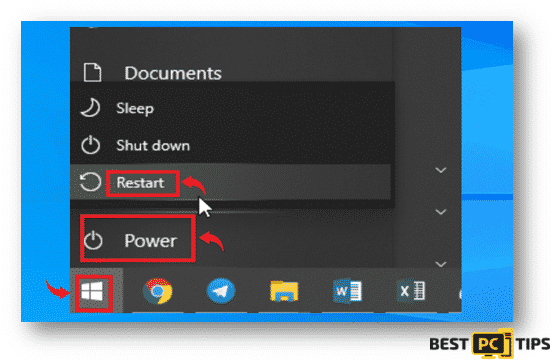
- Press on the “Start” or “Windows” logo located on the bottom left corner of the desktop screen. Hold down the “Shift” key on your keyboard, click the “Power” button and then click “Restart”
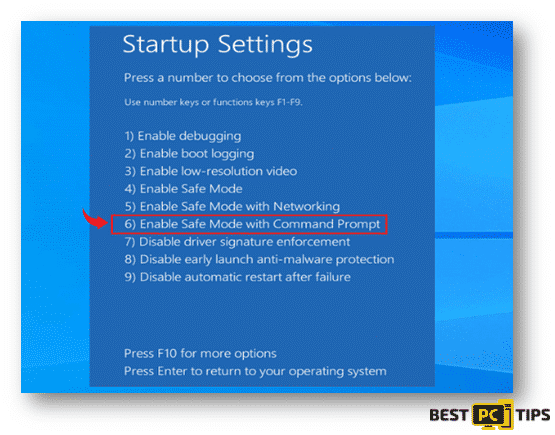
- On the next screen, you will see the “StartupSettings” window. Select the “Enable Safe Mode with Command Prompt”
- On the next screen, you will see the “Startup Settings” window. Select the “Enable Safe Mode with Command Prompt”
On the next steps, we will show you how you can start the “System Restore” process.
- Type in “cd restore” in the “Command Prompt” window and press enter and type in “rstui.exe” in the next line and press enter again.
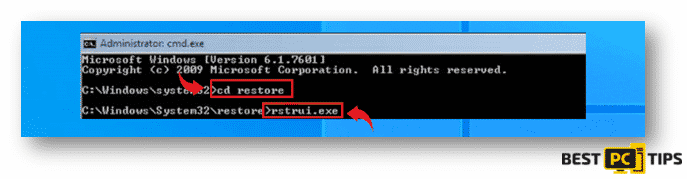
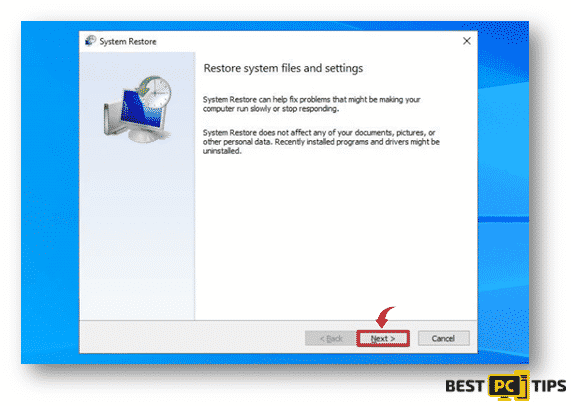
- The “SystemRestore” window will be shown on the next screen, click on the “Next” button and select the best restore point on your system. It is best to select the point when the system was working perfectly.
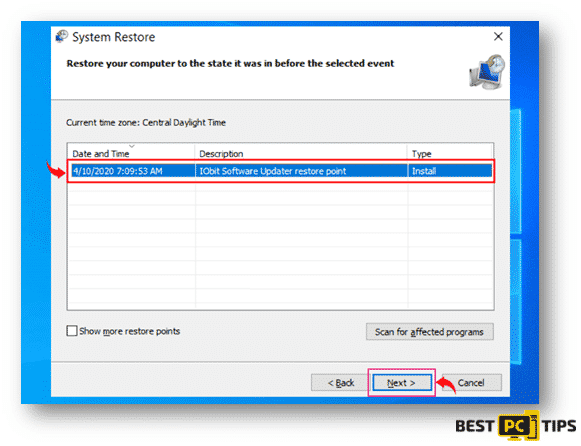
- Lastly, click on “Yes” on the next screen to confirm the restore point that you have selected.
After the system has fully restored to the selected restore point, it is best to run a full system scan once again using your preferred Anti-malware tool to make sure that the system has been cleaned out of the ClhmotjdxpRansomware.
Restoring Files and Data Recovery
Removing the Clhmotjdxp Ransomware from an infected machine is one part of making the infected system up and running normally again, however, recovering the data from the infected machine is another. Not being able to recover your files is pretty much the same as reformatting your machine since you will be left with nothing even after the ransomware has been removed from the system. Reformatting is basically reverting the machine back into the state when the machine did not have any applications, files, and programs installed.
Below are some steps that you can follow to possibly recover your files.
