OMFL Ransomware Removal Guide (Free Instructions)
Rebecca P.
Issue:My computer files have been renamed to ".omfl" and I cannot access them. How can I fix this?
Hi,
all of my PC files have been encrypted with .omfl extension and I cannot access them now.
On top of that, I received a ransom note requiring me to pay $480 (crazy!) to get my files back.
I'm sure there's a way to solve this. Can you please help?
Thank you!
The Omfl Ransomware is a new variant of ransomware from the Djvu Ransomware family. Just like its predecessors, the Omfl ransomware encrypts infected files making them unusable and changes their file extensions. As an example, if the file is named “sample.jpeg” it will be changed to “sample.jpeg.omfl“.
Once the encryption process is complete, the Omfl ransomware will then leave a ransomware on the folders that contains encrypted files that is named “_readme.txt“
As per the message in the ransom note, the criminals behind the Omfl ransomware will only provide the unique key and decryption software once the victim pays them $980 for the full amount or $490 if the victim contacts the criminals within 72 hours.
The worst problem about becoming infected with the Omfl ransomware is that there is currently no known third party decryption tool available and only the cyber criminals themselves have them.
Here’s a screenshot of the ransom note from the people behind the Omfl Ransomware:
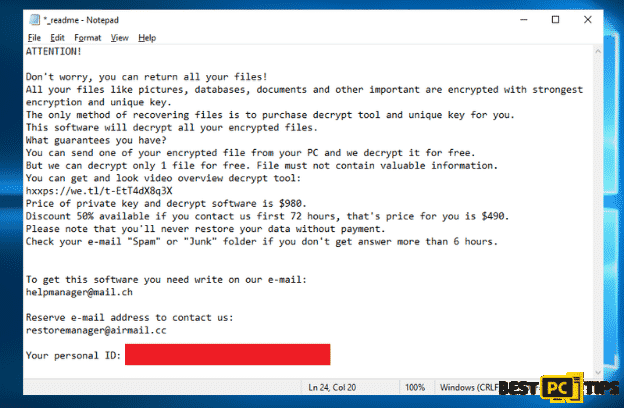
“ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-EtT4dX8q3X
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
[email protected]
Reserve e-mail address to contact us:
[email protected]
Your personal ID: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx “
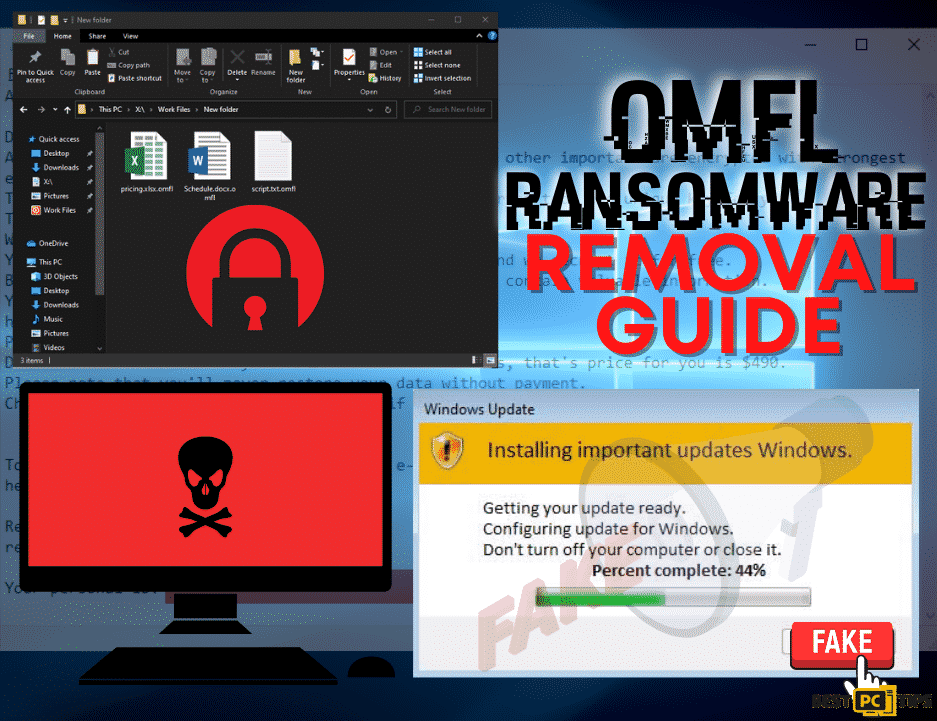
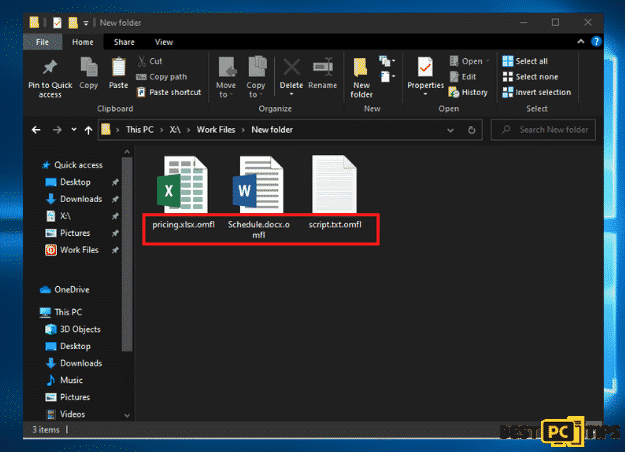
Here’s a screenshot of how infected files look like:
How to Avoid Getting Infected With Omfl Ransomware?
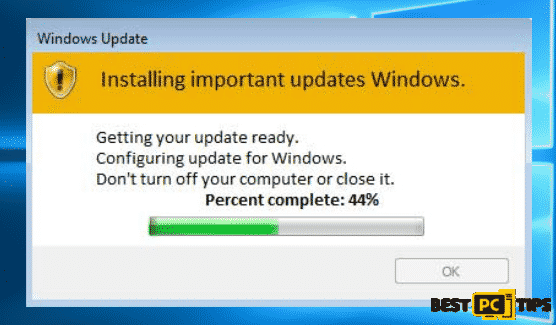
