How to Remove Clipboard Hijackers to Prevent Financial Loss
Cecil Faron
Issue:A different wallet address whenever I paste my wallet address in my Crypto Exchange Provider.
Hey, I don't know what's going but when I copy my wallet address and try to paste it in my Crypto Exchange Provider, it pastes a different wallet address.
No matter what I do, it does not paste the correct wallet address. Help me please.
Malicious virus known as Clipboard Hijacker is used by cyber thieves to conduct fraudulent bitcoin transactions. This is accomplished by simply swapping bitcoin wallet addresses contained in a victim’s clipboards to those owned by cybercriminals.
They utilize Clipboard Hijacker in this way to steal cryptocurrency from victims that use cryptocurrencies and perform transactions with them. This infection must be removed as soon as possible to avoid potential financial losses.
In operating systems, the clipboard is a cache that stores data temporarily while it is moved (usually, copied) from one location to another. Data copied from a document, for example, are saved in the clipboard to let the users paste it into another, possibly different document.

Cybercriminals employ Clipboard Hijacker in this example to change cryptocurrency wallet addresses that are copied to the clipboard with a different address from other wallets. Many users conduct transactions by manually inputting and copying their wallet addresses to the clipboard.
Then, using Clipboard Hijacker, cyber thieves substitute it with another address, causing unsuspecting victims to send money to them rather than the intended recipient.
People seldom double-check their wallet addresses, allowing cyber thieves to deceive them into completing unintended transfers. Remove Clipboard Hijacker right away to avoid this, make sure that the addresses are correct before conducting cryptocurrency transfers.
Threat Summary
| THREAT NAME | Clipboard Hijacker virus |
| THREAT TYPE | Clipboard hijacking malware. |
| DISTRIBUTION METHOD | Infected spam emails, Bundled software distribution, malicious websites, pop-ups, banner ad and fake Windows update prompts |
| SYMPTOMS | Clipboard Hijacker to steal cryptocurrency from victims who use cryptocurrencies and perform transactions with them. The Clipboard Hijacker changes the cryptocurrency wallet address that is copied to the clipboard with the wallet address of the cybercriminal. |
| REMOVAL | Scan the whole system with iolo System Mechanic all-in-one anti-virus tool or other virus removal tool or manually remove website permissions through the settings in the browser. You can also manually uninstall PUP’s. |
Clipboard Hijacker Distribution Method Summary
Malware like Clipboard Hijacker is typically spread through infected spam emails, Trojans, malicious software downloads, unapproved activation tools, and fraudulent software updating tools. Spam campaigns are used by cyber thieves to send emails with attachments.
In spam emails, most of the infected attachments are Microsoft Office files, executable files and compressed files such as .zip files. They make these attachments appear official and important in the hopes that the recipients will open the attached material.
Trojans, which, once installed on the computer will start to download and install other malicious apps, are also used to disseminate malicious software. Peer-to-peer networks such as torrent clients, eMule, and other tools are examples of questionable download channels. These are used by cyber thieves to disguise malicious files as non-harmful. However, when unknowing victims download and open malicious files, they are infecting themselves with high-risk malware.
Avoid Getting Infected with Any Malware (Including Clipboard Hijackers)
If you receive an email with an attachment or a web link from an unfamiliar, suspicious, or untrustworthy address, do not open it. All applications should be obtained through direct download links from official websites.
Official software developers must give updated functionality or tools to update installed applications or operating systems. If the installed software needs to be activated for a fee, it should not be done with third-party (cracking) tools. These are unlawful and frequently result in malware infections.
Regularly scan your computer with a reliable anti-virus tool and maintain it up-to-date to keep it safe.
Automatically Remove Clipboard Hijackers With iolo System Mechanic
Manual threat cleanup can be a time-consuming and difficult task that would require significant experience when it comes to troubleshooting computer problems. iolo System Mechanic is one of the most trusted and reliable malware removal solutions that is highly recommended for removing threats.