Using Data Recovery Pro
- Click this link to download Using Data Recovery Pro
- Follow the installation steps of Data Recovery Setup

- Once installed, launch the program, select the location that you want to scan and click “Start”
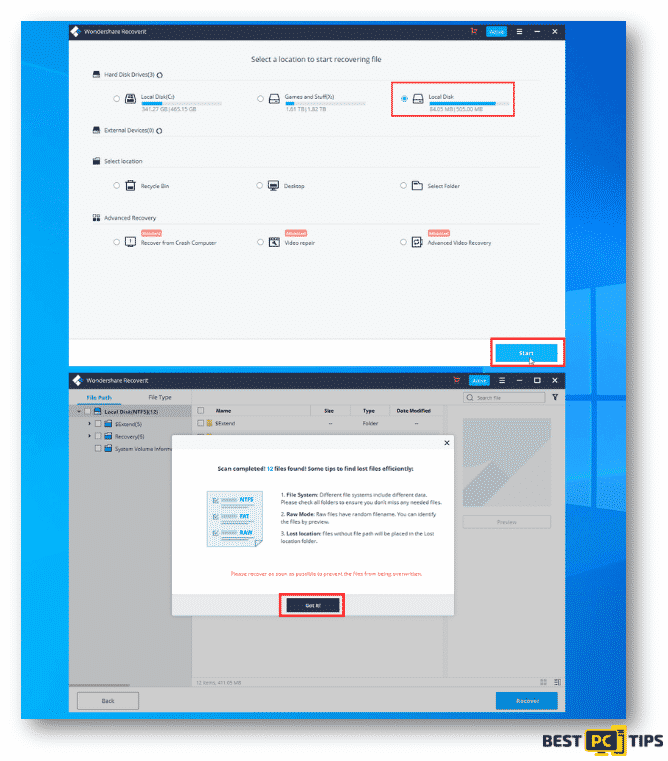
Once the scan is complete, you can restore the files and save them to your preferred location
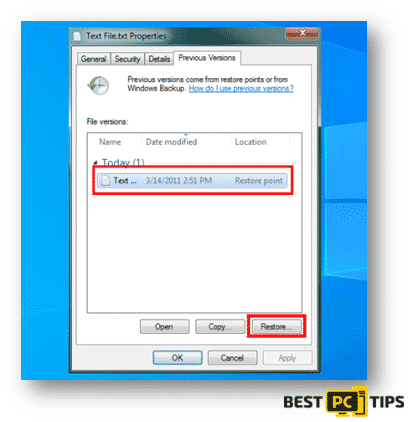
Windows Previous Versions
After completing the System Restore process, you use the Windows Previous Versions feature in order to restore files individually.
- Select an encrypted file in your system and right click on it
- Click on “Properties” and click on the “Previous Versions” tab
- In “Folder Versions”, select each of the available copes and click restore.
Recover Shadow Volume Copies Through Shadow Explorer
There’s a chance to recover encrypted files if shadow volume copies were not compromised by the infection. Follow these steps to use Shadow Explorer.
- Click here to download Shadow Explorer
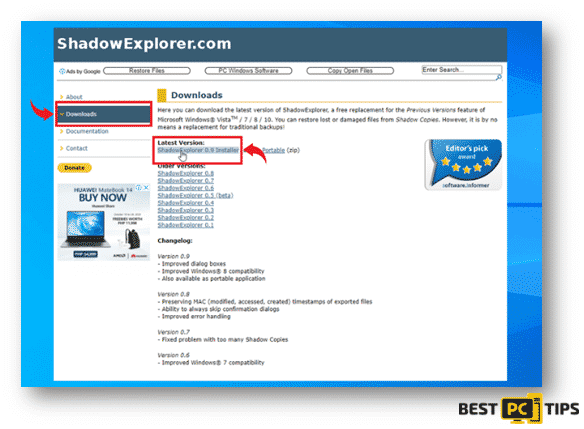
- Continue with the installation of Shadow Explorer once the download is complete
- Once Shadow Explorer is installed, launch the application and select the driver that you want to scan and right-click the folder that you wish to recover and click “Export” and select the location where you want to save it.
Conclusion & Automatic Malware Removal
Decryption tools for Clhmotjdxp Ransomware Virus have not yet been developed yet, that is why everyone needs to be very vigilant in using the internet, downloading files, and installing programs. The most effective way to avoid getting infected with any virus or ransomware is to install a reliable anti-virus or anti-malware software such as iolo System Mechanic. Users will be notified of any suspicious activities in the system and block them lets the user know if they want to allow it on the system or remove it. That is the beauty of having anti-virus software installed.
Offer
iolo System Mechanic® — is a patented PC & MAC repair tool & the only program of its kind. It’s not only a registry fix, PC optimizer, or an anti-virus scanner – The iolo System Mechanic® technology reverses the damage done to Windows or Mac, eliminating the need for time-consuming reinstallations & costly technician bills.
It is available for FREE. Although, for some more advanced features & 100% effective fixes you may need to purchase a full license.
If your Clhmotjdxp ransomware issue is still not fixed — don’t hesitate and contact us via email, or a Facebook messenger (the blue ‘bubble’ on the bottom-right of your screen).