There are multiple reasons as to why a computer gets infected with a virus or a ransomware. One of the most common reasons is if a victim clicks on a fake Windows update or a fake Flash player update. Here is how it may look like:
Aside from clicking on fake updates, viruses may also come from software bundling. This is a intrusive marketing strategy used by cyber criminals to install viruses on a victim’s computer. What happens is that there is a second application that gets installed together with the legitimate software. This software is installed without the user’s permission and knowledge and it then executes commands that open up the computer to other online threats.
Threat Summary
| Threat Name | Omfl Ransomware |
| Type of Threat | Crypto Virus, File Encryptor, Ransomware |
| File Extension | .omfl |
| Ransom Note File Name | _readme.txt |
| Ransom Amount | $980 ($490 if the victim contacts the developers within 72 hours) |
| Contact Details | [email protected] and [email protected] |
| Symptoms | Infected files are encrypted and can no longer be opened and used. The file extensions will also be changed and a ransom note will be left on the folders with infected files. |
| Distribution Methods | Malicious and intrusive ads, software bundling, clicking on email attachments from unknown sources |
| Removal | Manual removal or automatic removal using an anti-virus tool such as iolo System Mechanic |
There are currently 2 active variants of Djvu ransomwares floating around the internet, the old and the new variants. The old variants of the ransomware were developed to encrypt infected files using hard-coded offline keys that will start the encryption once the virus detects that the infected computer is not connected to the internet. Due to this loophole, the decryption tool from Emsisoft is able to successfully decrypt infected files.
However, if you have unfortunately been infected with the newer variant a Djvu ransomware then the Emsisoft application cannot recover the encrypted files.