Ways to Manually Remove Clipboard Hijackers
Manual malware removal is difficult, therefore it’s usually best to let antivirus or anti-malware solutions handle it for you.
iolo System Mechanic for Windows is recommended for removing this virus. If you want to manually remove malware, the very first step is figuring out what kind of malware you’re dealing with. Here’s an example of a potentially dangerous program on a victim’s computer:
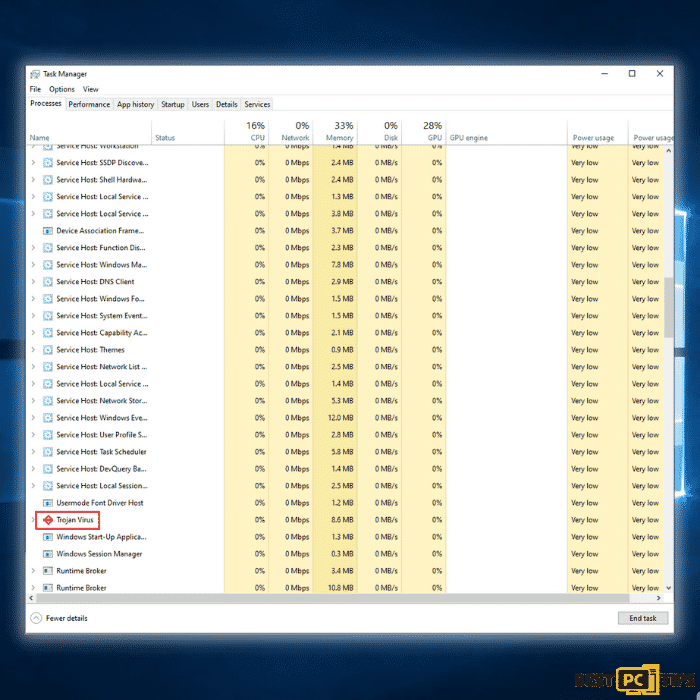
Now that you have determined the name of the threat that has infected your computer, you may now start with the procedure of manually removing threats.
Reboot Your Computer Into Safe Mode
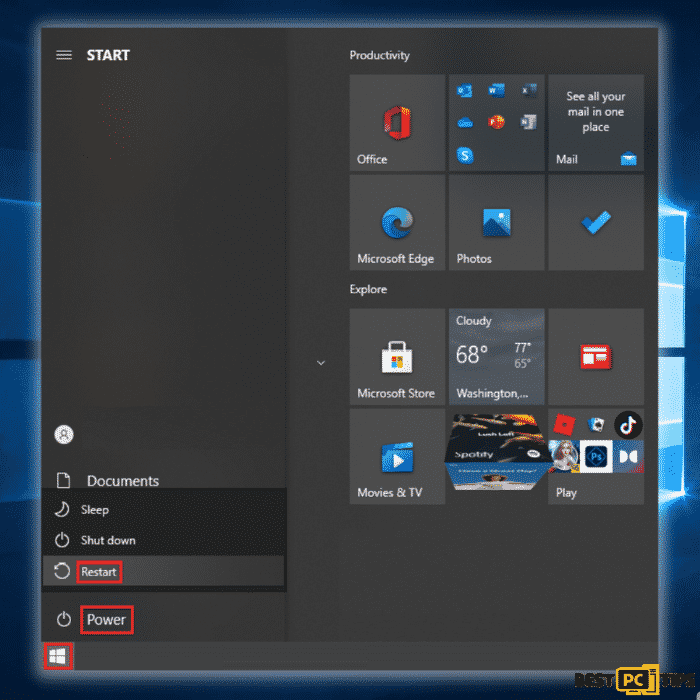
Step 1: Click the “Windows” icon on the taskbar and press the “shift” key on your keyboard, click “Power” and click “Restart”.
Step 2: The computer will reboot in the Troubleshoot screen. Click on the “Advanced Options”.
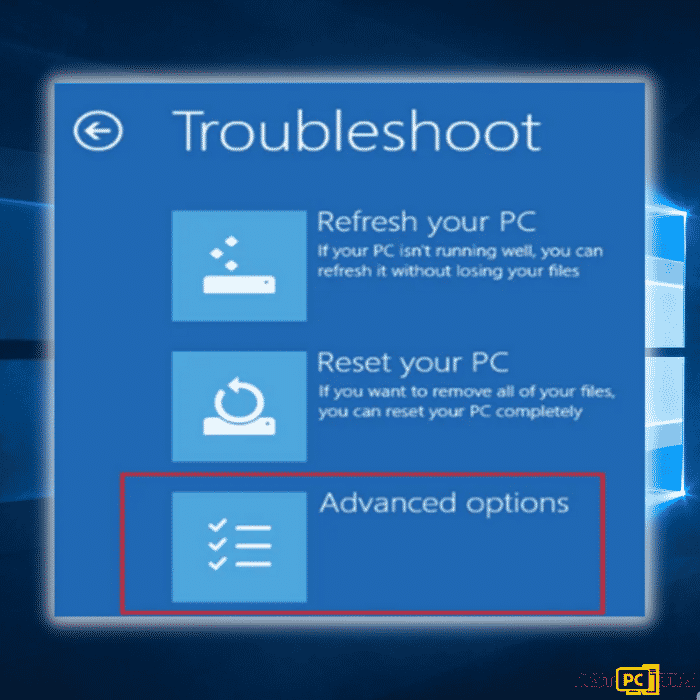
Step 3: Select “Enable Safe Mode with Networking” in option no. 5.