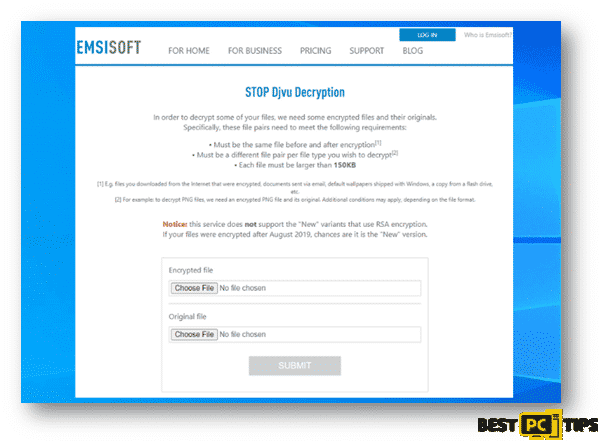
EmsiSoft is currently offering decryption services for users that have been infected with older versions of Djvu ransomwares. Older versions include threats that were developed and distributed before August 2019.
If you’re interested in checking if there’s a possibility to decrypt your infected file, go to to decrypter.emsisoft.com/submit/stopdjvu/.
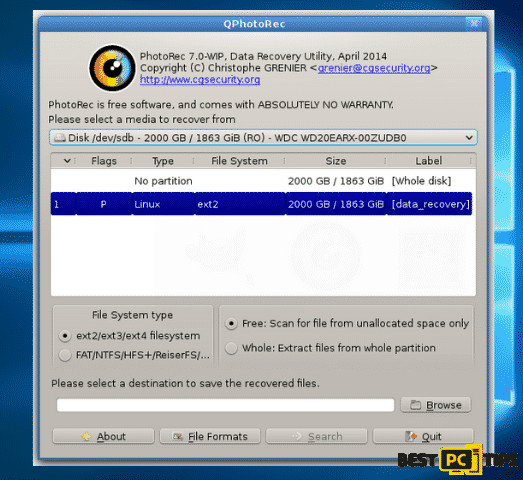
There are also reports from victims that they have successfully restored their files by using the PhotoRec tool from CG Security. You can download the tool by clicking here.
Omfl Ransomware Removal Guide
Manual virus removal may take a lot of time and patience especially if you’re not much technically inclined. However, if you wish to do it automatically, then we suggest you to use a reliable anti-malware tool such as iolo System Mechanic.
iolo System Mechanic is an all-in-one application that not only automatically detect and remove online threats, but it also automatically updates Windows files to make sure your computer runs on its optimum state.
Must Do’s if a There’s a Ransomware Infection
If you determine that your computer has been infected by the RestorFile Ransomware, the first thing to do is to isolate it from the rest of the devices in your network. Doing this first step ensures that the infection will be isolated in one machine and not spread to other devices in the network.
Follow these steps on how to isolate your computer from the network:
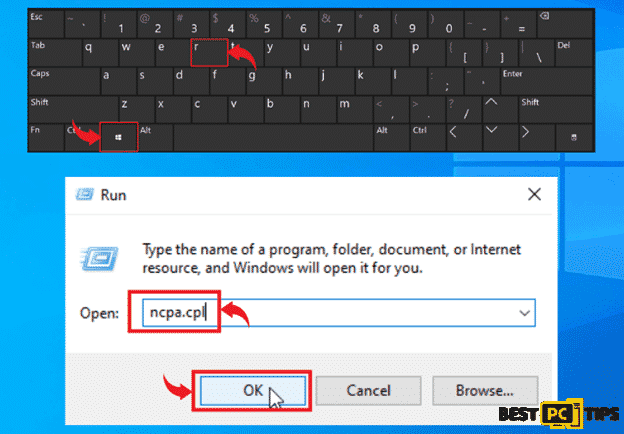
- Disconnect your computer from the network/internet – The easiest way to go about this is to disconnect your computer from the WiFi or unplug the network cable from your machine. You may also follow these steps to do it from the control panel.
- Open the Run Command window by holding down the “Window” key on your keyboard and press the letter “R” and type in “ncpa.cpl” and press enter
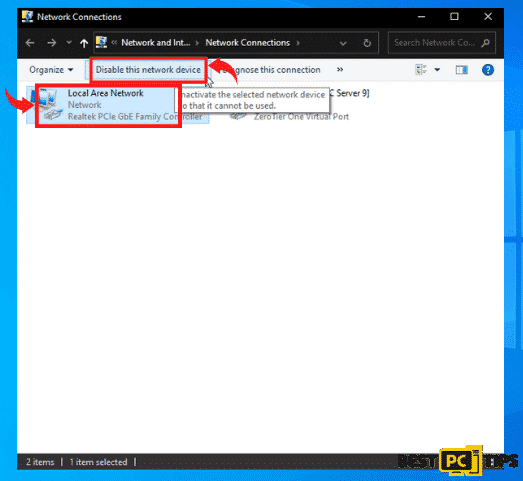
- Click on your “Local Area Network” and click “Disable This Network Device”
- Unplug all connected external storage devices – If you have a flash drive or any external storage devices plugged in to your computer, it is best to safely unplug them so that it will not infect the files on the external device.
You can simply click the “Arrow” that is pointing up beside the clock on the bottom left corner on your desktop, and click on the connected media icons and click on the “Eject” on the external storage device.
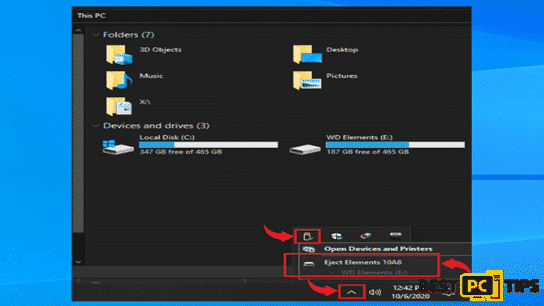
- Logout from all Cloud Storage Accounts – When an infection hits a computer, it will affect all the files in the machine including files in the Cloud Storage. That is why we strongly suggest to disconnect your computer from the internet so that if you do not have the time to logout from the Cloud, at least the infection cannot spread to it through the internet.
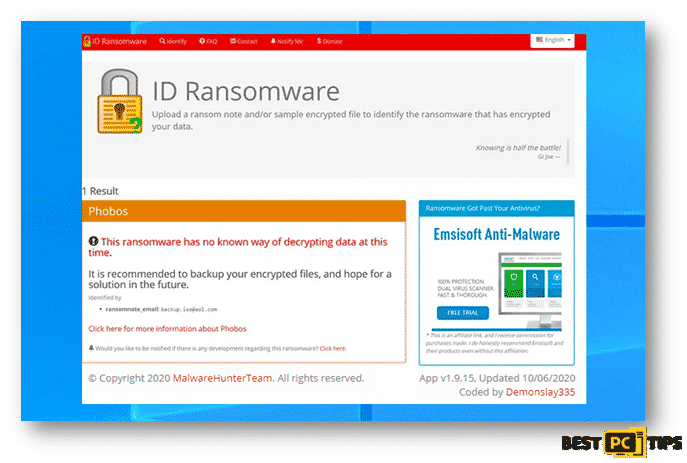
Determining the Name of Ransomware (Is It Really OMFL?)
The next process of determining what ransomware is infecting a system is using the ID Ransomware website. This service can determine most of the currently existing ransomware. The victim only needs to upload an encrypted file or the ransom note. You may go to their website at https://id-ransomware.malwarehunterteam.com/
If ID Ransomware is able to determine what type of ransomware is infecting the machine, it will show this message containing the name of the ransomware.
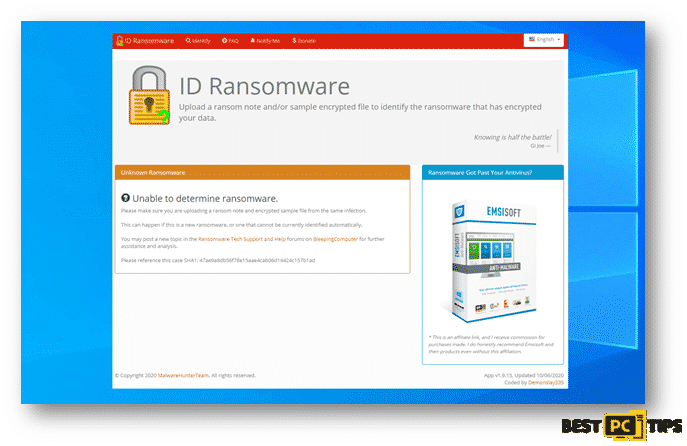
Here’s a screenshot of ID Ransomware not being able to determine what ransomware is infecting the machine.