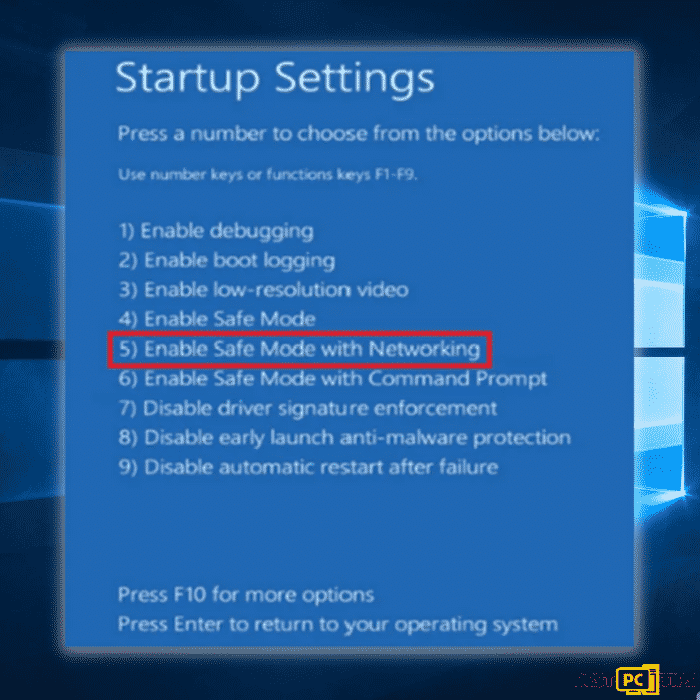
Your computer will now reboot into Safe Mode. It may look different since it will only load important apps and drivers and will disable others.
Disable Unknown Applications in Startup in Task Manager
Step 1: Press the “Ctrl + shift + Esc” keys simultaneously on your keyboard to bring up the Task Manager. Go to the “Startup” tab and look for the Trojan virus in the list of applications and click “Disable”
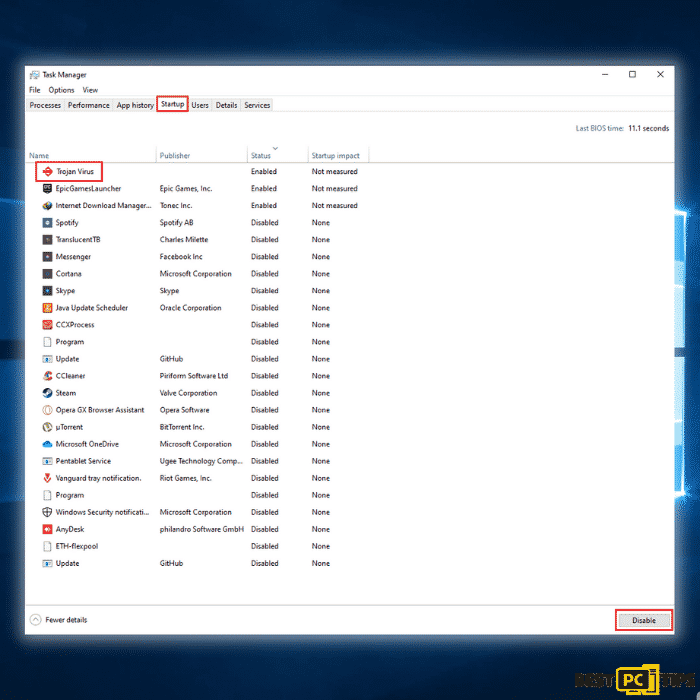
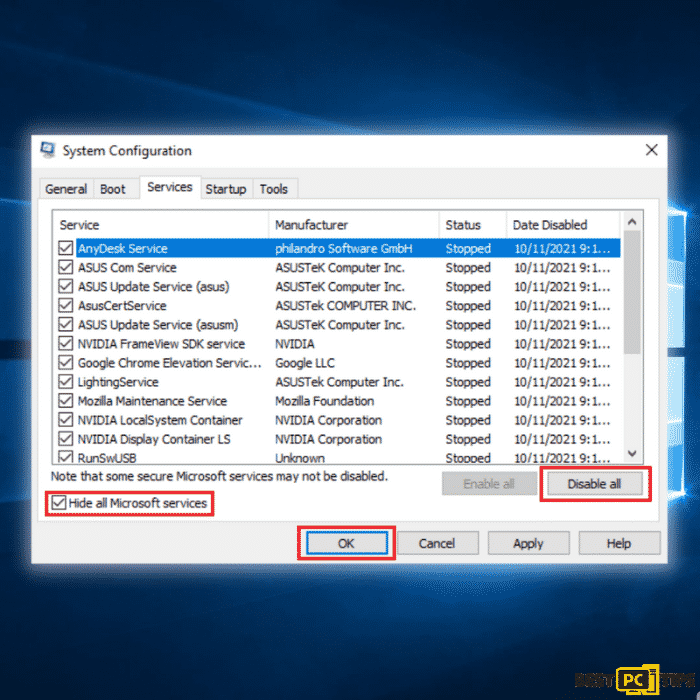
Disable All Non-Microsoft Services (Clean boot)
Step 1: Bring up the run command line by pressing the “Windows” + “R” keys and type in “msconfig” and press “OK”.
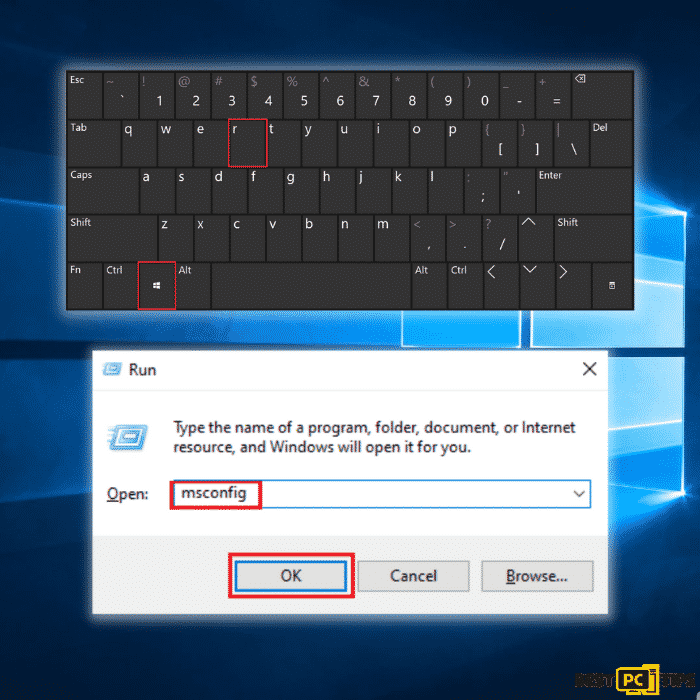
Step 2: In the System Configuration window, click on the “Services” tab and click on “Hide all Microsoft Services”, click “Disable all” and click “OK”
Run a Full System Scan with Your Preferred Anti-Virus Tool
Now that all unnecessary services and background processes have been disabled, your anti-virus tool can go ahead search for the threat without any chances of getting disabled by the threat. You can use the built-in anti-virus tool in Windows 10 but we strongly suggest using iolo System Mechanic as it will not only remove threats, it will also update your system drivers and repair corrupt or missing system files that may have been affected by the infection.
Conclusion
If you would notice, when manually removing online threats such as the Clipboard Hijacker, you will have to perform several steps. If you want to skip all of these, we recommend download iolo System Mechanic to automatically remove threats from your computer.
Offer
iolo System Mechanic® — is a patented PC & MAC repair tool & the only program of its kind. Not only it’s a registry fix, PC optimizer, or an anti-virus/malware remover – The iolo System Mechanic® technology reverses the damage done to Windows or Mac, eliminating the need for time-consuming reinstallations & costly technician bills.
It is available for FREE. Although, for some more advanced features & 100% effective fixes you may need to purchase a full license.
If the Clipboard Hijackers is still not fixed — don’t hesitate and contact us via email, or a Facebook messenger (the blue ‘bubble’ on the bottom-right of your screen).