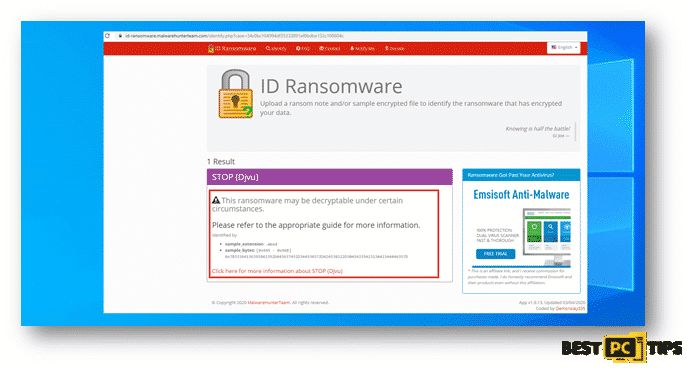
Lastly, here’s a screenshot of ID Ransomware determining the name of the ransomware however, but they do not have the capacity to decrypt the infected files.
Using Reliable Decryption Tools
Although there are ransomware infections such as Phobos and Dharha CrySis that are very difficult to remove and the only way to get rid of it is to contact the developer of the ransomware, there are also other ransomware that can easily be removed by decryption tools that you can find online.
The No More Ransom Project is a free website that works as a search engine for possible decryption tools for ransomware infections. You will only need to upload 1 or 2 encrypted files or the ransom note left by the cyber criminals.

Restoring Files with Recovery Tools
Depending on the severity of the ransomware infection in the system, there are data recovery tools that can recover the infected files. One of the most used tool is the EaseUS Data Recovery Wizard Pro, it supports multiple types of files such as photos, documents, videos, audios, etc.
You can download EaseUS Data Recovery Wizard Pro by going to their website https://www.easeus.com/datarecoverywizardpro/index.htm
Below are steps on how you can use the EaseUS Data Recovery Wizard Pro:
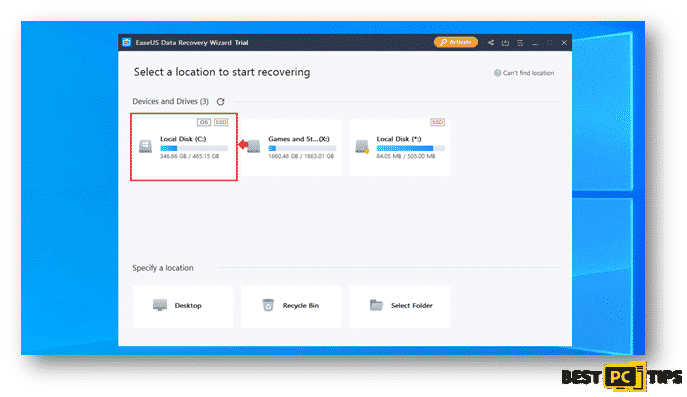
Step 1: How to Perform a Scan
Click on the partition that had wish to have a scan on and it will automatically run the scan. The scan may take a while as it will go through the whole partition.
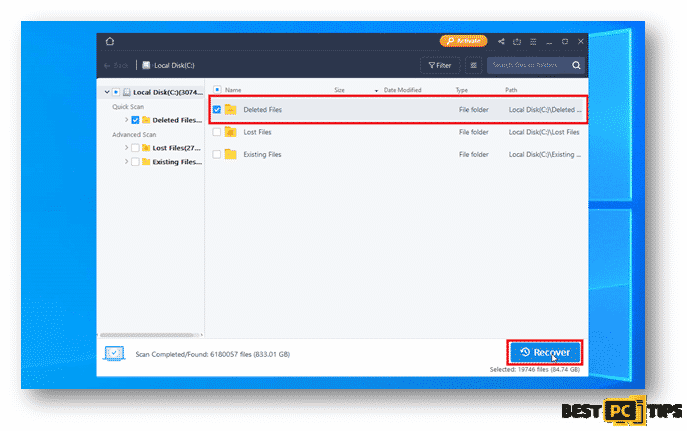
Step 2: Recovering the Discovered Data
Selected your desired folder and click on recover.
Backing Up Your Important Data
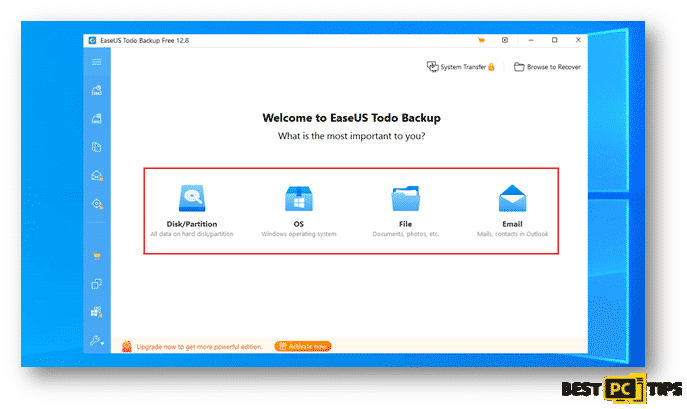
You may also use a software that would automatically back up your files for you such as EaseUS Todo Backup. With EaseUS Todo Backup, you can easily schedule and automatically run your backups. In cases of disastrous files and data loss, EaseUS Todo Backup can also restore your data easily to get your computer working again. You can download EaseUS Todo Backup at https://www.easeus.com/backup-software/.
Select your preferred types of files or data that you wish to do a backup of:
Next step is to select the file path and files that you wish to back up and click on Proceed.
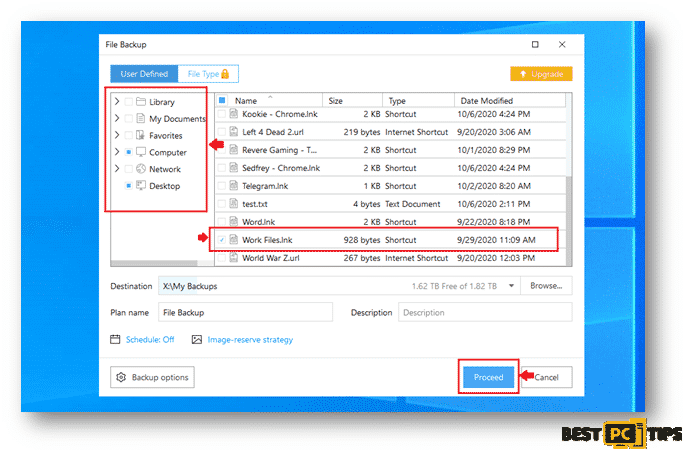
You backed up files will be located on the location that you selected once the backup process is complete.
A Last Few Words of Advice
To be ready for disastrous data loss, it is very important to keep a backup of your important files. It is best to backup your files to an external device or a cloud storage. In this way, you will be able to get a copy of your files just in case your computer gets infected with a virus.
Of course, one of the most important things in keeping your PC safe is having protective software installed. For that purpose we highly recommend iolo System Mechanic. It will prevent various types of malware and ransomware.
Offer
iolo System Mechanic® — is a patented PC & MAC repair tool & the only program of its kind. Not only it’s a registry fix, PC optimizer, or an anti-virus/malware remover – The iolo System Mechanic® technology reverses the damage done to Windows or Mac, eliminating the need for time-consuming reinstallations & costly technician bills.
It is available for FREE. Although, for some more advanced features & 100% effective fixes you may need to purchase a full license.
If your OMFL virus is still not removed — don’t hesitate and contact us via email, or a Facebook messenger (the blue ‘bubble’ on the bottom-right of your screen).